Adrien B
@Int2e_Malware research and threat intel ex #DFIR responder at @Mandiant
Similar User

@stvemillertime

@Wanna_VanTa

@MrDanPerez

@bryceabdo

@kyleehmke

@3dRailForensics

@williballenthin

@MalwareRE

@bkMSFT

@tylabs

@rufusmbrown

@xorhex

@malwaresoup

@matthieu_faou

@BitsOfBinary
Microsoft identified multiple vulnerabilities in the open-source platform OpenVPN, integrated into millions of devices worldwide, which could be exploited to create an attack chain allowing remote code execution (RCE) and local privilege escalation (LPE). msft.it/6014llDIQ
We are looking for a strategic threat intel analyst to join @ESETresearch Interested in cyber-espionage and geopolitics? Apply! ca.linkedin.com/jobs/view/anal…
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack. The issue has been identified, isolated and a fix has been deployed. We…
Welcome to the future of YARA: virustotal.github.io/yara-x/blog/ya…
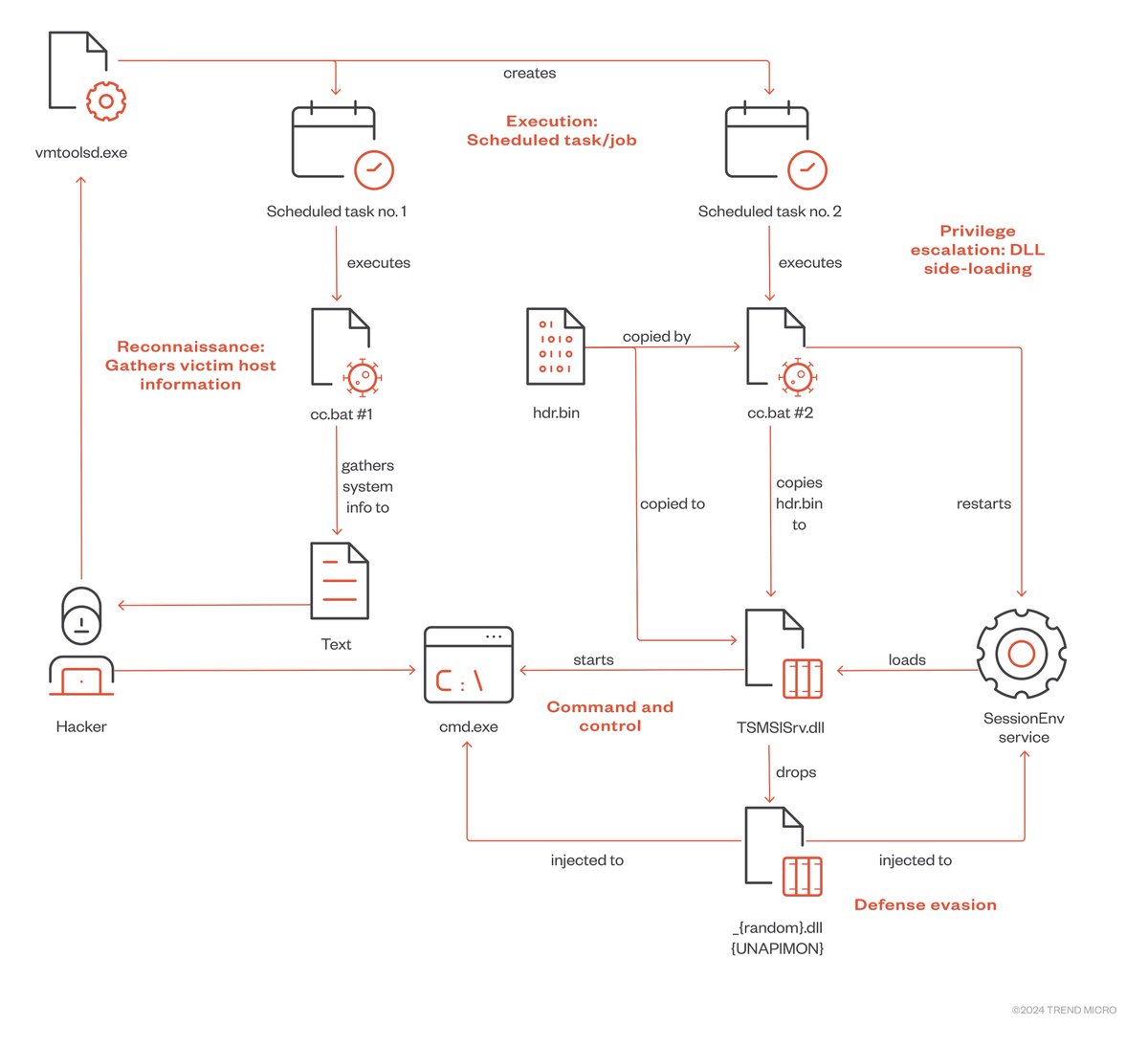
Trend Micro's Christopher So looks into two techniques used by Earth Freybug (a subset of APT41) in the UNAPIMON malware: dynamic-link library hijacking & application programming interface (API) unhooking to prevent child processes from being monitored. trendmicro.com/en_us/research…
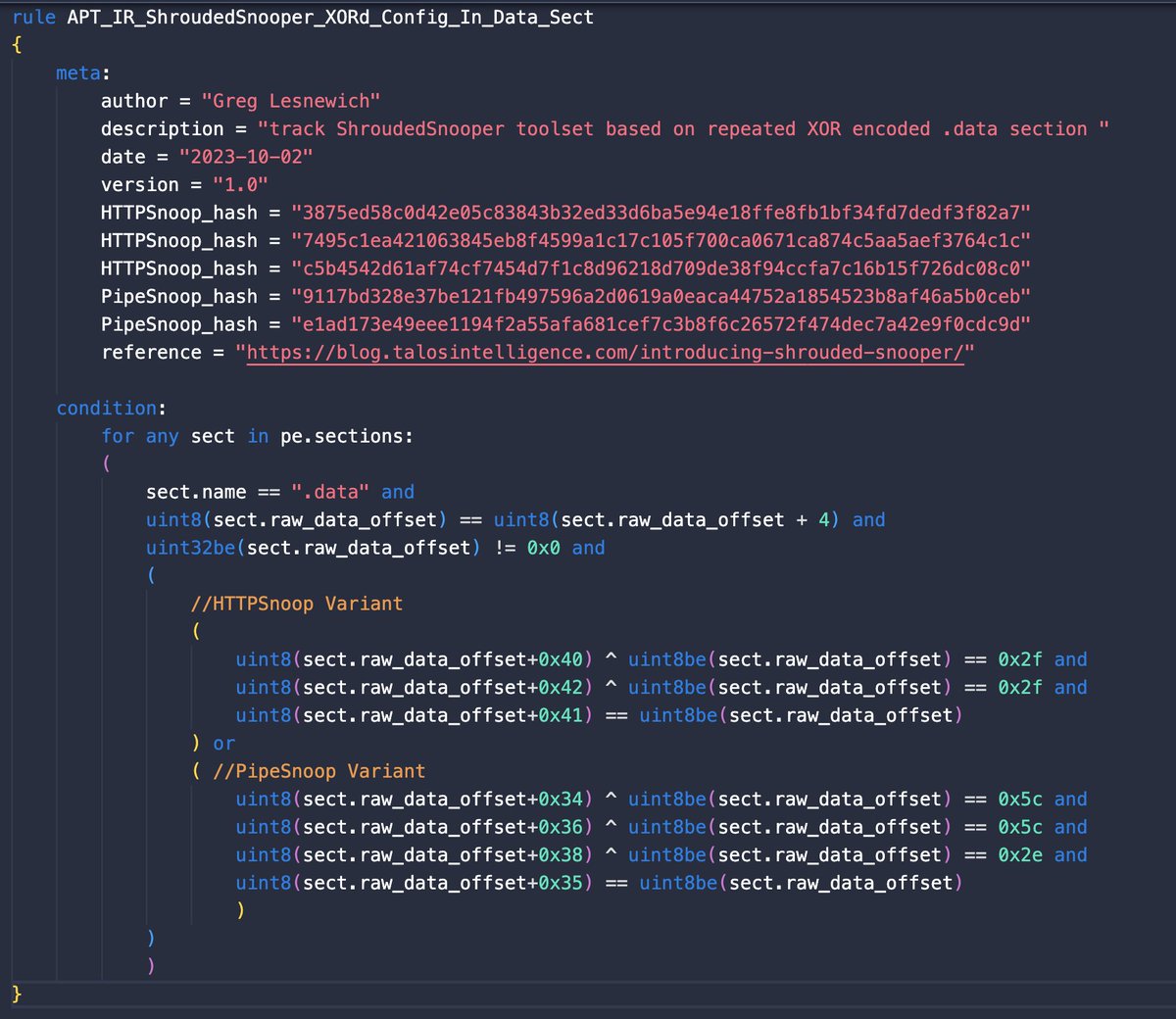
#100DaysofYARA Day 07 - another condition only rule this time looking for the HTTPSnoop and PipeSnoop families found by Talos a little avant garde, but both store config info in the .data section, XOR'd with a 1 byte key following the same structure github.com/100DaysofYARA/…

