sean
@seanmwUnpacMe | OALABS | Security Researcher
Similar User

@herrcore

@x64dbg

@unpacme

@struppigel

@mrexodia

@silascutler

@REhints

@malpedia

@cPeterr

@Myrtus0x0

@2igosha

@anyrun_app

@sysopfb

@mal_share

@pmelson
Here is a clip of me from earlier this year predicting that LLMs wouldn’t take any infosec jobs. I was wrong🧵
AI-Powered Threat Reporting and Analysis... ATIP It's live now, check it out 🤖 blog.unpac.me/2024/11/25/ati…
We're doing a Black Friday week sale and providing 15% off our Premium course bundle. With this you'll get access to both of our Introduction to Malware Binary Triage courses (IDA and Binary Ninja) and Premium benefits! Ends December 1. More details here: training.invokere.com/pricing

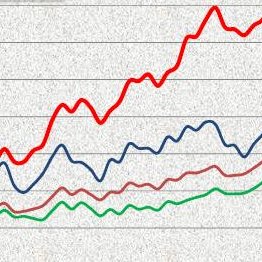
1/2 Payload statistics from October 2024 📊 We observed 373 tasks distributed by threat actors across the tracked botnets. This resulted in 4510 unique payloads. Top families: 1. #StealC 2. #Lumma 3. #Amadey 4. #VidarStealer 5. #SmokeLoader Unpacking & detection: @unpacme

HashDB Release 1.10.0 Now with support for IDA 9, and continued backwards compatibility all the way back to IDA 7.5 🙌 thanks to @plebourhis for the help!! github.com/OALabs/hashdb-…
Imagine no zoom meetings 📈
Imagine how much innovation could be unlocked if there was a nice JS SDK that allowed a HTML Canvas element to join a zoom meeting or Google meet.
This is one of the reasons we started classifying legacy samples as #Zombieware. We've observed that many high volume feeds used by both researchers and academics contain a large % of legacy malware samples. We found it difficult to properly prioritize analysis of samples,…
I have looked at 2024 malware research papers in academia and found that none of them used today's relevant malware. Families they used were old worms and viruses that had been relevant decades ago and nowadays only thrive on sandbox systems.



Payload statistics from September 2024 📊 We observed 752 tasks distributed by threat actors across the tracked botnets. This resulted in 3841 unique payloads. Top families: 1. #StealC 2. #Amadey 3. #SmokeLoader 4. #VidarStealer 5. #Tofsee Unpacking and detection: @unpacme

🦺We’re seeing some processing issues that may impact overall analysis time. We’re looking into it and expect to have it resolved shortly.
Last minute change in the schedule of BruCON 0x10. I will be presenting a workshop about LLVM for Reverse Engineers (introduction) brucon0x10.sched.com/event/60c6e638… @brucon
Is this a new stealer technique or just something flying under the radar 🤔 - Open browser in kiosk mode (no escape) - Force user to enter Google creds - Steal them from the browser! cc @unpacme @LIA_Intel research.openanalysis.net/credflusher/ki…
UNPACME 8.5.0 is live! ⚡️ MalwareID - a blazing-fast mode for quickly identifying and extracting malware configurations. 🔎 New Pivots and Improved Search 💾 Updated DiE Interface & Rules 🚀 Yara Hunt Improvements blog.unpac.me/2024/09/08/mal…
Got a bit motivated by @herrcore stream to write another #Zharkbot Yara rule that hopefully works on new builds 😁 Hunt results from @unpacme : unpac.me/yara/hunt/resu… Rule reference: github.com/RussianPanda95…

Notes are live, vod will be up by the weekend! research.openanalysis.net/zharkbot/triag…
New #TinyTracer (2.8) is out: github.com/hasherezade/ti… - including some new AntiVm/AntiDebug bypasses, and other useful features 😊

New blog entry: C++ Unwind Metadata: A Hidden Reverse Engineering Bonanza msreverseengineering.com/blog/2024/8/20…

United States Trends
- 1. Thanksgiving 30,2 B posts
- 2. #AEWDynamite 24,6 B posts
- 3. Tyrese Martin 1.280 posts
- 4. Friday Night Lights 15,1 B posts
- 5. Druski 20,2 B posts
- 6. Pat Spencer N/A
- 7. #Survivor47 4.295 posts
- 8. Kevin Hart 8.229 posts
- 9. Knicks 13,1 B posts
- 10. Zuck 10,2 B posts
- 11. Vindman 58,4 B posts
- 12. #BillboardIsOverParty 135 B posts
- 13. Cruz Azul 17,9 B posts
- 14. Ace Bailey 1.165 posts
- 15. #ALLCAPS 1.114 posts
- 16. Trae Young 6.033 posts
- 17. Max Christie 2.137 posts
- 18. #Blackhawks 1.312 posts
- 19. Harden 14,8 B posts
- 20. Taylor Hall 1.133 posts
Who to follow
-
 herrcore
herrcore
@herrcore -
 x64dbg
x64dbg
@x64dbg -
 UNPACME
UNPACME
@unpacme -
 Karsten Hahn
Karsten Hahn
@struppigel -
 Duncan Ogilvie 🍍
Duncan Ogilvie 🍍
@mrexodia -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 REhints
REhints
@REhints -
 Malpedia
Malpedia
@malpedia -
 Chuong Dong
Chuong Dong
@cPeterr -
 Myrtus
Myrtus
@Myrtus0x0 -
 Igor Kuznetsov
Igor Kuznetsov
@2igosha -
 ANY.RUN
ANY.RUN
@anyrun_app -
 sysopfb
sysopfb
@sysopfb -
 MalShare
MalShare
@mal_share -
 Paul Melson
Paul Melson
@pmelson
Something went wrong.
Something went wrong.