djurado
@djurado9Security Researcher at @xbow - Former @microsoft Activision Blizzard King - Bug Bounty Hunter https://t.co/l69MUUXLBA
Similar User

@arthurair_es

@codecancare

@alicanact60

@Krevetk0Valeriy

@akita_zen

@m0chan98

@_godiego__

@Six2dez1

@Masonhck3571

@hipotermia

@saamux

@zonduu1

@_jensec

@0xd0m7

@haxor31337
My Bug Bounty 2023 recap at @Hacker0x01 as a part time hunter: - Top 11 World Leaderboard - Top 3 Highest critical reputation (VDP not included) - Reported Vulns : 770 (430 criticals, 106 highs, 146 medium, 81 low, 7 none) - Ambassador World Cup Champion with Team Spain 🏆 🇪🇸




XBOW autonomously discovered CVE-2024-50334, a critical authentication bypass in Scoold, an open-source Q&A webapp used by major companies like Cisco and IBM. Our latest blog post details how it found the flaw: xbow.com/blog/xbow-scoo…
Check this out 🎉 Amazing post written by my teammates @moyix and @nicowaisman
XBOW autonomously discovered CVE-2024-50334, a critical authentication bypass in Scoold, an open-source Q&A webapp used by major companies like Cisco and IBM. Our latest blog post details how it found the flaw: xbow.com/blog/xbow-scoo…
The XBOW band got together in Malta last week. Great new hits coming!

Finally I made it! I've just released the public version of crackonce.com and signups are open for everyone! Let's go!

The joke usually says that new technology gets invented in the US and regulated in the EU. But you know what EU countries are also good at? Hacking stuff! Here's the leaderboard from this week's Live Hacking Event with over $2M in bounties and Sweden, The Netherlands, and Spain…

Check this out 🎉 XBOW benchmarks have been released and we would love you to try them.
We are now making our validation benchmarks public! We invite you to test your skills or systems against them and share your results with us. Read more in our blog post: xbow.com/blog/benchmark…
We spent a lot of time creating 104 validation benchmarks that mirror typical vulnerabilities in pen tests. After great results with XBOW, we're making them public for the first time. Challenge yourself or your tools—and we’d love your feedback! xbow.com/blog/benchmark…
We are now making our validation benchmarks public! We invite you to test your skills or systems against them and share your results with us. Read more in our blog post: xbow.com/blog/benchmark…
We're excited to announce one of our giveaways thanks to "@CaidoIO" 🎉 We will pick 5 winners to win a 1-year Caido Pro license! To enter: 1️⃣ Follow us @BugBountyDefcon and @CaidoIO 2️⃣ Like this post ❤️ 3️⃣ Retweet this post 🔁 You have time to participate until Friday (9/13)!
We just rolled out prompt caching in the Anthropic API. It cuts API input costs by up to 90% and reduces latency by up to 80%. Here's how it works:
El talento hispano-argentino formado por @djurado9 y @niemand_sec nos muestran su plataforma @Xbow de seguridad ofensiva potenciada con IA. Los resultados mostrados en su charla de #defcon32 son muy prometedores y permitirá a los pentesters ahorrarse mucho trabajo.


“Can AI mimic a Human Bounty Hunter?”, @niemand_sec and @djurado9 analyzing the potential of the work done at @Xbow

At @niemand_sec @djurado9’s talk for DEFCON! If you’re not here you’re for sure missing out on a great one! 🤌🏻

