Crypt0s
@Crypt0sApplication security guy who dabbles in radios, networking, protocols…pretty much anything anyone puts in front of me to hack!
Similar User

@ihackedwhat

@sno0ose

@n00bznet

@SecBarbie
@attritionorg

@iiamit

@magen_wu
@grecs

@Wh1t3Rabbit

@ForgottenSec

@Jabra

@McGrewSecurity

@DaveMarcus

@pwcrack

@gdead
Confused about DMR? Fustrated you can't get your hotspot configured? Need some help? Here is a quick tutorial: medium.com/@Crypt0s/how-t… #DMR #hamradio #brandmeister #mmdvm
1/12 It has been confirmed that the #Taurus interception was done via “a non-secure line”. Below is my opinion of one way in which it *might* have been done, taking into account the situation and #Russia's previous history. Essentially it involves using #SS7 interception. 🧵

Lenovo X1 Carbon Bitlocker Key Sniffing any% Speedrun (42.9 seconds)
OST cannot be stopped. Here is a technique we tested internally 9 months ago: blocking EDR telemetry by leveraging the Windows Filtering Platform. Considered it so evil that we didn't publish it that time. It was pointless, now here it is by @netero_1010: github.com/netero1010/EDR…
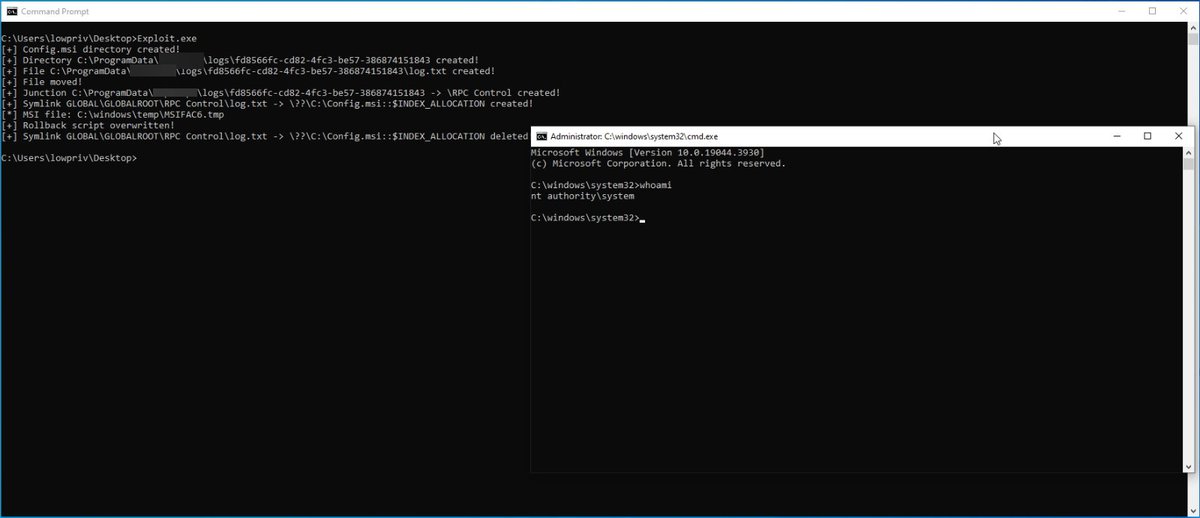
Discovered and exploited an arbitrary file delete vulnerability that lead to SYSTEM level privileges. Thanks to the goat @filip_dragovic
The best thing about generative AI is that I hear far far less about Web3 bullshit
Are we really not supposed to double space after a period anymore???????
Red, Blue, and Purple LDAP Queries. Quite useful. politoinc.com/post/ldap-quer…
Very cool explanation of CANbus theft technique
There is no software update, the theft is via 'CAN injection 🚘💉' See kentindell.github.io/2023/04/03/can… for more details.
New blog: Obtaining Domain Admin from Azure AD by abusing Cloud Kerberos Trust I teased this a bit during my Windows Hello talks, now found some time to write about this interesting technique. Also contains defenses and detection opportunities. dirkjanm.io/obtaining-doma…
A certificate reseller bypassed the HTTP verification of the ACME cert protocol by using a remote code injection in ACME.sh to write their own When called out they are surprised Pikachu and say they didn’t know what an RCE was before this. 😬
🍿🍿🍿 CA dId NoThInG wRoNg (they built a product around an 0day in a certificate management tool, got caught, and I'm hoping this results in a root CA being incinerated because that would be funny) groups.google.com/a/mozilla.org/…
I'd be pretty interested see how it fares with my new SDR Bluetooth sniffer and a bladeRF. Can it perform all-channel sniffing in real time? Benchmark with ice9-bluetooth -s -f /dev/urandom github.com/mikeryan/ice9-…
It’s like nobody has ever tried to execute a docker container inside of an existing network namespace before
"Espressif ESP32: Bypassing Encrypted Secure Boot (CVE-2020-13629)" raelize.com/blog/espressif…
Not for a hot minute tho right? Like part of fuzzing could be the AI can generate the test harness but that’s a far cry from current “coding ability” of AI I’ve seen so far. And web is such a hot mess of different stuff… Maybe in 2-3 years?
Generative AI aided fuzzing will lead to more binary and web exploits. Both defense and offense will benefit from this.
United States Trends
- 1. Thanksgiving 673 B posts
- 2. #AEWDynamite 12,7 B posts
- 3. #Survivor47 1.917 posts
- 4. Zuck 7.529 posts
- 5. #BillboardIsOverParty 107 B posts
- 6. Custom 85 B posts
- 7. Vindman 40,8 B posts
- 8. Kamille 2.008 posts
- 9. #CONVICT 6.938 posts
- 10. Azzi 2.372 posts
- 11. James Harden 4.520 posts
- 12. Shelton Benjamin 1.085 posts
- 13. Ishii 2.860 posts
- 14. Mbappe 442 B posts
- 15. Marcus Smart N/A
- 16. Jericho 3.823 posts
- 17. #spatchcock N/A
- 18. Max Caster N/A
- 19. Genevieve 3.342 posts
- 20. Verify 30,3 B posts
Who to follow
-
 Render Man
Render Man
@ihackedwhat -
 Sno0ose
Sno0ose
@sno0ose -
 n00bz
n00bz
@n00bznet -
 Erin Jacobs
Erin Jacobs
@SecBarbie -
 jericho
jericho
@attritionorg -
 Ian
Ian
@iiamit -
 Magen Wu
Magen Wu
@magen_wu -
 grecs (at #shmoocon)
grecs (at #shmoocon)
@grecs -
 Rafał Łoś 🇵🇱 🇺🇦
Rafał Łoś 🇵🇱 🇺🇦
@Wh1t3Rabbit -
 Forgotten
Forgotten
@ForgottenSec -
 Josh Abraham
Josh Abraham
@Jabra -
 Dr. Wesley McGrew
Dr. Wesley McGrew
@McGrewSecurity -
 Biggles McSwole The Zionist Dolphin
Biggles McSwole The Zionist Dolphin
@DaveMarcus -
 Robert Weiss
Robert Weiss
@pwcrack -
 Bruce Potter
Bruce Potter
@gdead
Something went wrong.
Something went wrong.