BarryV
@BarryVShow me, don't tell me -- Opinions are my own and do not represent those of my employer
Similar User

@3dRailForensics

@MrDanPerez

@stonepwn3000

@Wanna_VanTa

@williballenthin

@mittypk

@rufusmbrown

@bkMSFT

@siedlmar

@bwithnell

@tylabs

@x04steve

@SElovitz

@stevemk14ebr

@tiskimber
Don’t forget you @virustotal collection with #APT45 iocs is available here virustotal.com/gui/collection…
Member Turla signing Javascript malware? Serial Number: cd:fb:13:a3:e6:49:ec:c5:df:95:db:88:ca:c1:3f:fb
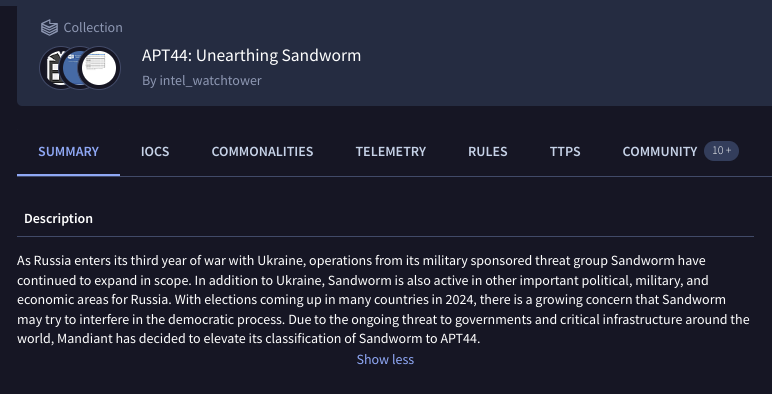
One really cool thing we've implemented in this iteration of our graduation process is leveraging @virustotal's Collections to provide IOCS to the community for #APT44 - check those out here: virustotal.com/gui/collection…
Today, Mandiant is sharing research on the GRU’s Disruptive Playbook, drawn from insights into GRU’s full-spectrum cyber operations in Ukraine over the past year. mandiant.com/resources/blog…
Head of Rubrik Zero Labs @stonepwn3000 recently talked to @joetidy of @BBCNews about why it is so rare to hear about Western #CyberAttacks and hacking teams and how the narrative of who the good guys and bad guys are in cyber-space is changing 👇 rbrk.co/43WGGsd
Really excited to see the culmination of some amazing work from some amazing people get released today. A report from @Google TAG, with contributions from friends at @Mandiant, on cyber activity related to the war in Ukraine. @t_gidwani @ShaneHuntley blog.google/threat-analysi…
capa v5.0.0 is out: major improvements for .NET binary analysis, 150 new/updated rules, caching to improve performance standalone and in the IDA Pro plugin, better ELF OS detection, and a lot more. github.com/mandiant/capa/… VirusTotal integration updates are next!