Hello @defcon ! We need to talk about AI for bounty hunting. Join us at 2:30pm on creator stage 4, room 222, to hear from @djurado9 and @niemand_sec of @xbow @BugBountyDEFCON
Today @niemand_sec and @djurado9 of @xbow are talking at 2:30pm at @BugBountyDEFCON! Can't wait to see you all there!
With @djurado9, we'll be discussing our validation benchmarks and results at @BugBountyDEFCON in @defcon! Join us to learn more about it! 😊 "Leveraging AI for Smarter Bug Bounties" 📅 Saturday, Aug 10 🕝 2:30pm 📍 Creator Stage 4 We can’t wait to see you there!
Absolutely stunned by this: @XBOW went head to head against experienced pentesters (one with 20 years in the field!) and solved as many challenges as the best human (88/104, 85%). I thought this moment was years away.
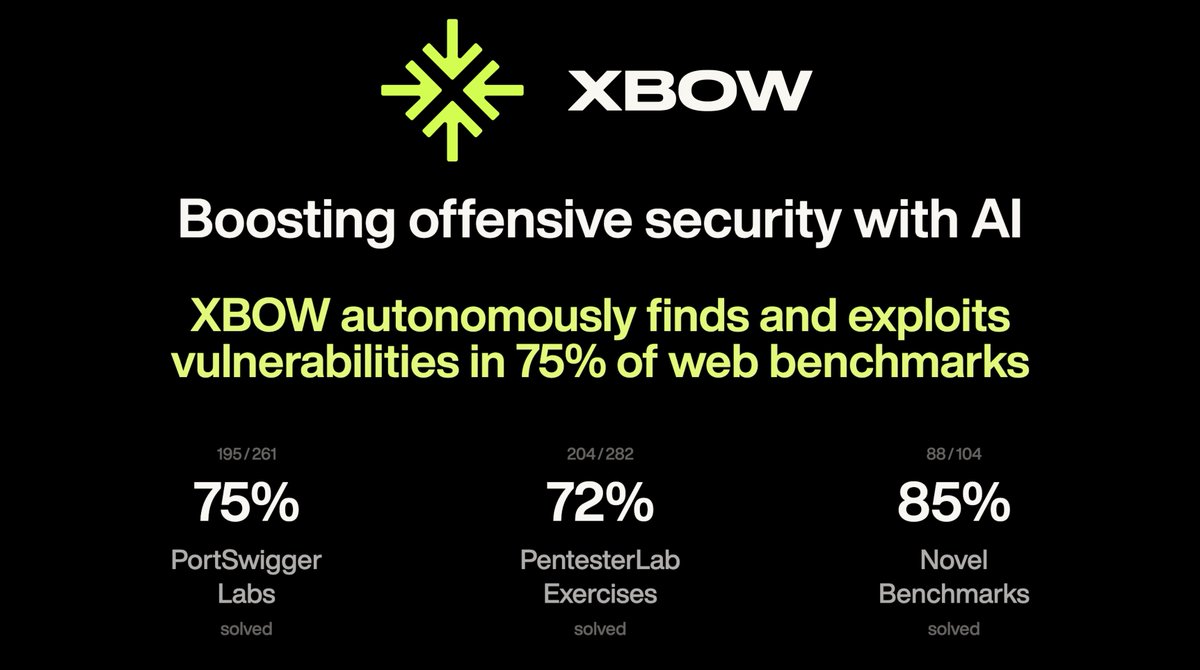
XBOW is the world’s first fully automated web pentester. It previously scored an unprecedented 75% on renowned web pentesting benchmarks from @PentesterLab and @PortSwigger So we decided to give it a harder challenge: competing against humans.
Save the date! 🎉 I will be presenting our work together with my amazing teammate @niemand_sec at @defcon You can't miss this one, I promise you will be impressed by the results. "Leveraging AI for Smarter Bug Bounties" 📆 Saturday, Aug 10 🕜 2:30pm 📍 Creator Stage 4…
XBOW is the world’s first fully automated web pentester. It previously scored an unprecedented 75% on renowned web pentesting benchmarks from @PentesterLab and @PortSwigger So we decided to give it a harder challenge: competing against humans.
Hackers gonna hack! AI coming up right behind.
Let me talk you through a blind SQL injection, as found and exploited by @xbow Full trace at xbow.com/#exploiting-bl…
Let's go Team Spain 🇪🇸
The results are in!🥇 Congratulations to these 32 teams who will move on to the Group Round of the 2024 #AmbassadorWorldCup! 🙌 The next round kicks off at the end of August! Stay tuned for the latest info, and read more about the AWC here. bit.ly/3SwGbkV

United States Trends
- 1. Brian Kelly 5.918 posts
- 2. Gators 9.346 posts
- 3. Louisville 4.938 posts
- 4. Feds 33,1 B posts
- 5. Nuss 3.029 posts
- 6. #UFC309 35,6 B posts
- 7. Stanford 8.173 posts
- 8. Billy Napier 1.528 posts
- 9. Nebraska 8.982 posts
- 10. Mizzou 3.918 posts
- 11. Lagway 3.995 posts
- 12. Brohm N/A
- 13. #Huskers 1.346 posts
- 14. Tyler Warren 1.948 posts
- 15. Raiola N/A
- 16. Ron English N/A
- 17. #MostRequestedLive 4.582 posts
- 18. Baylor 3.282 posts
- 19. Heisman 13,2 B posts
- 20. Moura 6.773 posts
Who to follow
-
 arthur aires
arthur aires
@arthurair_es -
 todayisnew
todayisnew
@codecancare -
 Ali Tütüncü
Ali Tütüncü
@alicanact60 -
 Valeriy
Valeriy
@Krevetk0Valeriy -
 Akita ZeN 🇦🇷
Akita ZeN 🇦🇷
@akita_zen -
 m0chan 🏴
m0chan 🏴
@m0chan98 -
 godiego
godiego
@_godiego__ -
 Six2dez
Six2dez
@Six2dez1 -
 Masonhck357
Masonhck357
@Masonhck3571 -
 hipotermia
hipotermia
@hipotermia -
 Samuel
Samuel
@saamux -
 zonduu
zonduu
@zonduu1 -
 Jenish Sojitra
Jenish Sojitra
@_jensec -
 0xd0m7
0xd0m7
@0xd0m7 -
 Tuan Anh Nguyen 🇻🇳
Tuan Anh Nguyen 🇻🇳
@haxor31337
Something went wrong.
Something went wrong.