
PhishTool
@PhishToolThe phishing analysis platform.
Similar User

@SecBlueTeam

@BlueLabsOnline

@CyberDefenders

@HackerSploit

@LetsDefendIO

@4n6lady

@carrier4n6

@ISC2_Japan

@Recon_InfoSec

@RedDrip7

@SecHubb

@RangeForce

@DfirDiva

@CyberWarship

@InnocentOrg
PhishTool has just turned 3 years old! 🎂 How fitting - we have just released PhishTool v3! A major, major update, making phishing analysis even faster and more detailed. Check out PhishTool v3 now! app.phishtool.com
Cyber security colleagues - Why not take a break from the #Log4j2 nightmare to analyse some phishing emails?
Phishing playbook for SOC teams #blueteam gitlab.com/syntax-ir/play…

⚠️Your organisation is at serious risk without the right strategy and tool to defend against #phishing Stop simply ticking ☑️ compliance check boxes, get stuck in with a proper anti-phishing weapon: phishtool.com
Features! There are so many we are working on. You can find out what phish-destroying functionality we have coming up in our public roadmap 🗺 trello.com/b/wnOhoSg8/phi…
PhishTool combines threat intelligence, email metadata and automated analysis pathways into one powerful #phishing response platform. Making your organisation a formidable adversary - immune to phishing campaigns that those with lesser email security capabilities fall victim to.
Would you find instructional videos on phishing email and attachment analysis useful? Give us a ❤️ if the answer is yes, or a 🔄 either way 😜
We’ve been tracking a phishing campaign that has been using open redirects for months, and it continues to evolve and persist. As recently as last week, we detected a spam run that abused a different web app but utilized the same TTPs and infrastructure.
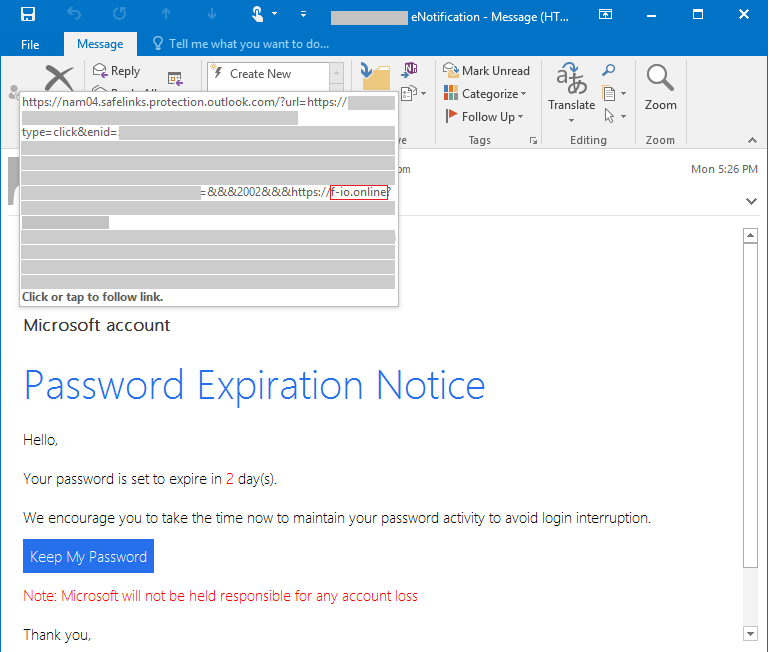
If your organisation 🏢 doesn’t see #phishing as a problem, it’s likely because end users 🧑💻 aren’t reporting enough. User engagement is key 🔑, and we are about to release some functionality that dials user engagement up to 1️⃣1️⃣, automagically 😉
After careful consideration we have decided to announce that we are going to absolutely destroy #phishing Come and see PhishTool.com
What an incredible series of mile stones… Thank you to our incredible users and organisations fighting #phishing with us every single day! 🎉 ✅ 5000+ phishing investigations! ✅ ~1000 PhishTool users! ➡️ Get involved phishtool.com
Our technology rips apart 🪚 #phishing emails, revealing 🔎 everything you need to defeat them. What are you waiting for? PhishTool Community is now completely free! Get it here: phishtool.com/products/commu…
Consent phishing attacks, which aim to trick users into granting malicious cloud apps access to sensitive data, are steadily increasing. Microsoft provides comprehensive protection against these attacks by coordinating defense across multiple solutions. microsoft.com/security/blog/…
The world 🌍 cannot afford 💵 to take #phishing lightly. We are building a uniquely powerful weapon against the criminals targeting 🎯 our businesses 🏢 and institutions 🏛. Start defending against phishing now with PhishTool.com
PhishTool is to #phishing as a disassembler is to malware or a forensic toolkit is to file systems. Start reverse engineering phishing campaigns with PhishTool now phishtool.com
Sometimes humans just do it better. #Phishing reverse engineering for humans with PhishTool. Timely and accurate, find out how humans (with machine assistance) are fighting back against phishing phishtool.com
Which #phishing response platform can detect sophisticated campaigns without malicious URLs or attachments? We can! Automated detection of chained social engineering tactics… that’s us!
United States Trends
- 1. Thanksgiving 1,26 Mn posts
- 2. $cuto 6.248 posts
- 3. Thankful 241 B posts
- 4. Turkey Day 28,6 B posts
- 5. #Gratitude 8.713 posts
- 6. #Grateful 4.729 posts
- 7. Al Roker N/A
- 8. Feliz Día de Acción de Gracias 2.350 posts
- 9. Vindman 97,6 B posts
- 10. Jimmy Fallon 1.316 posts
- 11. Gobble Gobble 14,8 B posts
- 12. The Outsiders 2.311 posts
- 13. #Butter1BillionOnYT 21,5 B posts
- 14. #AskZB N/A
- 15. Billy Porter N/A
- 16. Death Becomes Her N/A
- 17. Minnie Mouse N/A
- 18. Go Lions 1.754 posts
- 19. Hoda 1.100 posts
- 20. #givethanks 1.621 posts
Who to follow
-
 Security Blue Team
Security Blue Team
@SecBlueTeam -
 Blue Team Labs Online
Blue Team Labs Online
@BlueLabsOnline -
 CyberDefenders®™
CyberDefenders®™
@CyberDefenders -
 HackerSploit
HackerSploit
@HackerSploit -
 LetsDefend
LetsDefend
@LetsDefendIO -
 4n6lady
4n6lady
@4n6lady -
 Brian Carrier
Brian Carrier
@carrier4n6 -
 ISC2_Japan
ISC2_Japan
@ISC2_Japan -
 Recon InfoSec
Recon InfoSec
@Recon_InfoSec -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 John Hubbard
John Hubbard
@SecHubb -
 RangeForce
RangeForce
@RangeForce -
 DFIR Diva
DFIR Diva
@DfirDiva -
 Florian Hansemann
Florian Hansemann
@CyberWarship -
 The Innocent Lives Foundation
The Innocent Lives Foundation
@InnocentOrg
Something went wrong.
Something went wrong.

































