If you have any intel analysis or threat hunting roles, please reach out to @PhreakingGeek You'd be hard-pressed to find anyone more passionate about chasing adversaries than he is. I am broken-hearted to have lost him, but I know he'll make a great impact on a new team.
We welcome @Mandiant's CAPA and GoReSym to our malware analysis suite. CAPA provides valuable TTPs, and GoReSym produces all kind of metadata to analyse GO samples: blog.virustotal.com/2023/01/mandia…
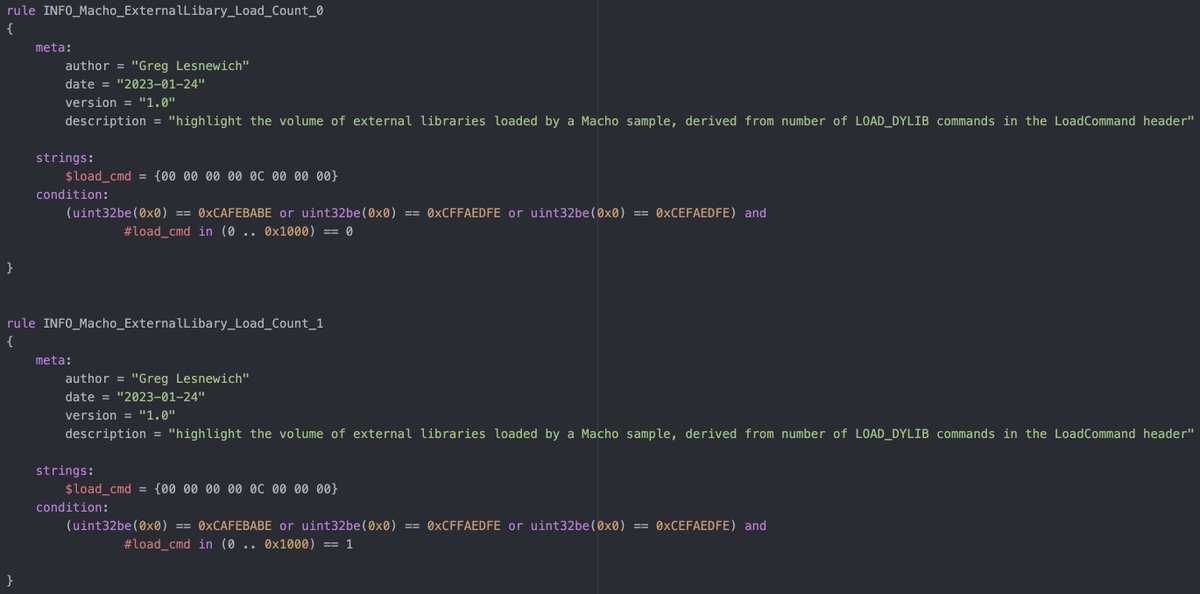
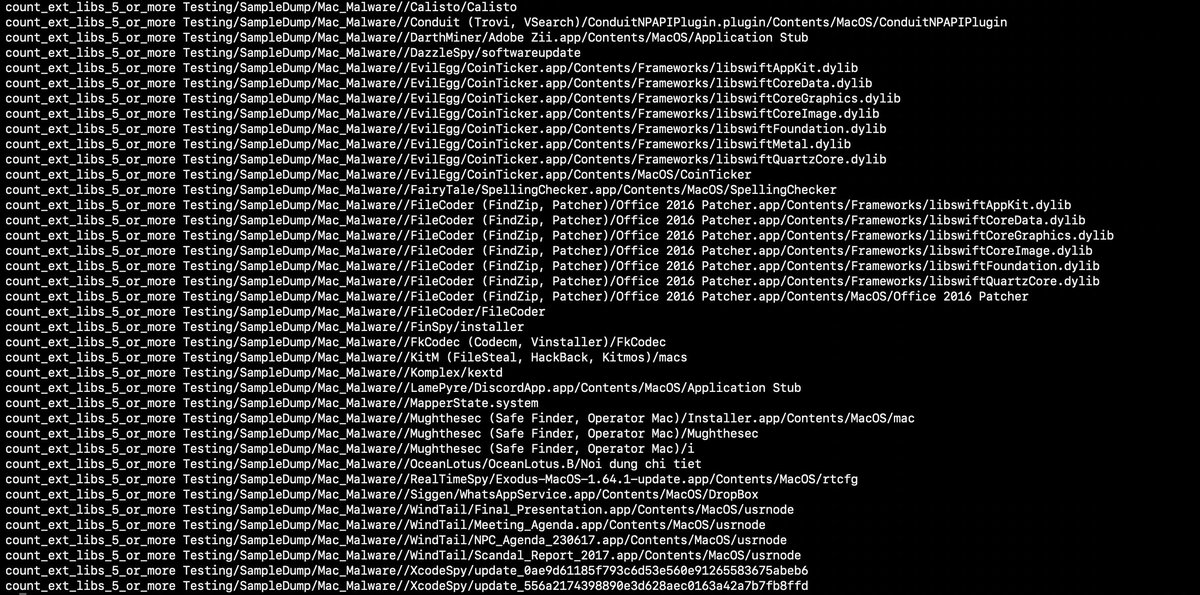
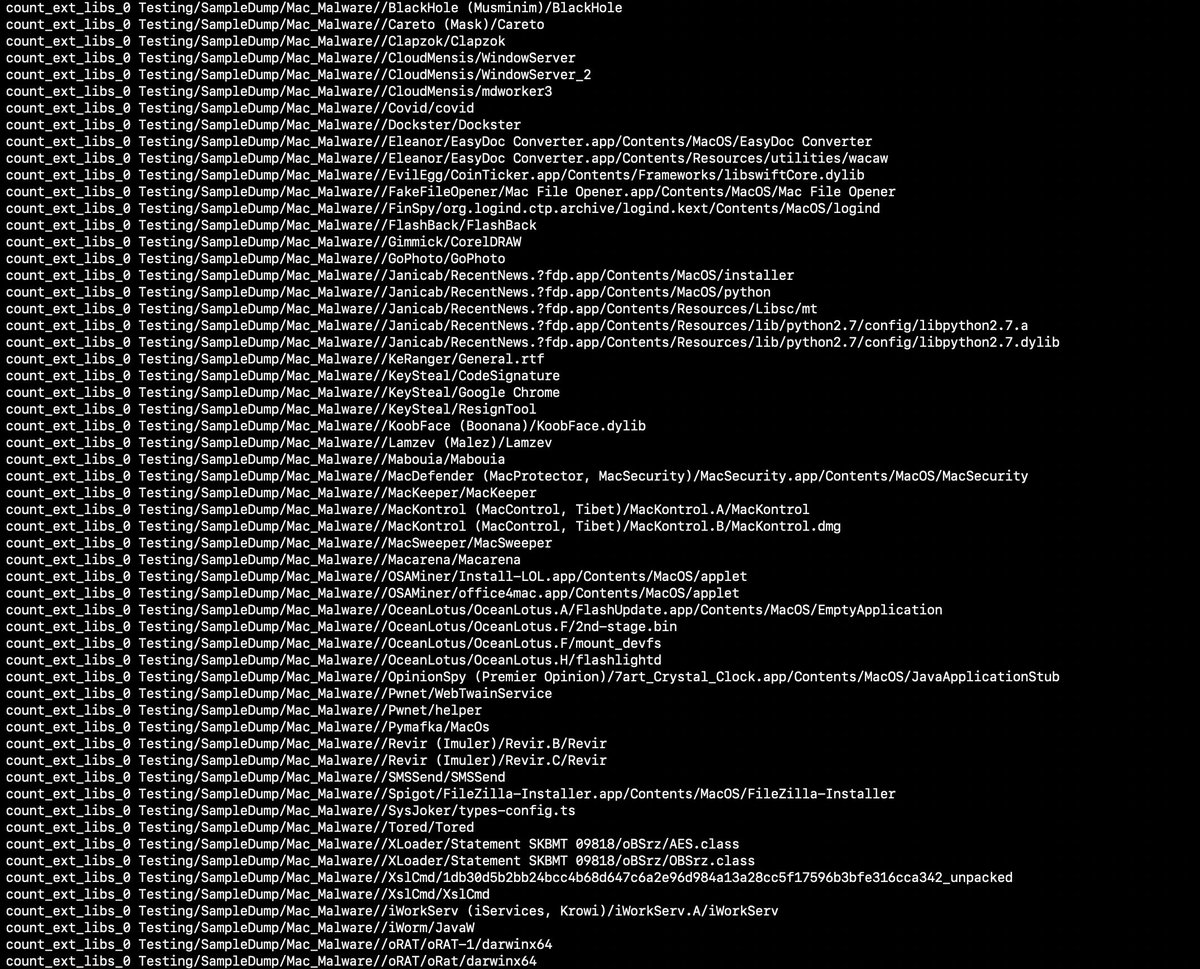
#100DaysofYARA tons of tasty info can be pulled from Macho headers, especially Load commands! Lets get a generic count of LOAD_DYLIB commands to quantify the amount of external libraries are used - no idea if any # is suspicious github.com/100DaysofYARA/…
Mandiant Blog - Turla: A Galaxy of Opportunity mandiant.com/resources/blog… This is Mandiant’s first observation of suspected Turla targeting Ukrainian entities since the onset of the invasion.
In September 2022 Mandiant Managed Defense detected data staging and exfiltration at a Ukrainian organization. Digging into this incident, we discovered QUIETCANARY (aka Tunnus), a suspected Turla Team backdoor, was the source.
What's the technical term for when you've absorbed so much technical debt you're spending all your time addressing support issues rather building?
If we’re gonna haggle/argue over terminology can it please be thrunt.
