Hiroshi Suzuki
@herosi_tA malware analyst, forensic investigator, incident responder and researcher. A conference speaker and trainer such as Black Hat, Virus Bulletin and FIRST.
Similar User

@4n6ist

@unkn0wnbit

@you0708

@cci_forensics

@Metemcyber

@MasafumiNegishi

@avtokyo

@x64koichi

@00001B1A

@strinsert1Na

@shokoaraki

@f47sh33p

@EurekaBerry

@hiropooh

@soji256
Thanks to YOU, our course at #BHUSA have sold out now! However, don't worry about it. We will add several seats. Stay tuned! @BlackHatEvents blackhat.com/us-19/training…

#UAC (Unix-like Artifacts Collector) v3.0.0 has been released. Many of my PRs were also merged! Thanks, @tclahr #DFIR #Linux
New #UAC (Unix-like Artifacts Collector) v3.0.0 released! 🌟 New features 🔎 New artifacts 👨💻 Thanks to all the contributors!!! Get it here: github.com/tclahr/uac#dfir #digitalforensics #cybersecurity #infosec
GCC 2025 TaiwanでC++マルウェアの解析に関する講義することになりました。 gcc.ac/#reverse-engin… 募集は以下のページでされています。興味のある学生さん、応募お待ちしております。 security-camp.or.jp/event/gcc_taiw…
GCC 2025 TaiwanでC++マルウェアの解析に関する講義することになりました。 gcc.ac/#reverse-engin… 募集は以下のページでされています。興味のある学生さん、応募お待ちしております。 security-camp.or.jp/event/gcc_taiw…
サイバーセキュリティの世界でトップクラスのカンファレンスBlack Hat USA 2024にIIJの高山が参加しました。高山はIIJチームが提供するトレーニングコースのサポートをしつつ、様々な発表も聴講しています。そのサマリがレポートされています、どれも面白そうです。 eng-blog.iij.ad.jp/archives/27540

Due to some missing links on the conference web pages, I uploaded my conference talk pdfs for 10 years. Time flies. speakerdeck.com/takahiro_haruy…
Early pricing for our #BHUSA course ends this Friday. To save $300, join our DFIR course now! blackhat.com/us-24/training…
Our #BHUSA DFIR course will attack Win11 23H2 and Server 2022 with in-the-wild malware/attack tools. Then, we will analyze them to discover what evidence the attack tools remain, which means you can learn both attack and defense. Join our course: blackhat.com/us-24/training…


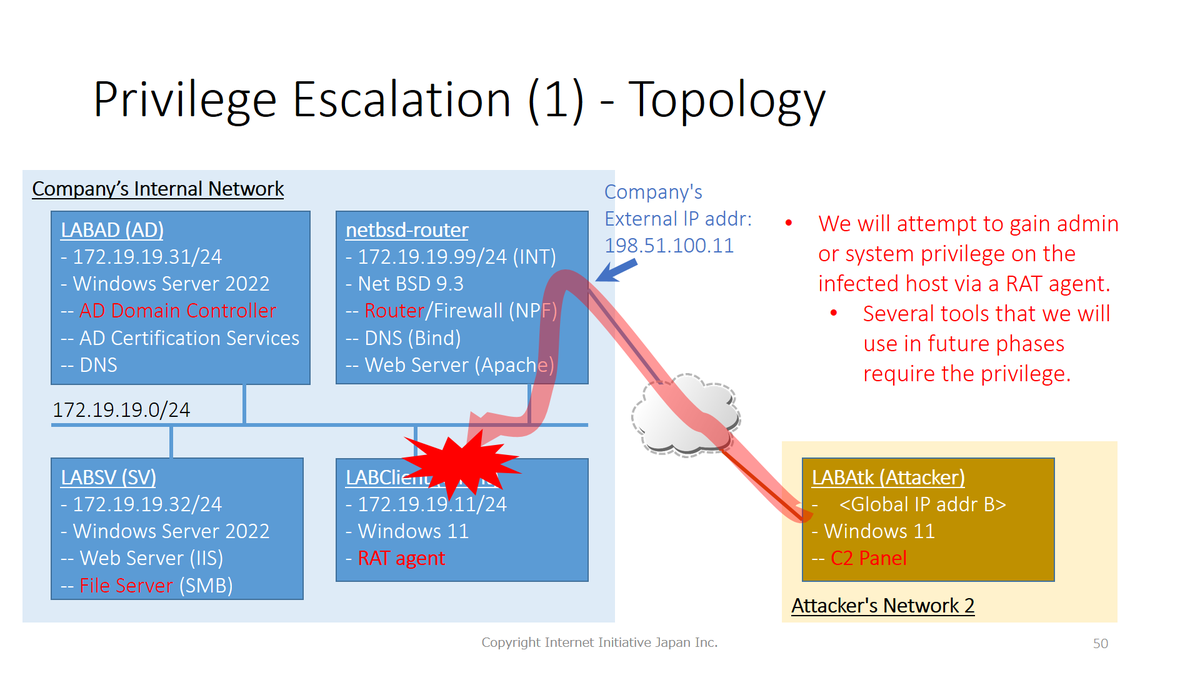
Our #BHUSA DFIR course will attack Win11 23H2 and Server 2022 with in-the-wild malware/attack tools. Then, we will analyze them to discover what evidence the attack tools remain, which means you can learn both attack and defense. Join our course: blackhat.com/us-24/training…




