Mr0x4b
@mr0x4bMalware researcher & reverse engineer enthusiast
🚨 ALERT: Potential ZERO-DAY, Attackers Use Corrupted Files to Evade Detection 🧵 (3/3) ⚠️ Although broken and corrupted, the file remains undetectable by security tools, yet user applications handle it seamlessly due to built-in recovery mechanisms exploited by attackers 🔎…

🚨 ALERT: Potential ZERO-DAY, Attackers Use Corrupted Files to Evade Detection 🧵 (2/3) When analyzing a corrupted file, it is mostly identified as a #ZIP archive or MS Office file 💢 Security solutions attempt to extract its contents, assuming they need to scan the files…

🚨ALERT: Potential ZERO-DAY, Attackers Use Corrupted Files to Evade Detection 🧵 (1/3) ⚠️ The ongoing attack evades #antivirus software, prevents uploads to sandboxes, and bypasses Outlook's spam filters, allowing the malicious emails to reach your inbox The #ANYRUN team…

🚨Alert🚨CVE-2024-30103: Microsoft Outlook Remote Code Execution Vulnerability ⚠This Microsoft Outlook vulnerability can be circulated from user to user and doesn’t require a click to execute. Rather, execution initiates when an affected email is opened.This is notably dangerous…

🚨 #opendir: 185.101.104[.92 Fresh opendir loaded with malware. Beware of fake apps impersonating Spotify and Roblox. For example: 📄 cmdd.exe - #AgentTesla ⬇️ 185.101.104[.92/Built.exe ⬇️ Built.exe - #BLANKGRABBER 🚨 #opendir Alert: 185.101.104[.92 🚨 @500mk500

GitHub comments abused to push malware via Microsoft repo URLs: "Even if you decide not to post the comment or delete it after it is posted, the files are not deleted from GitHub's CDN, and the download URLs continue to work forever. As the file's URL contains the name of the…

🎯 #Meterpreter #backdoor uses tricky #steganography by filtering image channels in yet another #stegocampaign 🕵 A .NET executable file with a #PowerShell script inside downloads a PNG image from a remote C2 server 📝 #Malware calculates a byte array from image channels by…

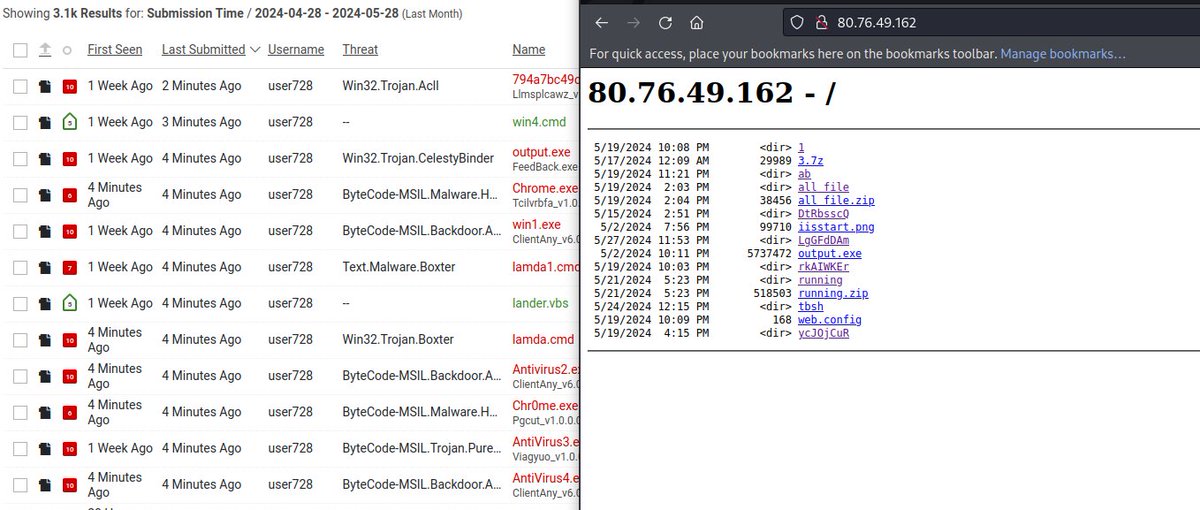
#opendir full with fun again #purelogstealer #asyncrat #celestybinder #backdoor #malware urlhaus.abuse.ch/host/80.76.49.… previously found on urlhaus.abuse.ch/host/85.209.13…
195.10.205[.]162:80 is hosting a #malicious #trojan #loader AS 215826( Partner Hosting LTD ) VT: Default.exe virustotal.com/gui/file/e812a… Any Run: app.any.run/tasks/a9f6b646… @malwrhunterteam @JAMESWT_MHT @500mk500 @ReBensk @banthisguy9349 @anyrun_app
![raghav127001's tweet image. 195.10.205[.]162:80 is hosting a #malicious #trojan #loader
AS 215826( Partner Hosting LTD )
VT: Default.exe <a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/TR9clksC5x">virustotal.com/gui/file/e812a…</a>
Any Run:
<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/c5KJqKWtn7">app.any.run/tasks/a9f6b646…</a>
@malwrhunterteam @JAMESWT_MHT @500mk500
@ReBensk @banthisguy9349 @anyrun_app](https://pbs.twimg.com/media/GOnVvN_WUAAqHFz.jpg)
![raghav127001's tweet image. 195.10.205[.]162:80 is hosting a #malicious #trojan #loader
AS 215826( Partner Hosting LTD )
VT: Default.exe <a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/TR9clksC5x">virustotal.com/gui/file/e812a…</a>
Any Run:
<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/c5KJqKWtn7">app.any.run/tasks/a9f6b646…</a>
@malwrhunterteam @JAMESWT_MHT @500mk500
@ReBensk @banthisguy9349 @anyrun_app](https://pbs.twimg.com/media/GOnWq9LXgAEv2V5.jpg)
![raghav127001's tweet image. 195.10.205[.]162:80 is hosting a #malicious #trojan #loader
AS 215826( Partner Hosting LTD )
VT: Default.exe <a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/TR9clksC5x">virustotal.com/gui/file/e812a…</a>
Any Run:
<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/c5KJqKWtn7">app.any.run/tasks/a9f6b646…</a>
@malwrhunterteam @JAMESWT_MHT @500mk500
@ReBensk @banthisguy9349 @anyrun_app](https://pbs.twimg.com/media/GOnXYgfWIAAsuFY.jpg)
Finally seeing some post-compromise from #SolarMarker, it's been awhile 👀 Kudos to @bohansec for retrieving the sample and logs. 🕔 Initial check-in: 146.70.80.]83 🕤 Backdoor C2: 2.58.15.]118 🔏 Observed signature: Ameri Mode Inc. (revoked) 🌻 C2 for the stealer and hVNC:…
![RussianPanda9xx's tweet image. Finally seeing some post-compromise from #SolarMarker, it's been awhile 👀
Kudos to @bohansec for retrieving the sample and logs.
🕔 Initial check-in: 146.70.80.]83
🕤 Backdoor C2: 2.58.15.]118
🔏 Observed signature: Ameri Mode Inc. (revoked)
🌻 C2 for the stealer and hVNC:…](https://pbs.twimg.com/media/GOPHbXxW0AAi4p5.jpg)
http://141.11.109.151:8000/ Yikes opendir full with malware

