newfolder
@newfolderjMuslim Security Student -- NOT from OXFORD | HARVARD | MIT | IIT | IBA | NUST | LUMS | FAST | UET
Similar User

@zhenwarx

@moe1n1

@0xAwali

@lu3ky13

@ashketchum_16

@alp0x01

@haxor31337

@nihad_rekany

@PrettyRecon

@mamunwhh

@sheikhrishad0

@BountyOverflow

@AkashHamal0x01

@CyCatz_Official

@3ncryptSaan
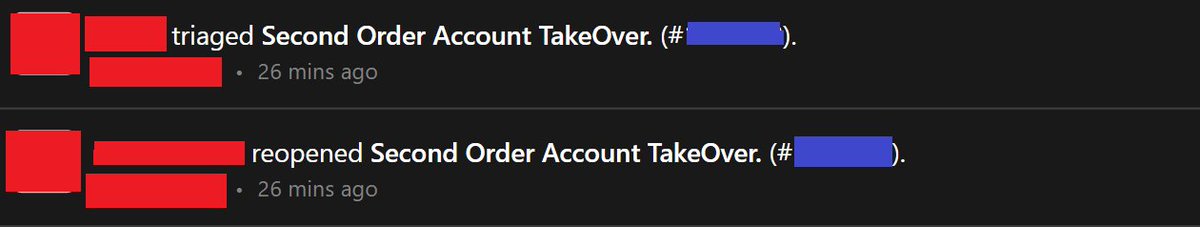
None => Critical (10/10) Second Order Account Takeover : (attacker's VERIFIED email attached to attacker's UNVERIFIED email merged can takeover vicitm's VERIFIED account) H1 : Closing as Self Account Takeover (none). Me : Should I Takeover your Account? H1 : Sure! Me : BOOOM

Just submitted my first Smart Contract Bug to the DeFi Protocol, big thanks to Owen, @pashovkrum & @gogotheauditor for their public audits.
Started testing program of 2017, out of 200 subdomains I chose the main app (which I always do) as it communicate with current API . After 2 days of testing after office for 3 hours a day, I was able to find 5 Crtx, 3 High, 8 mediums. All were related to API's I shared before
P1 in 1 minute for 4*$: user can invite members with “org-member” role only tried “org-xyz” = 400 Read JS files: tried “org-super-admin” & “org-owner” = 401 Bypassed: “org-owner<space>“ = 200 BOOOM
API Leaked all Users Secrets: /v1/org/users=403 /v1/org/admin/users=401 /v1.1/org/admin_id/users=200 (blank response) /v1.1/org/admin_id/users?FUZZ=FUZZ /v1.1/org/admin_id/users?Withrole=true 401(body unauthorised) /v1.1/org/admin_id/users?With[mail,credit_card,apikey]=true BOOM
Thounsand org users leaked /api/org/123 => leaked ORG_NAME only /api/org/123/* => 403 /api/org/123/users =>403 /api/org/ORG_NAME/users =>403 /api/org/@org_name/users => 500 /api/org/@org_name/users/attributes => blank response /api/org/@org_name/users/attributes/email => BOOOM
Organisation Users Complete Data leaked: /api/users => 403 /api/users/all => 403 (json) /api/users/all/name,email,data => 404 /api/users/all?FUZZ=FUZZ /api/users/all?fields=name => 200 ( LOW ) only name was queryable /api/users/all?access=all => BOOOM (email, credit_card etc)
In February what ever I submitted was loss, I have been removed from my University Final Year Project due to low maintenance of Credit Hours of our so called reputed HEC bcz I was busy with bounties. So far I would ( maybe ) repeat one more semester of degree👏.
Quick Account Takeover in a minute: Auth Implementation: After signup ,user change email to unsigned user, session refreshes ,email changed/confirmed to unsigned user. change to victim@x.com =>user exists change to "victim@x.com<SPACE>" or %20 =>200 ok victim id got 2 passwords
Able to access Million+ emails $: API Implementation: /organization/:id => only org name shown /organization/:id/users => 403 typical response /organization/:id/users?get=newfolder => 403 with response & error msg (auth) /organization/:id/users?get=users::metadata => BOOM


