ak1001
@ak100117Malware Analyst | Reverse Engineer | Security Research https://t.co/Kq7TRiAQM0
Similar User

@CyberSpooon

@infinitywarrio7

@Iiquidmvmt

@aaqeel87

@okinom

@outhex2
🚨 Cybercriminals exploit Spotify for #malware distribution. 🎵 Why? Spotify has a strong reputation and its pages are easily indexed by search engines, making it an effective platform to promote malicious links.

This is probably the simplest case where we see "JUMPOUT" statements, and the solution for such a case is really easy. #ida #reversing

🚨 @UHC is hiring a Senior Malware Analyst! 🚨 If analyzing malware is your mission, apply now: careers.unitedhealthgroup.com/job/20783386/s… This is a remote role, but candidates must be located in the U.S. Not for you? Please retweet – this might be the opportunity one of your followers has been…

#Hunting Malware Samples Starting from one domain Relations 🔅virustotal.com/gui/domain/pub… 🔱Related Samples Collection bazaar.abuse.ch/browse/tag/pub… 🔆Related Urls urlhaus.abuse.ch/browse/tag/pub…



Huge thanks to @vinopaljiri for his ConfuserEx2 deobfuscation tools—worked flawlessly on a recent sample! 🔥 Check out his detailed walkthrough: youtu.be/y_ma9cLFdmY?si… and the tools: github.com/Dump-GUY/Confu…
I created a new repo where I will be uploading fully annotated IDBs of interesting samples that I analyzed, check out my fully annotated IDB for APT41 StealthVector. github.com/Blu3Eye/Malwar…
We have uploaded the workshop materials from our REcon 2024 workshop on Automating Malware Deobfuscation with Binary Ninja. The slides, workshop manual and code can be found here: cfp.recon.cx/recon2024/talk… thank you again to all those who attended!
Initial Sample Traneasy 易翻译助手 3.2.3f.msc MD5 271dea4d0bdfa80e4ad01257508571cc ❇️AnyRun #SilverFox app.any.run/tasks/f9aff535… Samples bazaar.abuse.ch/browse/tag/118…



.NET assembly loader with patchless AMSI and ETW bypass github.com/VoldeSec/Patch…
Something a bit different for you all this time round, as we ask is the CCP the biggest APT? intrusiontruth.wordpress.com/2024/08/07/is-…
The eighth article (62 pages) of Malware Analysis Series (MAS) is available on: exploitreversing.com/2024/08/07/mal… I am actively writing the following articles: 01. ER_03 (Hyper-V) 02. ER_04 (MacOS/iOS) My focus is on writing articles in the Exploiting Reversing series (ERs), which is a…

#Lumma Stealer has now opened a "Log Market" where Lumma operators (with an storefront code) can sell its own logs directly from their panel. Purchase is made through crypto deposits in BTC or ETH addresses. Currently there's ~5700 logs at sale from unkown vendors




Styx Stealer 7ef60ef8045c6bb90eaaf66e2c1c4954 #StyxStealer #Stealer #IOC



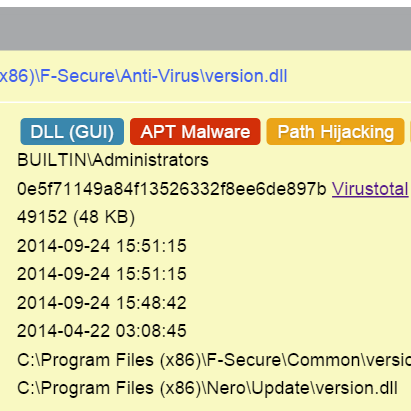
#MustangPanda is abusing Azure for distributing #PlugX🤔 CC: @MsftSecIntel virustotal.com/gui/file/ca0df…

🚨 New blog! We just published research on an APT41 campaign targeting a Taiwanese government-affiliated research institute. Great team work with @joeychennogg @_vventura!! #Shadowpad #CobaltStrike #APT41 blog.talosintelligence.com/chinese-hackin…
Published detection for CVE-2024-38112, which involves a .url shortcut containing mhtml and !x-usc, allowing websites to be opened with Internet Explorer.

We've uploaded the x86 Assembly Primer lecture from the Introduction to Malware Binary Triage course. This provides an overview of the x86 assembly language, memory structures and calling conventions. Enjoy! youtu.be/dunhGOubqKc
⚠ As expected, the incident with #CrowdStrike has been exploited to distribute malware. 🎯 In our example, an archive containing #Hijackloader, which delivers #Remcos to the infected system, is downloaded into the system under the guise of a #hotfix. 💢 The name of the ZIP…


"Adobe-PDF-Viewer.js": 307d1fc0c524e69ce8c8fe8aa41d0b5d314fd9553f0138fdf370efacaa2e0c67 From: https://ainvestinternational[.]com/wp/Adobe-PDF-Viewer.js

I've published my analysis of #StrelaStealer. Victims include those who utilize Thunderbird or Outlook 2016 email clients. This analysis delves into how StrelaStealer operates, including how the malware decrypts Outlook 2016 passwords. link.medium.com/sNnMKxy4hLb
United States Trends
- 1. Bama 26,5 B posts
- 2. Miami 96,4 B posts
- 3. Clemson 13,9 B posts
- 4. South Carolina 22,6 B posts
- 5. XDefiant 8.097 posts
- 6. Cam Payne N/A
- 7. Warde Manuel 1.555 posts
- 8. Ubisoft 7.201 posts
- 9. Africa 260 B posts
- 10. #CFBPlayoff 4.104 posts
- 11. $DCARS 6.127 posts
- 12. Gundam 94 B posts
- 13. Lindsey 25,7 B posts
- 14. #MAFS N/A
- 15. #tomatoJay 2.429 posts
- 16. Cade Phillips N/A
- 17. Committee 176 B posts
- 18. Hegseth 124 B posts
- 19. The CFP 11,7 B posts
- 20. #MarriedAtFirstSight N/A
Something went wrong.
Something went wrong.