Similar User

@CorbridgeMax

@namazso

@JUMPSEC

@shubakki

@d_tranman

@zodiacon

@0xthirteen

@djhohnstein

@anthemtotheego

@__mez0__

@peterwintrsmith

@j0hn__f

@Weasel_Sec

@0xLegacyy

@wle702
I'm speaking at BSides London tomorrow morning @HackingDave but I have a feeling people may be thinking they are coming to see you 🤣. I'm forever disappointing people whenever I join a new Discord server or do an event! 😊

In his latest blog, @chudyPB covers a pre-auth Arbitrary File Deletion vulnerability he discovered in the SolarWinds Access Rights Manager (ARM). It may not sound exciting, but it can lead to an LPE on domain-joined Windows machines. Read the details at zerodayinitiative.com/blog/2024/12/1…
Want to run roadrecon, but a device compliance policy is getting in your way? You can use the Intune Company Portal client ID, which is a hardcoded and undocumented exclusion in CA for device compliance. It has user_impersonation rights on the AAD Graph 😃
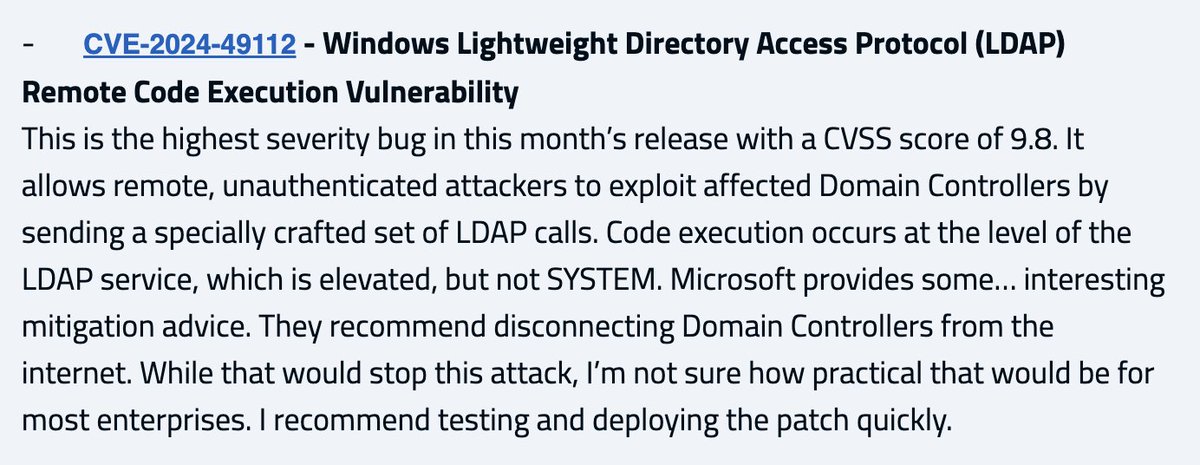
Unauthenticated Remote Code Execution (RCE) on Domain Controllers (DC). It does not get worse than that. Probably will be included in #ransomware campaigns. Any technical analysis of CVE-2024-49112 published? CC: @gentilkiwi @harmj0y @_wald0
I am excited to share with you my latest research - "DCOM Upload & Execute" An advanced lateral movement technique to upload and execute custom payloads on remote targets Forget about PSEXEC and dive in! deepinstinct.com/blog/forget-ps… github.com/deepinstinct/D…
Gotta love 0-day. Gonna be a wild night! Cleo software CVE-2024-50623 is being actively exploited in-the-wild and fully-patched systems running 5.8.0.21 are still exploitable. 💥 Dropped some details to Reddit: reddit.com/r/sysadmin/com… Blog coming soon. ⚡

👀 we’ve watched APTs recently ravage lawful interception systems, and wanted our own capabilities… Join us on a journey today into Mitel’s MiCollab - that originally started to reproduce CVE-2024-35286, and quickly unravelled into more… labs.watchtowr.com/where-theres-s…
But you know what's even better? KrbRelay also works from a low privileged users perspective! 🔥🔥🔥

Finally I was finally able to reproduce RemotePotat0 from @splinter_code and @decoder_it which still works perfectly fine when relaying against SMB and choosing the correct CLSID :-) Only LDAP relaying it patched and not possible anymore. Super late but ¯\_(ツ)_/ ¯🤪


This week is a foray into the world of disaster recovery, and the reasons that often prevent organisations from creating and battle hardening their Business Continuity Plans (BCPs): labs.jumpsec.com/bcp-as-easy-as…
🔥 Initial Access Guild registration is now open! 🔥 Offensive Engineers, let us unite in a trusted, vetted community! I invite you to a curated closed Discord server, where ideas can be exchanged safely. ☢️ binary-offensive.com/guild ☢️ See you inside fellow Breacher!