( chained "blocked user + Region based Authentication + Pass Reset Flaw to SECOND ORDER ATO") And Triager thought "Attacker would need access to victim's gmail account to perform Second Order Account Takeover." haha Closed N/A Reopened Critical 10 writeup coming Inshallah
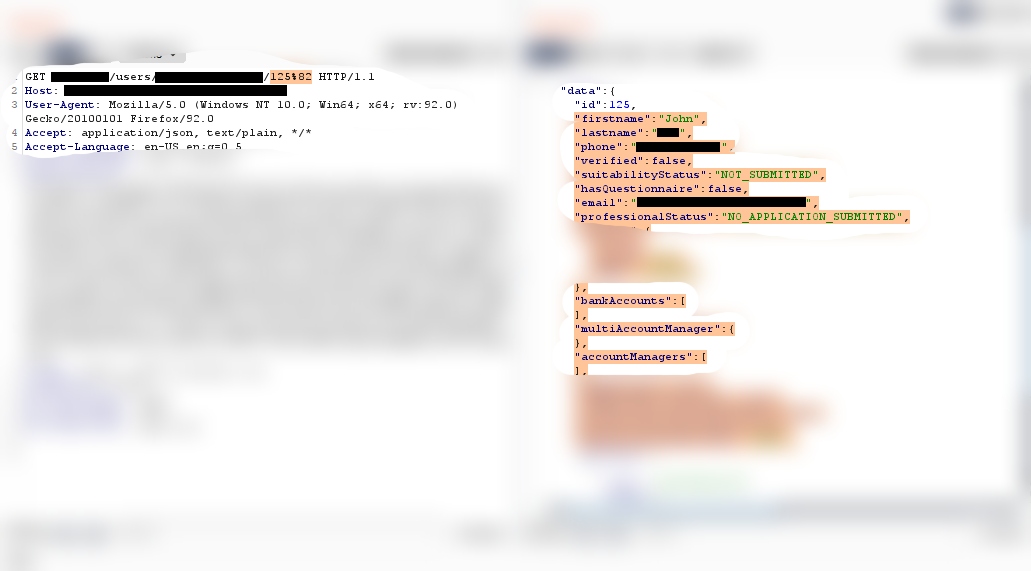
Alhamdullilah, I was awarded 4x$ bounty. Single API call could leak 1MILLION+ users private data I use these %03 %08 %10 %83 etc when I get 403 along with "403 in Api response". means we are beyond WAF but some regex/restrictions/auth-checks are stopping us to get Users data.


United States Trends
- 1. Kendrick 466 B posts
- 2. #AskShadow 15,6 B posts
- 3. $CUTO 7.104 posts
- 4. Luther 35,7 B posts
- 5. Daniel Jones 43,2 B posts
- 6. Drake 68,8 B posts
- 7. Wayne 47,8 B posts
- 8. Squabble Up 21,6 B posts
- 9. Kdot 5.371 posts
- 10. TV Off 28,8 B posts
- 11. MSNBC 167 B posts
- 12. Giants 74,9 B posts
- 13. Dodger Blue 10 B posts
- 14. Kenny 23 B posts
- 15. #TSTTPDSnowGlobe 4.892 posts
- 16. Reincarnated 27,6 B posts
- 17. Gloria 43,8 B posts
- 18. #AyoNicki 3.542 posts
- 19. NASA 66,9 B posts
- 20. One Mic 4.445 posts
Who to follow
-
 Zhenwarx
Zhenwarx
@zhenwarx -
 moSec
moSec
@moe1n1 -
 Mahmoud M. Awali
Mahmoud M. Awali
@0xAwali -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 Ashish Dhone
Ashish Dhone
@ashketchum_16 -
 Alp
Alp
@alp0x01 -
 Tuan Anh Nguyen 🇻🇳
Tuan Anh Nguyen 🇻🇳
@haxor31337 -
 Nihad
Nihad
@nihad_rekany -
 PrettyRECON
PrettyRECON
@PrettyRecon -
 khan mamun
khan mamun
@mamunwhh -
 Sheikh Rishad
Sheikh Rishad
@sheikhrishad0 -
 I¯\_(ツ)_/¯I \ (•◡•) /
I¯\_(ツ)_/¯I \ (•◡•) /
@BountyOverflow -
 root@AkashHamal0x01:~/ # 🇵🇭
root@AkashHamal0x01:~/ # 🇵🇭
@AkashHamal0x01 -
 CyCatz
CyCatz
@CyCatz_Official -
 Shakti Ranjan Mohanty || 🇮🇳 ||
Shakti Ranjan Mohanty || 🇮🇳 ||
@3ncryptSaan
Something went wrong.
Something went wrong.