
H̷͙̰͕̼̫̥͔̮͓͈͉̩͇̯̍̄̍́͊̋̓͜_̸̭̤̻̫͚̗͒̀́̊͆͜D̷̛̈́̏̓̈̒̈͂̚͝
@hd_421Similar User

@fyoorer

@KHIZER_JAVED47

@antyurin

@Wh11teW0lf

@theRaz0r

@0xw2w

@theBeched

@sergeybelove

@0xKonqi

@asad0x01
🔺New on Apple Security Research blog: a deeply comprehensive Private Cloud Compute security guide, and an unprecedented Virtual Research Environment allowing you to run production PCC software right on your Mac with Apple silicon. And up to a $1M bounty! security.apple.com/blog/pcc-secur…
🔺New on the Apple Security Research blog: introducing Private Cloud Compute! We believe this is the most advanced security architecture ever deployed for cloud AI compute at scale. security.apple.com/blog/private-c…
🔺Now live: the May 2024 update to the Apple Platform Security Guide! support.apple.com/guide/security…
🔺New on the Apple Security Research blog: introducing PQ3, a groundbreaking post-quantum cryptographic protocol for iMessage. To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world. security.apple.com/blog/imessage-…
🔺New on the Apple Security Research blog: a brief technical overview of iMessage Contact Key Verification! security.apple.com/blog/imessage-…
🔺New on the Apple Security Research blog: we pit our hardened kalloc_type XNU allocator against SockPuppet, a powerful vulnerability from the past: security.apple.com/blog/what-if-w…
I've added a bunch of security checks for SAML. The bottom part of the article will be useful for pentesters too invicti.com/blog/web-secur…
My video presentation of AppsecStudy from #blackhateurope youtu.be/n0gOjmMiuKM via @YouTube Subscribe, like, and share 😀 #BlackHat
I hoped to attend #BlackHatEurope @BlackHatEvents with two tools, but because my visa is not ready, I will miss it. It's very upsetting, but sometimes it happens. Let me write a few words about the tools and share the links in this thread. blackhat.com/eu-22/arsenal/… #BlackHat
Incredible work!
More car hacking! Earlier this year, we were able to remotely unlock, start, locate, flash, and honk any remotely connected Honda, Nissan, Infiniti, and Acura vehicles, completely unauthorized, knowing only the VIN number of the car. Here's how we found it, and how it works:

I’m really excited for us to shed light on some really cool work we’ve been doing to harden the XNU allocator! This has been a huge effort by so many people, and I’m very proud of the direction: security.apple.com/blog/towards-t…
Today I am finally releasing a new 3-part browser exploitation series on Chrome! This was written to help beginners break into the browser exploitation field. Part 1 covers V8 internals such as objects, properties, and memory optimizations. Enjoy! jhalon.github.io/chrome-browser…
#DexcaliburPro on steroid💊 Just added device-oriented features to inspect / generate hooks to spoof data read from / write to device 😍 by any instrumented app on this device (1/n) @_bhamza @U039b @Farenain @trufae @EmericNasi @_reversense_ #hacking #android #frida #security
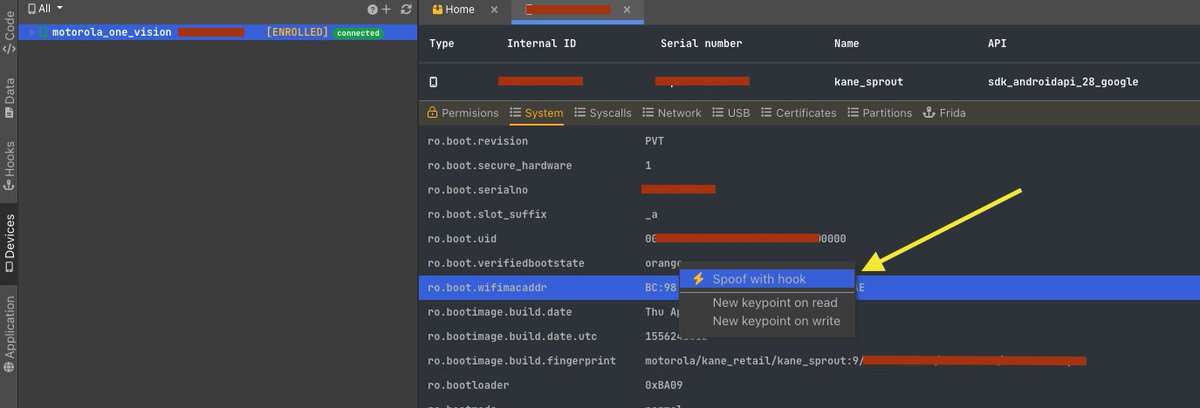
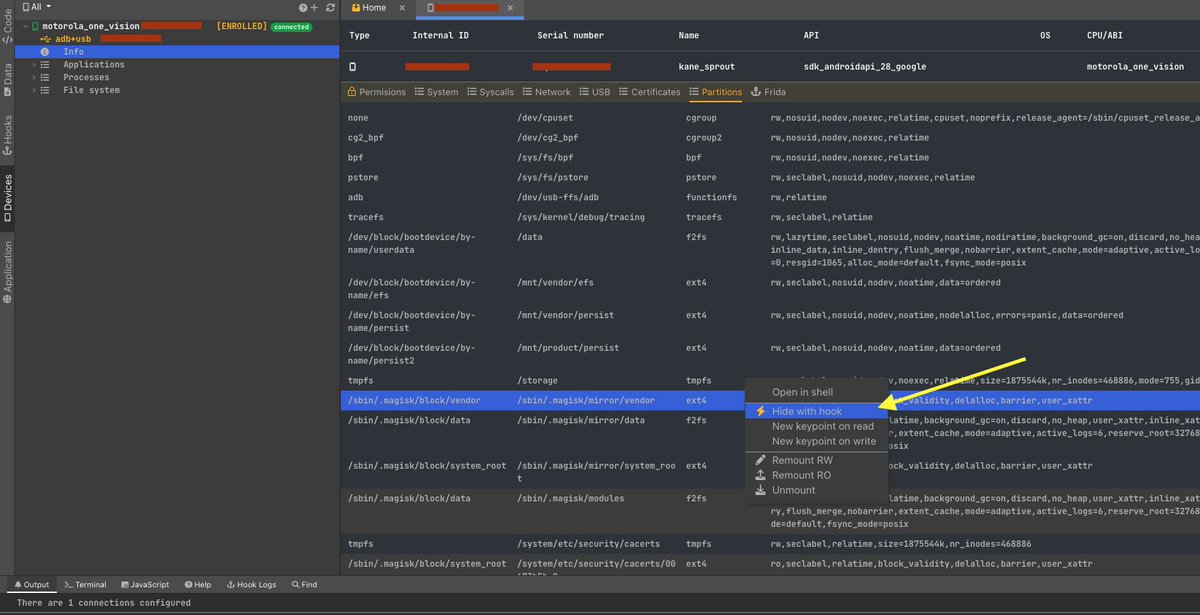
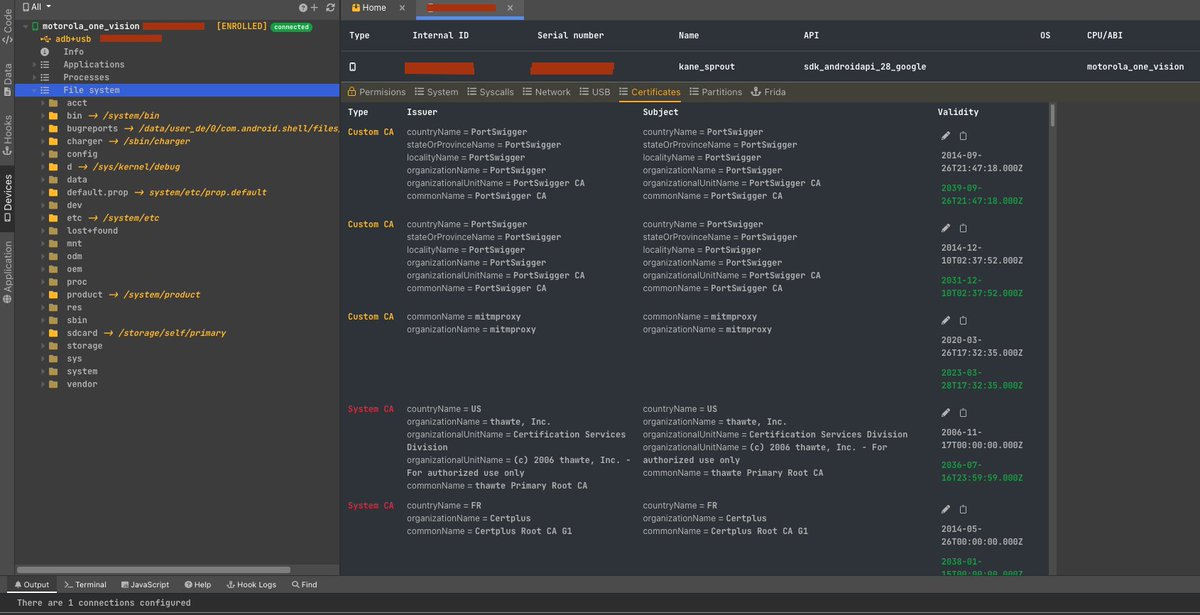
Smooth and simple 👍
Bypassing ContentProvider.openFile() internal security checks in Android [1/3] I've discovered an interesting trick that you may use to access private information using a content provider


