Chí Thành 🇻🇳
@JackLy09280371Try to learn about Malware Analysis, Reverse Engineering
Similar User

@huongntl31

@KMA_Akai

@erichoang851

@cookiehanhoan

@c0nc4nh0

@tacbliw

@biennd279

@n1c3gu7

@xamvi_

@h4d3s101

@1943Reisen
.@TrendMicro kudos to the team that put this together. 180+ page report - Exploring forensic evidence and detection methods for remote monitoring and management (RMM) tooling. Also including common sync tools used in incidents. jsac.jpcert.or.jp/archive/2023/p… #DFIR #RMM




Malware: #Rhadamanthys & #XMRig found on @YouTube 🎥 🔗 Malicious software distribution: youtube.com/@Download-Link… 🖥️C2: 185.221.196[.81/api/endpoint.php 🐍 Hydra Panel: 185.221.196[.81/login.php 🔍 Analysis: tria.ge/231122-n8f3dac… 📊🔬

I had a great time to learn how to deploy and use Timesketch. Honestly, I am parsing Windows event logs by Hayabusa and importing them to Timesketch. Unfortunately, the graph plugins do not work. I decided to customize the plugin to work. github.com/n0bit4lsm3/Tim…
Happy to share the release of my latest plugin for IDA Pro 🎉 - a tool for demangling Rust & Normalizing function names to make Reversing easier. github.com/timetravelthre…
📭We've added a PoC exploit msg file for CVE-2023-23397 here (UNC path is localhost!): delivr.to/payloads?id=49… 🔍 There's also a yara rule in our detections repo that identifies the PidLidReminderFileParameter set in a msg Appointment file: github.com/delivr-to/dete…


We've just published a quick write up on CVE-2023-23397, which allows a remote adversary to leak NetNTLMv2 hashes: mdsec.co.uk/2023/03/exploi… by @domchell

A powerful and open-source toolkit for hackers and security automation github.com/We5ter/Scanner…

I created a repository containing samples of code that explain the basic implementation of COM objects. If you have any feedback, please let me know. #cpp #windows #lowlevel github.com/0xMegaByte/COM…
How to analyse malicious MSI files E.g. this Magniber MSI virustotal.com/gui/file/fd597… It consists mostly of zeroes. 1. step: Unpack with 7zip. Among the unpacked files is a x64 DLL named "djrbwtwujn" But how is this DLL called?

🐞 Malware Development for Dummies In the age of EDR, red team operators cannot get away with using pre-compiled payloads anymore. As such, malware Slides: github.com/chvancooten/ma… Exercises: github.com/chvancooten/ma… #maldev #csharp #nim
1\ #ThreatHunting: How to detect Linux anti-forensics log tampering Attackers can alter the utmp, wtmp, btmp files to hide malicious logon attempts by: > Zeroing entries out in hex > Overwriting the files with a malicious copy BLOG POST BELOW 👇 UwU inversecos.com/2022/06/detect…
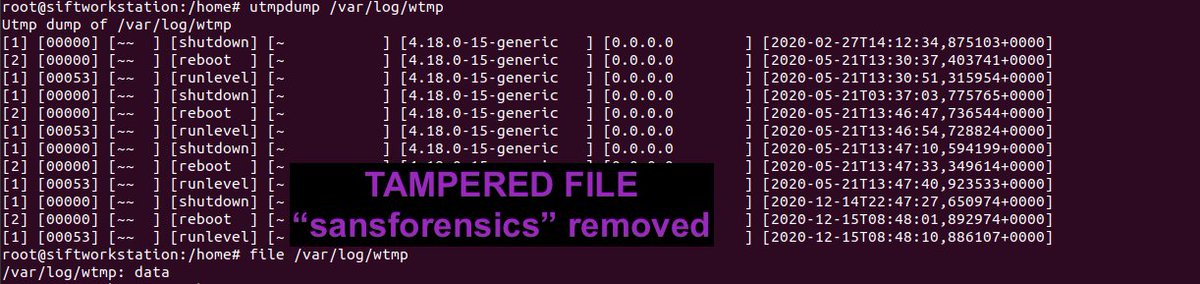

mitmhttp and mitmpcap tools to make capturing #malware TLS secrets and pcaps using #mitmproxy a breeze! gist.github.com/c3rb3ru5d3d53c… gist.github.com/c3rb3ru5d3d53c… Updated #KVM #Malware #Lab Guide: c3rb3ru5d3d53c.github.io/docs/kvm-malwa… TY to @reecdeep for the request Enjoy! 😇




Ultimate #Malware #Analysis #KVM Guide ✅ PFSense Router ✅ Remnux VM as Gateway ✅ Windows Dynamic Analysis VM ✅ Spice Agent and Guest Tools ✅ Anonymous VPN Networking ✅ List Malware Analysis Tools (my top picks) c3rb3ru5d3d53c.github.io/docs/kvm-malwa…

