Linux Live Analysis Knowledge Base, Tips & Tricks w0-0p.github.io/Linux-Forensic…
I’d love to see @CISAgov publish a ‘Top 10 Vendors’ list for releasing products with serious, frequently exploited vulnerabilities (CVSS > 8.5). It’d be a data-driven ‘wall of shame’ based on their exploited vulnerability reports. If they won’t do it, I might. And if a vendor…
🚨 Fortinet CVE-2024-23113 - actively exploited by state-sponsored hackers - is now being exploited by cybercriminals who have reverse-engineered it and are selling access to compromised devices If you haven't patched, restrict port 541 to approved IPs or enforce cert auth.

If you add a . (dot) before a file name, it becomes hidden in Linux. That's not a secret. But do you know that this "feature", was actually a bug?

Decoding Anti-Virus Detection Names For Malware Analysts: digitalinvestigator.blogspot.com/2024/11/decodi… #malwareanalysis #infosec #informationsecurity #dfir #reverseengineering #malware #cybersecurity
Our talk from @defcon is now available! In the presented research, we document every EDR bypass technique used in the wild along with how to detect it using new memory forensics techniques and @volatility plugins. Feedback appreciated! youtube.com/watch?v=PmqvBe… #DFIR
🚨EDR Telemetry website is live! 🥳 I hope this makes it even easier for folks to compare the telemetry of EDR vendors and visualize their visibility gaps 🙂 ‣ Website🔗edr-telemetry.com ‣ GitHub 🔗github.com/tsale/edr-tele… **Telemetry results reflect the most recent…

I created the first draft of a website for the EDR telemetry project to help people quickly compare vendor telemetry visibility. What do you think about it? Are there any specific features you want to see for the website? Built with ChatGPT 4o with canvas (wanted to test it…
PowerShell Command History Forensics #DFIR vikas-singh.notion.site/PowerShell-Com…
I wanted to learn more about using content delivery networks (CDNs) in Azure in conjunction with an Nginx reverse proxy in the context of using Cobalt Strike as a C2 framework. As a result, I've written the following blog post. redops.at/en/blog/cobalt… #redteam
Extracting Credentials From Windows Logs practicalsecurityanalytics.com/extracting-cre…
really excited about LockBit's new certification, CBTO (Certified Black Team Operator) Black Team Ops is an online, self-study course that teaches core concepts of being an adversary, including configuration of cracked cobalt strike, money laundering, and RAAS payload deployment
I had a great time to learn how to deploy and use Timesketch. Honestly, I am parsing Windows event logs by Hayabusa and importing them to Timesketch. Unfortunately, the graph plugins do not work. I decided to customize the plugin to work. github.com/n0bit4lsm3/Tim…
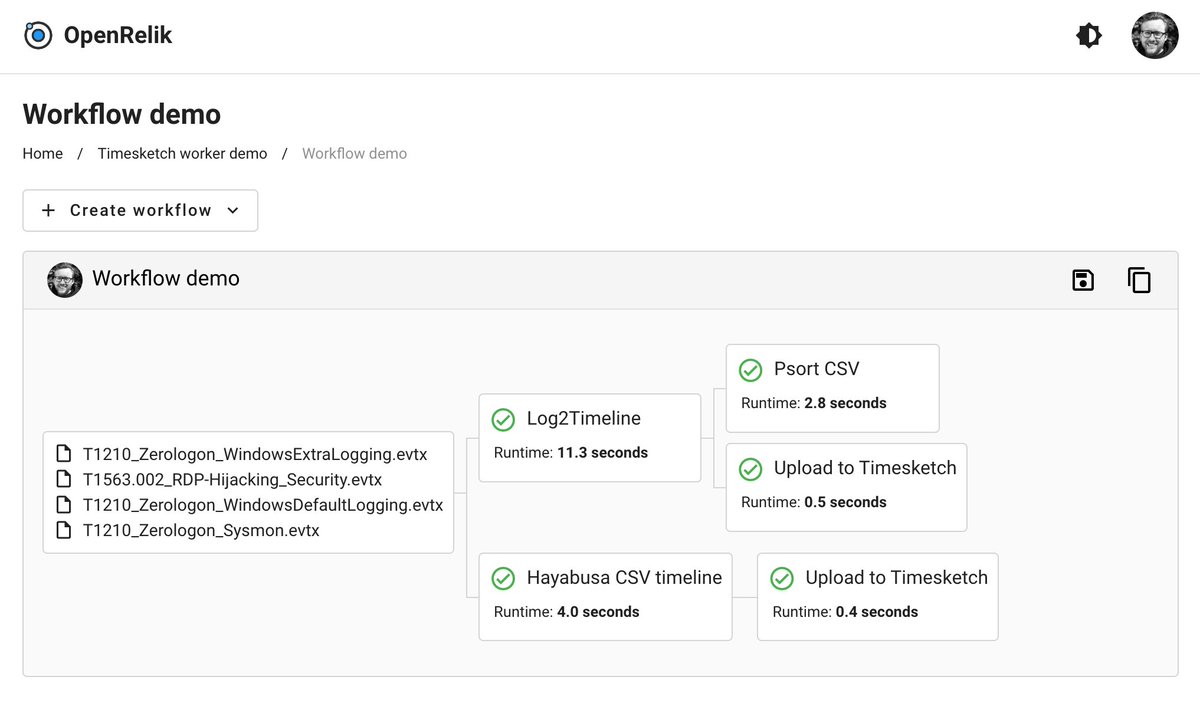
Two new OpenRelik workers released today: 1. Hayabusa from @SecurityYamato - Analyze your Windows Event Logs. 2. Timesketch exporter - export your timelines seamlessly. #DFIR #OpenRelik 🧵👇See this thread for screencasts:
#DFIR lessons learned are the best #cybersecurity “best practice” #TrustEverybodyButCutTheCards #Kudos to #Microsoft DART and welcome to #IncidentResponse Ninja Hub: techcommunity.microsoft.com/t5/microsoft-s… #mustread #incidentresponse #threathunting #TrustEverybodyButCutTheCards