Google Chrome Platform Notifications Database analysis with the new @ArsenalRecon LevelDB parser sans.org/blog/google-ch…

Visual Studio Code (VS Code) used by APT actor as a RAT tool case report. Our research member's presentation material at JSAC2024 is available now. jsac.jpcert.or.jp/archive/2024/p…
I wrote a script to convert Cisco MZIP format firmware into ELF. It might help checking manipulated firmware by attackers. Enjoy! github.com/herosi/mzip2elf
The tool, result and exploit PoCs github.com/TakahiroHaruya… Intel didn't assign the CVE number for stdcdrv64.sys but told us the driver was fixed.
VMW Carbon Black TAU discovered 34 unique vulnerable WDF/WDM drivers (237 file hashes), including ones made by major chip/BIOS/PC makers. By exploiting the drivers, an attacker without privilege may erase/alter firmware, and/or elevate OS privileges. blogs.vmware.com/security/2023/…
Don't miss this upcoming #APACDFIRSummit talk! 🗓️ 🎤 The Essentials of Information Gathering and Analysis Required of CSIRTs 👥 Masafumi Negishi ✍️ Join us September 7 - 8 for Free Live Online: sans.org/u/1qeJ

Hayabusa 2.8.0 released with two new "X" options. (Not to celebrate the unfortunate renaming of twitter...we just ran out of letters 😊) -x will carve evtx records from empty pages thanks to @forensic_matt and -X will perform de-duplication of detections.

昨年日本で、また今年USAで好評だったトレーニングを今年もBlack Hat Japan Tainings 2023で、提供します。 今回は対面での提供に戻ります。2日間で実施するので、より業務都合つけやすいと思います。奮ってご参加ください。 表示が崩れているのは僕らのせいではありませんw blackhat.com/trj-23/trainin…
I wrote an article about how to analyze malware with my tool CTO in our comapany's quarterly repoet. Malware Analysis with CTO and CTO Function Lister iij.ad.jp/en/dev/iir/059… You can download CTO from the URL below. github.com/herosi/CTO
「CTOとCTO Function Listerを使ったマルウェアの解析方法」というタイトルで、IIRに記事を書きました。 HTML: iij.ad.jp/dev/report/iir… PDF: iij.ad.jp/dev/report/iir… CTOのコード: github.com/herosi/CTO
I'm extremely excited to present at Black Hat Arsenal the new rewrite and upgrades to Noriben. I last presented it there *8* years ago, and I can't wait to show off a much evolved version. Free and simple malware sandboxing! blackhat.com/us-23/arsenal/…
Early pricing for our #BHUSA course ends this Friday. To save $300, join our practical forensic course now! blackhat.com/us-23/training…
Our #BHUSA course will attack a Windows domain, which consists of Win11 and Server 2022, with in-the-wild malware and attack tools first. Then, we will analyze them. In this single course, you can learn both red and blue team perspectives. Join our course! blackhat.com/us-23/training…




United States Trends
- 1. #MULTICO N/A
- 2. Thanksgiving 179 B posts
- 3. $CUTO 13 B posts
- 4. #BBMAs 123 B posts
- 5. Kreider 1.463 posts
- 6. #IDontWantToOverreactBUT 1.137 posts
- 7. #SonicMovie3 50,9 B posts
- 8. #MondayMotivation 20,6 B posts
- 9. Axios 16 B posts
- 10. $FRED 21,2 B posts
- 11. Phylicia Rashad 1.551 posts
- 12. Victory Monday 3.988 posts
- 13. Kikuchi 6.974 posts
- 14. Kemp 4.055 posts
- 15. Tannenbaum N/A
- 16. Marshall Law 1.574 posts
- 17. Angels 38,7 B posts
- 18. Trouba 1.205 posts
- 19. Snoop 28,9 B posts
- 20. Teedra Moses 2.993 posts
Who to follow
-
 Teru Yamazaki
Teru Yamazaki
@4n6ist -
 Minoru Kobayashi
Minoru Kobayashi
@unkn0wnbit -
 NAKATSURU You
NAKATSURU You
@you0708 -
 Takahiro Haruyama
Takahiro Haruyama
@cci_forensics -
 Metemcyber
Metemcyber
@Metemcyber -
Masafumi Negishi
@MasafumiNegishi -
 avtokyo
avtokyo
@avtokyo -
 Koichi
Koichi
@x64koichi -
 _roku_
_roku_
@00001B1A -
 MigawariIV
MigawariIV
@strinsert1Na -
 Shoko ARAKI
Shoko ARAKI
@shokoaraki -
 fatsheep
fatsheep
@f47sh33p -
 Yurika
Yurika
@EurekaBerry -
 HIROKI IWAI
HIROKI IWAI
@hiropooh -
 soji256
soji256
@soji256
Something went wrong.
Something went wrong.