
Vahagn Israelian 🇦🇲
@0xKonqiApplication Security | Synack Red Team
Similar User

@malcolmx0x

@uraniumhacker

@Zombiehelp54

@streaak

@niksthehacker

@princechaddha

@Parth_Malhotra

@Black2Fan

@Wh11teW0lf

@Paresh_parmar1

@vulnh0lic

@jackds1986

@har1sec

@RakeshMane10

@Karel_Origin
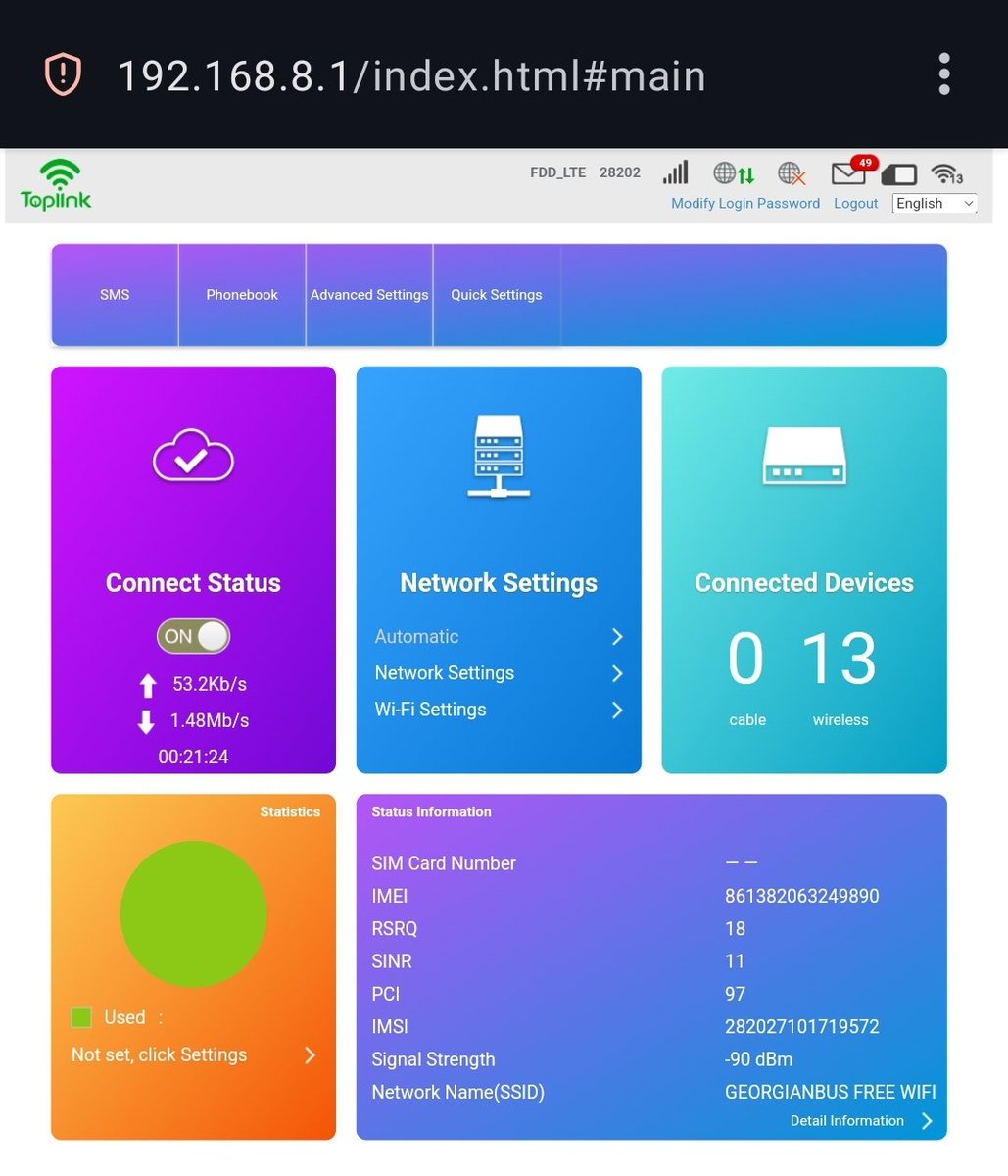
Heading to the airport on a Georgian bus. Free wi-fi & default router credentials are included 😏 #wifi #defaultcredentials
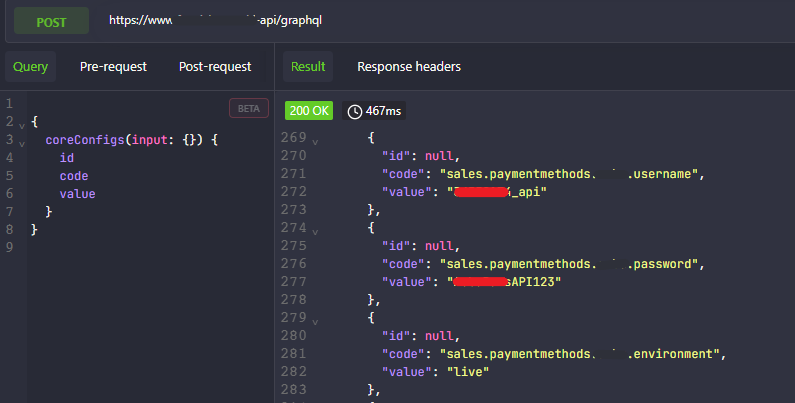
Fresh one. Leakage of payment gateway API credentials through Access Control Violation in GraphQL. #hacking #pentest #bugbounty #vapt #hackerone #owasp
Yay, I was awarded a $500 bounty on @Hacker0x01! hackerone.com/konqi #TogetherWeHitHarder Kinda back to H1. next step is to get clear badge
Check out my new blog post on RCE through Grafana 🔥 medium.com/@konqi/exploit… #pentest #bugbounty #bugbountytip #hacking #grafana
New Ivanti XXE seems promising (CVE-2024-22024) #pentest #bugbounty #synack #hackerone #ivanti