ProcEnvInjection - Remote code injection by abusing process environment strings in CreateProcess. Another method of injecting code into a remote process without using WriteProcessMemory. 🙂 x86matthew.com/view_post?id=p…
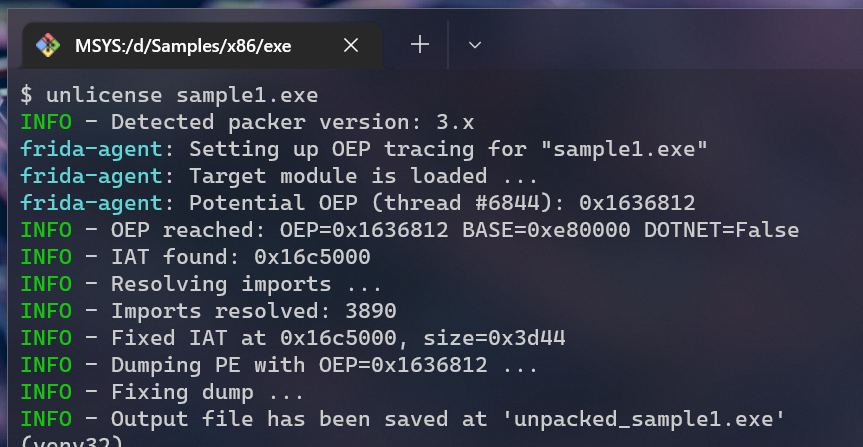
unlicense - A dynamic unpacker and import fixer for Themida/WinLicense 2.x and 3.x. Version 0.2.0 has been released. It adds support for DLL unpacking, .NET assembly unpacking (EXE only) and fixes a bug with some 2.x-packed EXEs. github.com/ergrelet/unlic…
I was playing around with @_JohnHammond fantastic POC for msdt/Follina on an endpoint with an EDR installed to see what's up and it pointed me towards this Registry key. I was not aware of it, but it seems to logs connections that are made by Office. General #DFIR Tip?


Process_Overwriting - Yet Another Variant Of Process Hollowing dlvr.it/SRG5tv #Process #Process_Overwriting #Windows

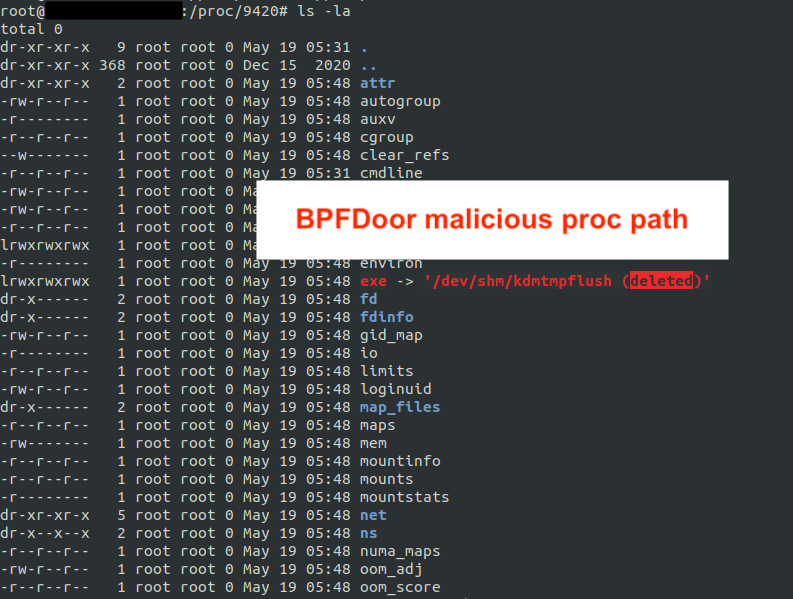
1\ #ThreatHunting: How to detect fileless Linux malware Look for processes in /proc/<PID>/exe where the path shows "(deleted)" Here are two examples👇 1. BPFDoor deleted binary 2. An attacker abusing memfd_create() to exec their malware in RAM w/o dropping files to disk.

⚠️New blog post: The Lotus Panda is awake, again. Analysis of its last strike. #APT #malware #cybersecurity cluster25.io/2022/04/29/lot…
Email header analysis for SOC Analysts

Analyzing a Stealer MSI using msitools, by @ForensicITGuy #DFIR forensicitguy.github.io/analyzing-stea…
Emotet Loader Technical Analysis nikpx.github.io/malware/analys…
United States Trends
- 1. #OnlyKash 59,6 B posts
- 2. Starship 201 B posts
- 3. Jaguar 64,4 B posts
- 4. Celtics 17,9 B posts
- 5. Nancy Mace 89,2 B posts
- 6. Sweeney 12 B posts
- 7. SpaceX 216 B posts
- 8. Medicare and Medicaid 25,7 B posts
- 9. Jim Montgomery 4.186 posts
- 10. Jose Siri 2.931 posts
- 11. Dr. Phil 8.679 posts
- 12. Linda McMahon 3.843 posts
- 13. $MCADE 1.373 posts
- 14. Stephen Vogt 1.362 posts
- 15. Dr. Mehmet Oz 8.216 posts
- 16. Monty 11,5 B posts
- 17. #LightningStrikes N/A
- 18. Cenk 15,3 B posts
- 19. #SpiteMoney N/A
- 20. Lichtman 1.407 posts
Something went wrong.
Something went wrong.