Ramiro Molina
@rammolinaComputer Engineer. Pentester.
Similar User

@Omkar7505

@ksandesh1996

@MerajusMd

@BharadwajDj

@realJuanArias

@Dolphin01684386

@Paubolivars

@mbidyeran

@01dguy

@macaordenavia
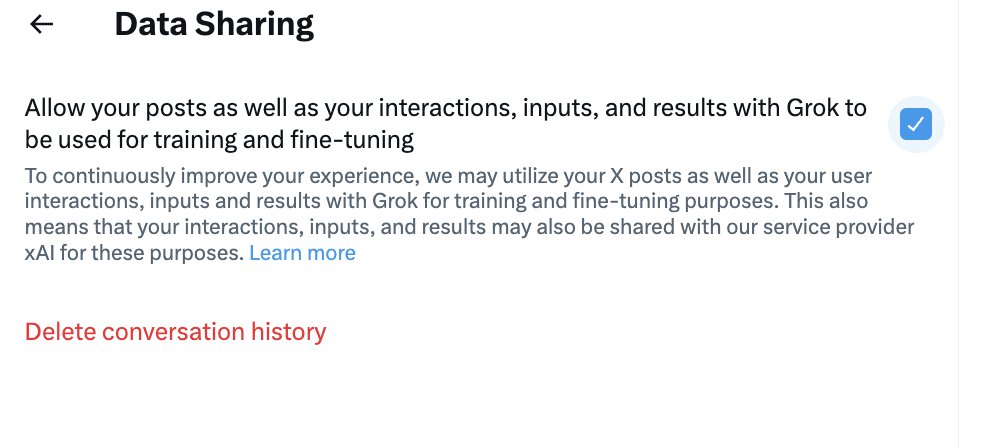
Without notice, X has opted all users into training its "Grok" AI Model. To turn off this setting and stop your "posts, interactions, inputs, and results" from being used for training and fine-tuning Grok, visit x.com/settings/grok_… and uncheck the checkbox.
Leaked footage of CrowdStrike's legal department this morning
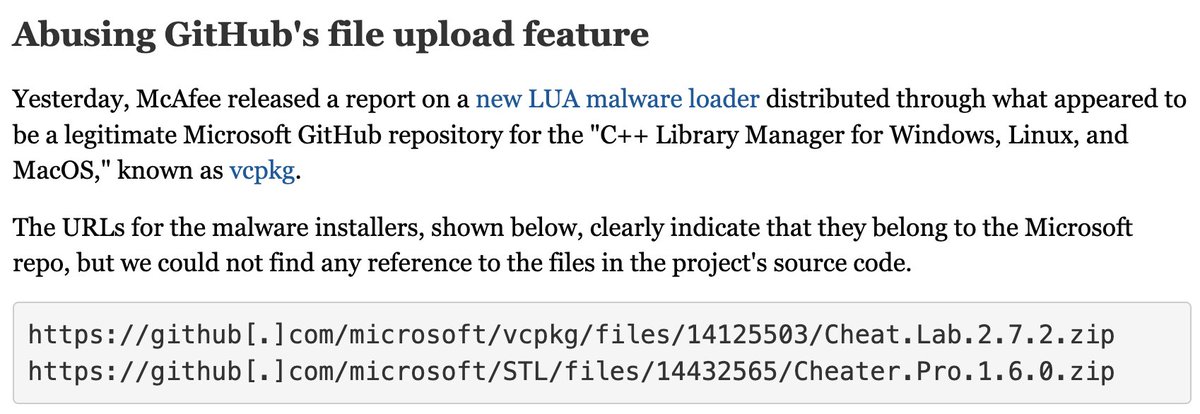
A GitHub flaw lets attackers upload executables that appear to be hosted on a company's official repo, such as Microsoft's—without the repo owner knowing anything about it. The following URLs, for example, make it seem like these ZIPs are present on Microsoft's source code repo:…
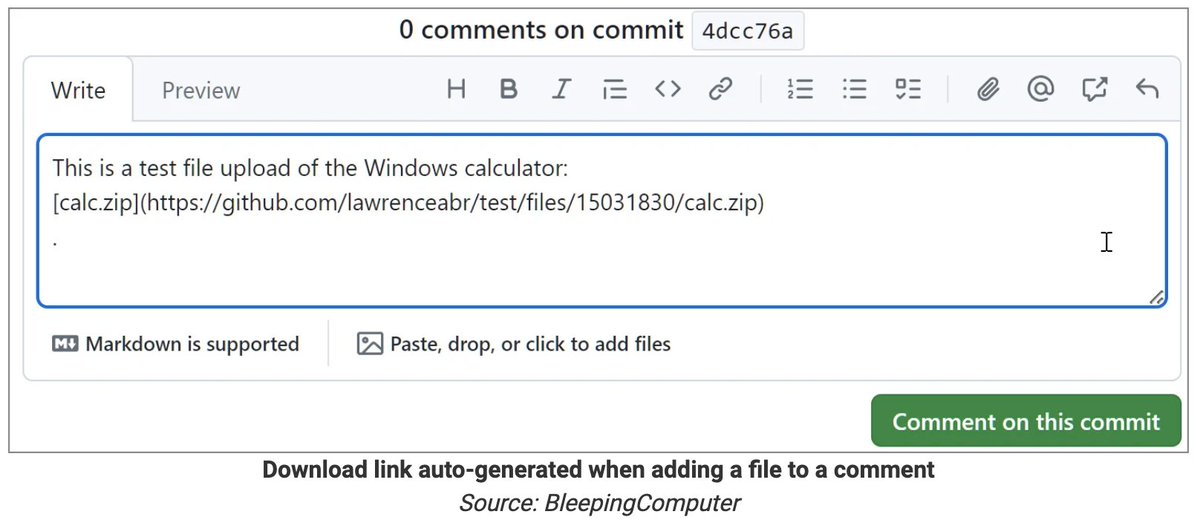
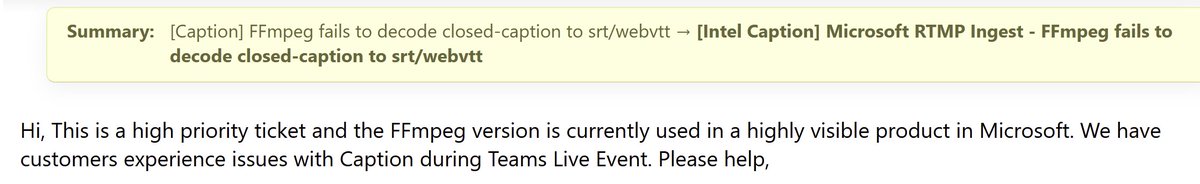
The xz fiasco has shown how a dependence on unpaid volunteers can cause major problems. Trillion dollar corporations expect free and urgent support from volunteers. @Microsoft @MicrosoftTeams posted on a bug tracker full of volunteers that their issue is "high priority"
[#HackTip ⚒] Looking for a legitimate way of achieving #persistence on Windows? How about #AnyDesk silent deployment? 😉