A great depiction of the current state of anti malware.
I changed a PNG in my app and suddenly Google and Ikarus think my app is a virus. I would like the last 2 hours of my life back. Here's a screenshot of the PNG so you don't get infected.


"YARA is dead, long live YARA-X!" 🎉 After 15 years, YARA gets a full rewrite in Rust, bringing enhanced performance, security, and user experience. Dive into the details in latest blog post by @plusvic : blog.virustotal.com/2024/05/yara-i…

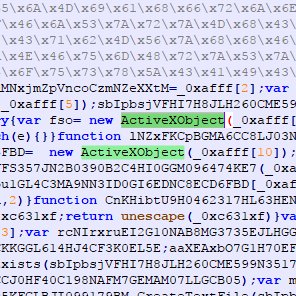
#wshrat part 2 #malware SHA256 hash: 3D3B93E744A9FC154A70B6A6B709BE2806598ABB2B00DB8E51FAA55F961F3076 IoC: 46.246.6[.]12 (port 7045) chongmei33.publicvm[.]com
![mr0x4b's tweet image. #wshrat part 2 #malware
SHA256 hash: 3D3B93E744A9FC154A70B6A6B709BE2806598ABB2B00DB8E51FAA55F961F3076
IoC:
46.246.6[.]12 (port 7045)
chongmei33.publicvm[.]com](https://pbs.twimg.com/media/GOBATxDWYAAB6T8.jpg)
#wshrat #malware SHA256 hash: 7e66f9c9c8dbbd79ea3e3a11dc7e902897ffa2bac730d1df3db8e12f09c44722 IoC https[:]//electrikar.com[.]mx/wp-includes/Text/mc.js 157.230.6[.]20
![mr0x4b's tweet image. #wshrat #malware
SHA256 hash: 7e66f9c9c8dbbd79ea3e3a11dc7e902897ffa2bac730d1df3db8e12f09c44722
IoC
https[:]//electrikar.com[.]mx/wp-includes/Text/mc.js
157.230.6[.]20](https://pbs.twimg.com/media/GOA9dMfW8AAK28i.jpg)
Discover how we use Gemini 1.5 Pro to improve malware analysis! Gemini's capability to tackle up to 1 million tokens makes a difference, not only when facing huge macros, but also providing a way to automate analysis of decompiled code, by @bquintero : blog.virustotal.com/2024/04/analyz…

As #malware continues to challenge analysts, so we checked how Gemini 1.5 Pro could help and found that: 🔎 Results were accurate, even with a zero-detection @VirusTotal sample ⏱️ It produced an accurate analysis in less than a minute Learn more: bit.ly/3WjINFq

United States Trends
- 1. Warriors 66 B posts
- 2. Rockets 41 B posts
- 3. Draymond 6.880 posts
- 4. Steve Kerr 4.509 posts
- 5. Steph 25 B posts
- 6. Knicks 33,2 B posts
- 7. Hawks 31,4 B posts
- 8. Podz 4.696 posts
- 9. #Survivor47 11,5 B posts
- 10. Trae Young 20,9 B posts
- 11. Selena 80,9 B posts
- 12. Jalen Green 3.871 posts
- 13. Sengun 5.018 posts
- 14. #AEWDynamite 24,7 B posts
- 15. #GSWvsHOU N/A
- 16. Voice of America 22,6 B posts
- 17. Bill Kennedy N/A
- 18. #Liftoff 1.082 posts
- 19. Rachel 50,8 B posts
- 20. #DubNation 2.172 posts
Something went wrong.
Something went wrong.











![mr0x4b's tweet image. #AgentTesla downloader #malware
IoC http[:]//98.142.254[.]109/rr/Pmhjlkp.dat](https://pbs.twimg.com/media/GN8FPnwWgAAIH-R.jpg)