Anyone else spot that linpeas.sh is looking to extract information from your system? This site is not linked to the original author's version of Linpeas by the way.

Oh, you didn't know? Cool kids are now relaying Kerberos over SMB 😏 Check out our latest blogpost by @hugow_vincent to discover how to perform this attack: synacktiv.com/publications/r…
It’s always awesome when we (@CISAGov) gets to release a red team report that we worked on, and today is another one of those days! Go check out our latest report and hopefully you can apply some of the same lessons to your environment! cisa.gov/news-events/cy…
in today's 'no way, is it real?' we found out that Palo Alto's PAN-OS CVE-2024-0012 and CVE-2024-9474 were the equivalents of saying 'turn off auth and give me a shell'. Enjoy! labs.watchtowr.com/pots-and-pans-…
hop skip jump over to our latest blog post - analysing Fortinet's FortiJump CVE-2024-47575, FortiJump-Higher (we love this name😄) and beyond (PoC included) labs.watchtowr.com/hop-skip-forti…
Back by popular demand, I wrote a second part blog post on the many defense mechanisms phishing kits are using to avoid detection. This second part dives deep on one specific strategy - preventing detection of commonly cloned login pages e.g. Microsoft pushsecurity.com/blog/how-aitm-…
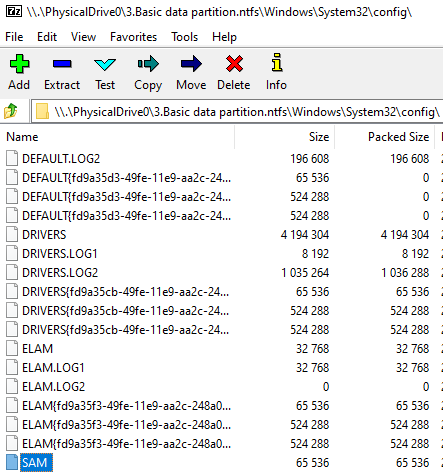
On related note, did you know, that 7z (running as admin), can browse to "PhysicalDrive0" (so \\.\PhysicalDrive0\3.Basic data partition.ntfs\Windows\System32\config\) and copy file from there? SAM is not locked, AV/EDR don't seem to give a damn :)
Hey @l4p0lis, remember bashing our heads against a wall trying to develop that BOF and wondering how anyone ever did it? We could’ve done with this back then, looks awesome
So @freefirex2 has been working hard and this should be live in the next 30-45 days.

United States Trends
- 1. Josh Allen 40 B posts
- 2. Lions 106 B posts
- 3. Bills 136 B posts
- 4. Josh Jacobs 5.829 posts
- 5. Dan Campbell 8.238 posts
- 6. Colts 32,7 B posts
- 7. #EarthMeta 1.768 posts
- 8. #GoPackGo 4.853 posts
- 9. $EMT 4.303 posts
- 10. Eagles 96,5 B posts
- 11. Seahawks 18,9 B posts
- 12. Steelers 74,2 B posts
- 13. #YellowstoneTV 3.545 posts
- 14. #RHOP 4.005 posts
- 15. Broncos 40,2 B posts
- 16. Chargers 23,6 B posts
- 17. Jalen 41,6 B posts
- 18. Buffalo 23,6 B posts
- 19. #OnePride 11,3 B posts
- 20. Goff 14,4 B posts
Who to follow
-
 maxicorbs
maxicorbs
@CorbridgeMax -
 namazso
namazso
@namazso -
 JUMPSEC
JUMPSEC
@JUMPSEC -
 bakki
bakki
@shubakki -
 Dylan Tran
Dylan Tran
@d_tranman -
 Pavel Yosifovich
Pavel Yosifovich
@zodiacon -
 Steven
Steven
@0xthirteen -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 Shawn
Shawn
@anthemtotheego -
 ☠️ Brandon
☠️ Brandon
@__mez0__ -
 Peter Winter-Smith
Peter Winter-Smith
@peterwintrsmith -
 john fitzpatrick
john fitzpatrick
@j0hn__f -
 Weasel Sec
Weasel Sec
@Weasel_Sec -
 Jord
Jord
@0xLegacyy -
 hoodie_sec
hoodie_sec
@wle702
Something went wrong.
Something went wrong.










































































