The #linux detection engineering saga continues! Breakdown persistence techniques both simple and complex in this new article from @RFGroenewoud: go.es.io/3X6w7k9 #ElasticSecurityLabs #detectionengineering
The best way to learn how real threat actors operate is to read the many published threat reports on their activity DFIR Report thedfirreport.com APT Groups and Operations docs.google.com/spreadsheets/d… ORKL orkl.eu/sources I’ll add more links in the replies 🧵
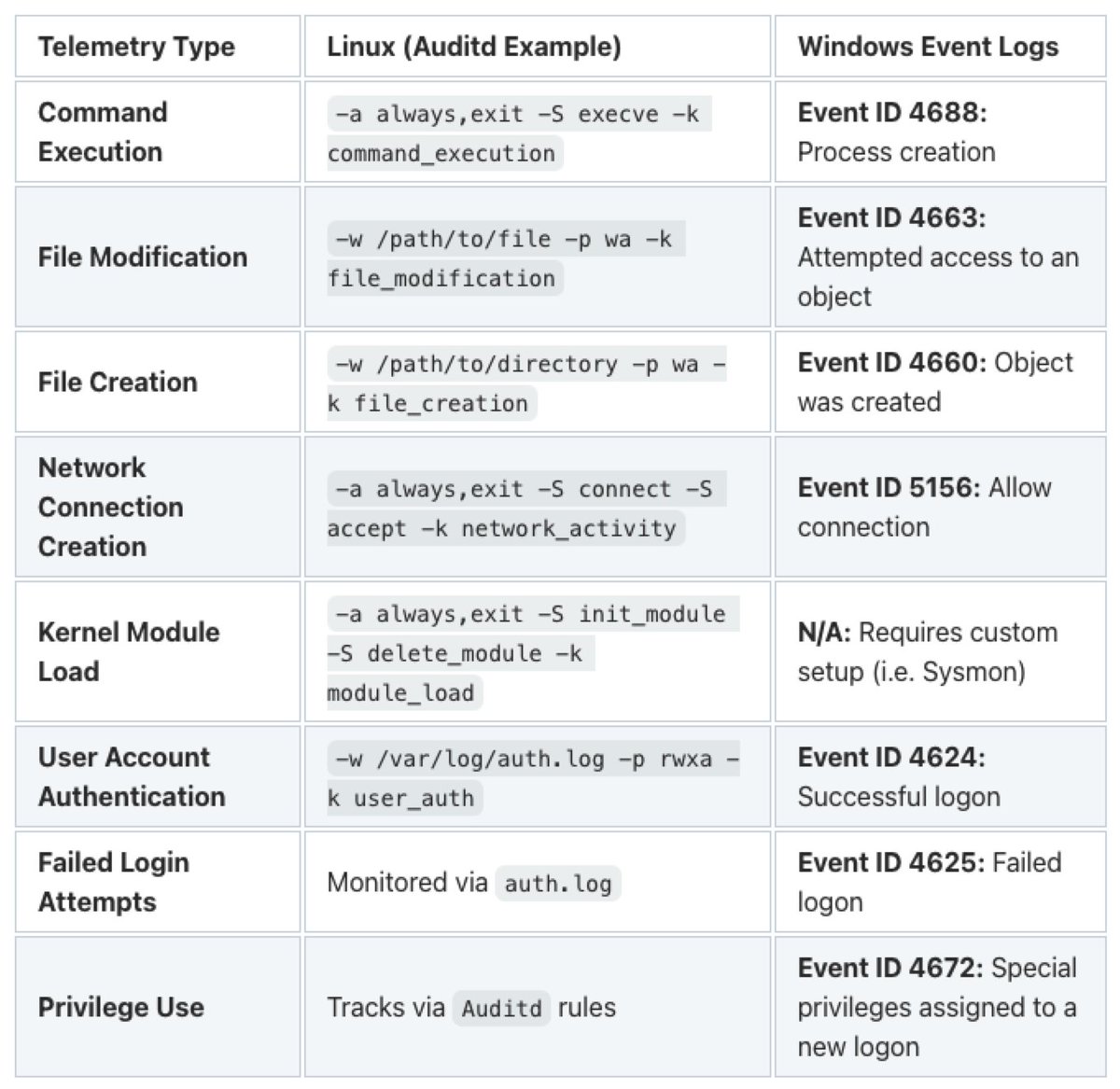
If you're interested in getting into #Linux #logging and evidence collection, this is an excellent write-up from @Kostastsale that compares #EVTX logs on Windows with #Auditd, #SysMon for Linux, and native Linux logging. #DFIR #LinuxForensics #SIEM #CSIRT kostas-ts.medium.com/telemetry-on-l…
* Always check open file descriptors per process, because there you can find other interesting differences * Use simple Yara rule + Velociraptor's Linux.Detection.Yara.Process to hunt at scale easily

#OSINT #SOCMINT At the request of many, I share with you an almost complete tool called “OSINT Investigation Assistant”, which contains a large set of useful resources for OSINT, categorized by #tags. ➡️ RESOURCE: lambda.black/osint.html Source: t.me/irozysk/13331

United States Trends
- 1. #OnlyKash 34,9 B posts
- 2. Jaguar 48,6 B posts
- 3. Joe Douglas 10,6 B posts
- 4. $MOOCAT 1.574 posts
- 5. Embiid 22,5 B posts
- 6. Maxey 14,5 B posts
- 7. Rodgers 13,2 B posts
- 8. Nancy Mace 64,2 B posts
- 9. Woody 15,3 B posts
- 10. Jets 43,1 B posts
- 11. #HMGxCODsweeps N/A
- 12. #HowToTrainYourDragon 16,1 B posts
- 13. Cenk 11,2 B posts
- 14. Howard Lutnick 18,4 B posts
- 15. #ysltrial 6.423 posts
- 16. Toothless 15,5 B posts
- 17. B-52 1.943 posts
- 18. Zach Wilson 1.653 posts
- 19. Saleh 19,5 B posts
- 20. Sarah McBride 58,3 B posts
Something went wrong.
Something went wrong.