#100DaysOfYara Day 7: Had an idea for a fun rule that takes PE import checking to the next level. Checks the function call opcodes and verifies that the RVA being called is actually the RVA for the import. Back to OpTriangulation tomorrow (probably). github.com/100DaysofYARA/…
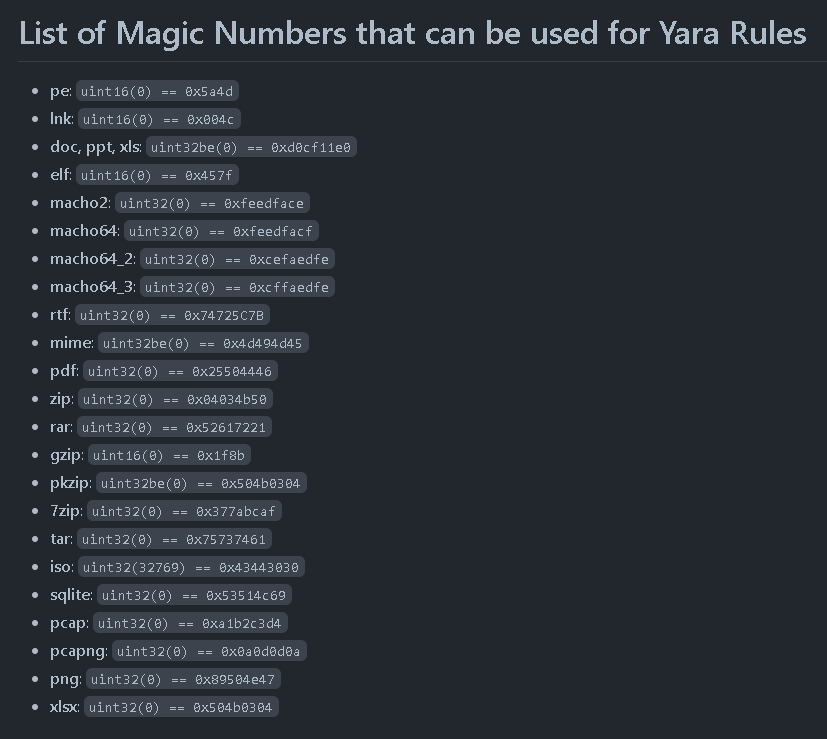
#100DaysOfYara Day 6: Yara can be used to access specific data at a given position. 👇 This feature is often used to identify Magic Numbers (used to determine the file format) to match your rule against a specific file type, such as a PE (0x4D5A), for example. Today, no…
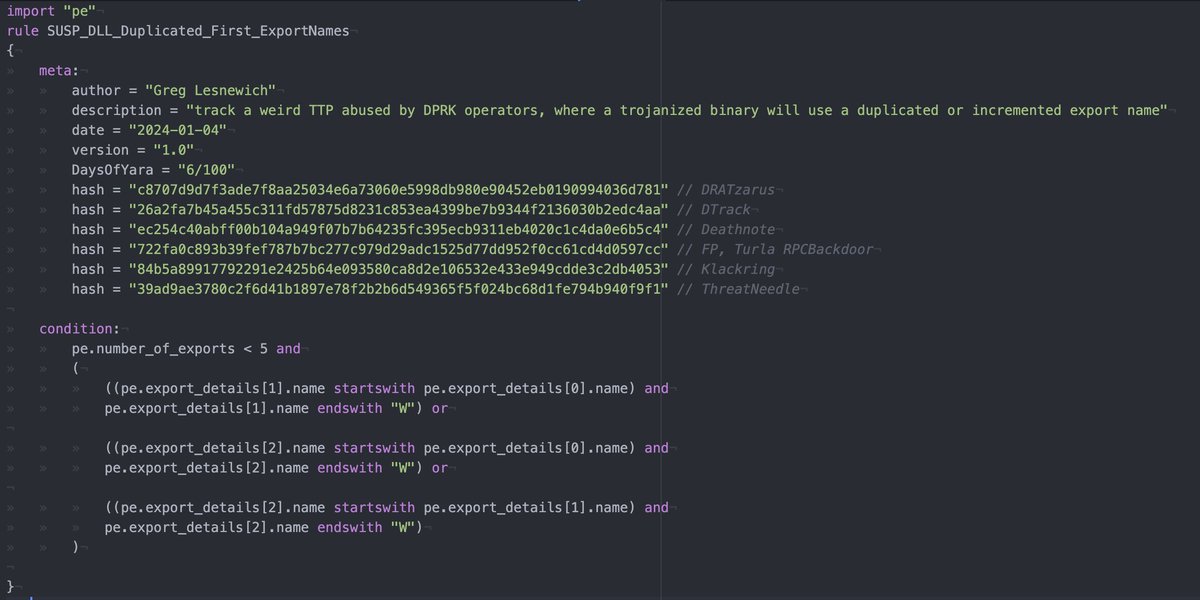
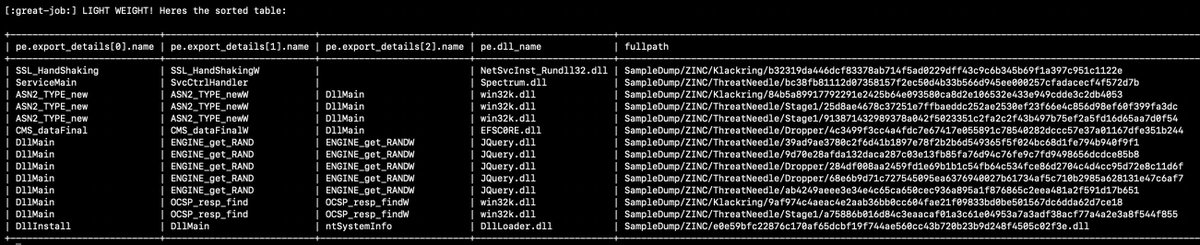
#100DaysofYARA Day 6 sometimes our pals in TA404/Zinc/Temp.HERMIT/Diamond Sleet reuse export names and add a dubya ("W") to the end of the second name. lets create a loose rule looking for duplicates like that! Examples in the second pic thanks to Ronnie Coleman
[1/4] Joined by @vmptrst (@PwC) and @MsftSecIntel, we release attribution information on the Sandman #APT, first revealed at @labscon_io '23. Link 👇 s1.ai/LuaDream
Microsoft has uncovered a supply chain attack by North Korean threat actor Diamond Sleet (ZINC) involving the modification of an installer file from software maker CyberLink. The payload calls back to attacker infrastructure for instructions. Learn more: msft.it/6013iHoQF
Teaser: we're working on a new #YARA module to enhance in-memory matching, allowing detection engineers to craft more precise rules. Stay tuned