Atlassian Confluence Remote Code Execution through OGNL Injection. CVE-2023-22527 #atlassian #bugbounty #hacking #pentest #confluence

Apache Struts 2 OGNL Injection (CVE-2013-2251) leading to Remote Code Execution. Found this one today during a Pentest. #bugbounty #hacking #pentest #struts #burpsuite

Just found GraphQL broken access control leading to administrator credentials disclosure. Here's how to avoid: 1) Implement Proper Authentication & Authorization mechanisms 2) Disable Introspection & field suggestion if API is not for public use #pentest #bugbounty #hacking

Found my tweet from 2017
I always used to joke that if there was an RCE in Log4J all hell might break lose. Yikes ! cve.mitre.org/cgi-bin/cvenam…
➡️Default creds for #redteam Cisco: cisco:cisco Citrix: nsroot:nsroot Dell iDRAC: root:calvin Juniper: super:juniper123 pfSense: admin:pfsense SAP: SAP*:06071992 Tomcat: tomcat:tomcat UniFi: ubnt:ubnt Weblogic: weblogic:weblogic1 Zabbix: Admin:zabbix #ptswarmTechniques

Just got my swag pack from @SynackRedTeam for participation in Hacker Hangout Europe! #bugbounty #Synack

Check out Easy Hack manual from @ptswarm #pentest #bugbounty
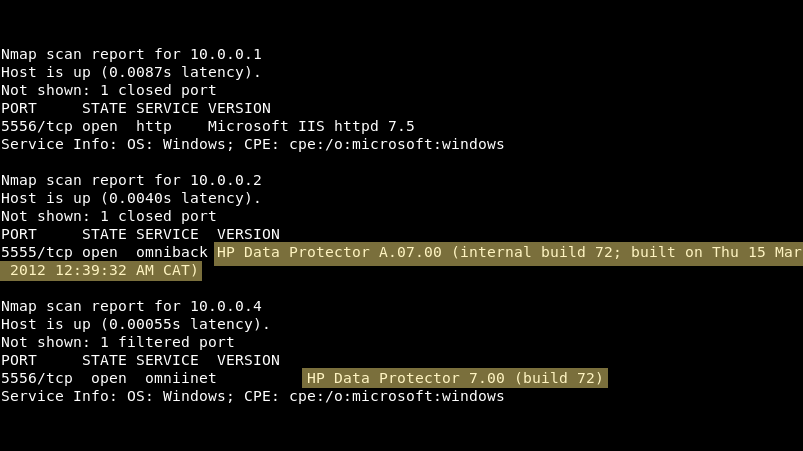
💥Easy RCE Ports Java RMI: 1090,1098,1099,4444,11099,47001,47002,10999 WebLogic: 7000-7004,8000-8003,9000-9003,9503,7070,7071 JDWP: 45000,45001 JMX: 8686,9012,50500 GlassFish: 4848 jBoss: 11111,4444,4445 Cisco Smart Install: 4786 HP Data Protector: 5555,5556 #ptswarmTechniques
The story how I found RCE in Citrix (CVE-2019-19781)
Read this article about CVE-2019-19781 RCE in Citrix by its author, Mikhail Klyuchnikov: swarm.ptsecurity.com/remote-code-ex…

The results are in...congrats to our #HackerHangout Europe winner, Ozgur - @ozgur_bbh 🏆! And extra shout outs to our top SRT runner(s) up: 2. Konqi - @0xKonqi 3. MrTuxRacer - @MrTuxracer 4. Papyrus - @A_Burak_Gokalp 5. s0rtega - @s_0rtega
Virtual HackerHangout Europe with @SynackRedTeam Like: #hackerhangout #road2tokyo #BugBounty #synack

United States Trends
- 1. UConn 8.697 posts
- 2. Jack Smith 134 B posts
- 3. Dan Hurley 1.267 posts
- 4. Solo Ball 1.111 posts
- 5. Tyrese Hunter N/A
- 6. lana 56,1 B posts
- 7. Maui 7.465 posts
- 8. Penny Hardaway N/A
- 9. Mahaney N/A
- 10. Kreider 3.930 posts
- 11. Samson 4.702 posts
- 12. Harrison Barnes 1.431 posts
- 13. Newcastle 24,5 B posts
- 14. #ysltrial 4.814 posts
- 15. Baymax 13,1 B posts
- 16. COTLTOOZ 1.221 posts
- 17. #Thanksgiving 16,2 B posts
- 18. Judge Chutkan 4.390 posts
- 19. Andretti 6.156 posts
- 20. West Ham 14,2 B posts
Who to follow
-
 mohammed eldeeb
mohammed eldeeb
@malcolmx0x -
 Uranium238
Uranium238
@uraniumhacker -
 Mahmoud Gamal
Mahmoud Gamal
@Zombiehelp54 -
 streaak
streaak
@streaak -
 nikhil(niks)
nikhil(niks)
@niksthehacker -
 pwnmachine
pwnmachine
@princechaddha -
 Parth Malhotra
Parth Malhotra
@Parth_Malhotra -
 Sergey Bobrov
Sergey Bobrov
@Black2Fan -
 Wh11teW0lf
Wh11teW0lf
@Wh11teW0lf -
 Paresh
Paresh
@Paresh_parmar1 -
 Yogendra Jaiswal
Yogendra Jaiswal
@vulnh0lic -
 jackds
jackds
@jackds1986 -
 harisec
harisec
@har1sec -
 Rakesh Mane
Rakesh Mane
@RakeshMane10 -
 Karel Origin
Karel Origin
@Karel_Origin
Something went wrong.
Something went wrong.































































































