The xz package, starting from version 5.6.0 to 5.6.1, was found to contain a backdoor. The impact of this vulnerability affected Kali between March 26th to March 29th. If you updated your Kali installation on or after March 26th, it is crucial to apply the latest updates today.
New: inside the underground site where "neural networks" churn out fake IDs - I tested, made two IDs in minutes - used one to successfully bypass the identity verification check on a cryptocurrency exchange - massive implications for crime, cybersecurity 404media.co/inside-the-und…

The attackers were very sophisticated. They were drinking expensive wine and listening to classical music while they exfiltrated the data.
Next beacon name be like :

This is utter crap for AV advice from Microsoft It's bad enough that Teams still runs in a user-writable location (AppData), but lets combine that with AV exclusions AND not specify path based vs process based exclusions I would highly advise against path based exclusions here
🔥 New blogpost 🔥 Running PEs inline without a console. You now can, for example, run PowerShell in CobaltStrike and obtain its output without spawning any process (including conhost.exe) coresecurity.com/core-labs/arti…
sometimes in hardened AD env they disable (actually remove) SeDebugPrivilege globally (via GPO) in order to prevent malicious things targeting process memory (like token stealing, etc.) even as local admin. good (or bad) news is that the bypass is easy: pentest.party/notes/windows/…
Last week I ported TinyNuke HVNC to a Cobalt Strike BOF: github.com/WKL-Sec/Hidden…
The new Teams splash screen warning for external participants is nice and a big improvement (after almost 2 years), but can be bypassed quite easily by using the meeting-chat. Details on my blog. badoption.eu/blog/2023/09/2…

New blog post about an adventure I had with pre-created computer accounts. Let me tell you, old computer accounts can be fun! Ended up creating an impacket script and a PR to the SharpHound ingestor as part of my adventure 🔥 Feedback is appreciated trustedsec.com/blog/diving-in…
United States Trends
- 1. Hunter 1,71 Mn posts
- 2. #IDontWantToOverreactBUT N/A
- 3. $CUTO 11,3 B posts
- 4. Cyber Monday 50,2 B posts
- 5. #MondayMotivation 15,8 B posts
- 6. tannie 223 B posts
- 7. Yeontan 752 B posts
- 8. Enron 4.832 posts
- 9. Victory Monday 2.547 posts
- 10. Good Monday 45,9 B posts
- 11. DeFi 191 B posts
- 12. Burisma 60,4 B posts
- 13. #MondayVibes 4.358 posts
- 14. #GivingTuesday 3.563 posts
- 15. Pat Gelsinger 1.768 posts
- 16. #MondayMood 2.645 posts
- 17. SKZ HOP UNVEIL ULTRA 12,9 B posts
- 18. Intel 28,2 B posts
- 19. $DEGENZ N/A
- 20. NO ONE IS ABOVE THE LAW 71,5 B posts
Something went wrong.
Something went wrong.