A few weeks ago I was honored to speak at @labscon_io . Great people, great talks, great venue. I honestly could not suggest any improvements except something closer to CET timezone!
Check this Microsoft x PwC research collab, coming to #LABScon23 labscon.io/speakers/adrie… labscon.io/speakers/bendi…
Microsoft has identified targeted attacks against the defense sector in Ukraine and Eastern Europe by the threat actor Secret Blizzard (KRYPTON, UAC-0003) leveraging DeliveryCheck, a novel .NET backdoor used to deliver a variety of second stage payloads. msft.it/6019gfoYU
CERT-UA in collab w/ @MsftSecIntel investigated UAC-0024 (susp. #Turla) using CAPIBAR & KAZUAR to target UA GOV entities. Details: cert.gov.ua/article/5213167 (UA only)
We’re sharing more details from our investigation of the Storm-0558 campaign that targeted customer email, including our analysis of the threat actor’s techniques, tools, and infrastructure, and the steps we took to harden systems involved: msft.it/6017g26HL
Very interesting sample: virustotal.com/gui/file/71c87… Fake survey for company FM Global iso -> local web server -> aspx -> sRDI shellcode -> unknown C++ backdoor Uses ChaCha and djbhash, shopping disguise (post to c2/orders, CARTSTATE, shopping_cart cookie name)
Volt Typhoon, a Chinese state-sponsored actor, uses living-off-the-land (LotL) and hands-on-keyboard TTPs to evade detection and persist in an espionage campaign targeting critical infrastructure organizations in Guam and the rest of the United States. msft.it/6019gj8eH
Today we are highlighting an actor we are tracking as Volt Typhoon. This activity is targeting US and Guam critical infrastructure. Volt Typhoon has been observed mostly living off the land during our investigations.
Volt Typhoon, a Chinese state-sponsored actor, uses living-off-the-land (LotL) and hands-on-keyboard TTPs to evade detection and persist in an espionage campaign targeting critical infrastructure organizations in Guam and the rest of the United States. msft.it/6019gj8eH
United States Trends
- 1. Jake Paul 989 B posts
- 2. #Arcane 224 B posts
- 3. Jayce 49,6 B posts
- 4. #SaturdayVibes 2.987 posts
- 5. Good Saturday 25,5 B posts
- 6. Serrano 1.346 posts
- 7. #saturdaymorning 2.034 posts
- 8. Vander 16,1 B posts
- 9. #SaturdayMotivation 2.018 posts
- 10. maddie 20,4 B posts
- 11. #HappySpecialStage 94 B posts
- 12. Pence 81,3 B posts
- 13. Isha 38,2 B posts
- 14. Jinx 108 B posts
- 15. WOOP WOOP 1.373 posts
- 16. Rizwan 8.551 posts
- 17. John Oliver 14,2 B posts
- 18. He's 58 31,3 B posts
- 19. Father Time 10,8 B posts
- 20. Super Tuna 24,7 B posts
Who to follow
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Van
Van
@Wanna_VanTa -
 Dan Perez
Dan Perez
@MrDanPerez -
 Bryce
Bryce
@bryceabdo -
 Kyle Ehmke
Kyle Ehmke
@kyleehmke -
 nick
nick
@3dRailForensics -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Ramin Nafisi
Ramin Nafisi
@MalwareRE -
 bk (Ben Koehl)
bk (Ben Koehl)
@bkMSFT -
 Tyler McLellan
Tyler McLellan
@tylabs -
 Rufus
Rufus
@rufusmbrown -
 avallach (@[email protected])
avallach (@[email protected])
@xorhex -
 Andy Moore
Andy Moore
@malwaresoup -
 __mat__
__mat__
@matthieu_faou -
 John
John
@BitsOfBinary
Something went wrong.
Something went wrong.