Likely Russian actor distributed trojaned copies of Windows OS: mandiant.com/resources/blog…
Mandiant observed a POORTRY sample signed with a Microsoft Windows Hardware Compatibility Authenticode signature. Further analysis led to a larger investigation into malicious drivers signed via the Windows Hardware Compatibility Program. 😱🌶️🔥 mandiant.com/resources/blog…
New from @SentinelOne and @Mandiant: Targeted Attacks Leverage Signed Malicious Microsoft Drivers: 🟣 s1.ai/signed-ms 🟣 mandiant.com/resources/blog…
United States Trends
- 1. $CUTO 7.540 posts
- 2. $CATEX N/A
- 3. $XDC 1.162 posts
- 4. DeFi 105 B posts
- 5. #Caturday 6.932 posts
- 6. GAME DAY 12,5 B posts
- 7. Good Saturday 33,5 B posts
- 8. #saturdaymorning 2.794 posts
- 9. Jayce 7.760 posts
- 10. #SaturdayVibes 4.206 posts
- 11. #Arcane 20,8 B posts
- 12. Pence 85,7 B posts
- 13. #MSIxSTALKER2 5.091 posts
- 14. Senior Day 2.714 posts
- 15. McCormick-Casey 26,3 B posts
- 16. $XRP 91,3 B posts
- 17. Pennsylvania Democrats 115 B posts
- 18. Tyquan Thornton N/A
- 19. Fetterman 41,5 B posts
- 20. Mel Tucker N/A
Who to follow
-
 nick
nick
@3dRailForensics -
 Dan Perez
Dan Perez
@MrDanPerez -
 Steve Stone
Steve Stone
@stonepwn3000 -
 Van
Van
@Wanna_VanTa -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Mathew
Mathew
@mittypk -
 Rufus
Rufus
@rufusmbrown -
 bk (Ben Koehl)
bk (Ben Koehl)
@bkMSFT -
 ⚛️ Marcin Siedlarz
⚛️ Marcin Siedlarz
@siedlmar -
 bubbles
bubbles
@bwithnell -
 Tyler McLellan
Tyler McLellan
@tylabs -
 Aaron Stephens
Aaron Stephens
@x04steve -
 Steve Elovitz
Steve Elovitz
@SElovitz -
 Steve Eckels
Steve Eckels
@stevemk14ebr -
 Kimberly
Kimberly
@tiskimber
Something went wrong.
Something went wrong.