DroidGuard: A Deep Dive into SafetyNet 🔥 #MobileSecurity #AndroidSecurity [SLIDES+PAPER+VIDEO] by @rh0main romainthomas.fr/publication/22…
Great and technically deep WP/talk on DroidGuard internals, totally recommended!
The slides and the whitepaper about SafetyNet/DroidGuard are available here: romainthomas.fr/publication/22…

This is a thread on the legality of reverse engineering (RE) software, inspired by @FrenchYeti's recent decision of not streaming a talk due to legal pressures. 1/
Stop war! 🙏
All I can think of are the Ukrainian and Russian CTF players I have met, whose writeups I have read, whose talks I have watched, who collaborated with me on videos. I always felt that hacking unites the world. It makes me cry, I'm scared and cope by distracting myself. 😢
Frida is really powerful and popular instrumentation frameworks, however there’s not many useful information sources on advanced usage gathered in single place, but here we have this gem, well done guys!
Releasing today: learnfrida.info It's a small, free web handbook to learn about binary instrumentation using @fridadotre If you found this resource interesting, please share for others to learn!
A blog post about HTTP/2-related checks that I have recently added to Acunetix. acunetix.com/blog/web-secur… Based on my research presented at ZeroNights.
United States Trends
- 1. #twitchrecap 4.299 posts
- 2. #BeldexBrowser 5.965 posts
- 3. AJ Dybantsa 3.877 posts
- 4. $CUTO 5.475 posts
- 5. #HumanRightsDay 78,8 B posts
- 6. Jimmy Butler 3.295 posts
- 7. Kevin Young N/A
- 8. Malibu 11,4 B posts
- 9. Jamie Foxx 3.817 posts
- 10. Nikki Giovanni 65,5 B posts
- 11. #tuesdayvibe 6.331 posts
- 12. #csm186 1.374 posts
- 13. 28 Years Later 29,5 B posts
- 14. First Take 57,7 B posts
- 15. Jackie Aina 1.350 posts
- 16. Good Tuesday 39,1 B posts
- 17. Harris and Walz N/A
- 18. Taco Tuesday 8.507 posts
- 19. Neely 301 B posts
- 20. Herb Jones N/A
Something went wrong.
Something went wrong.




























































































































![Account for the day[0] podcast + media.](https://pbs.twimg.com/profile_images/1221600753904537601/8sV0PIy_.png)










