Similar User

@G3tSyst3m

@rover_ninja

@Gwyomarch

@ariocosta

@a_denkiewicz

@Lizardqueen954

@castilho101

@sergiopedro_99

@w3th4nds

@andr0idp4r4n0id

@s3np41k1r1t0

@ghostpwner

@nunomcoelho

@_nunohumberto

@bl4ck_pwn
While loop without an exit condition in real life 😅
Something like this yeah 😂😂
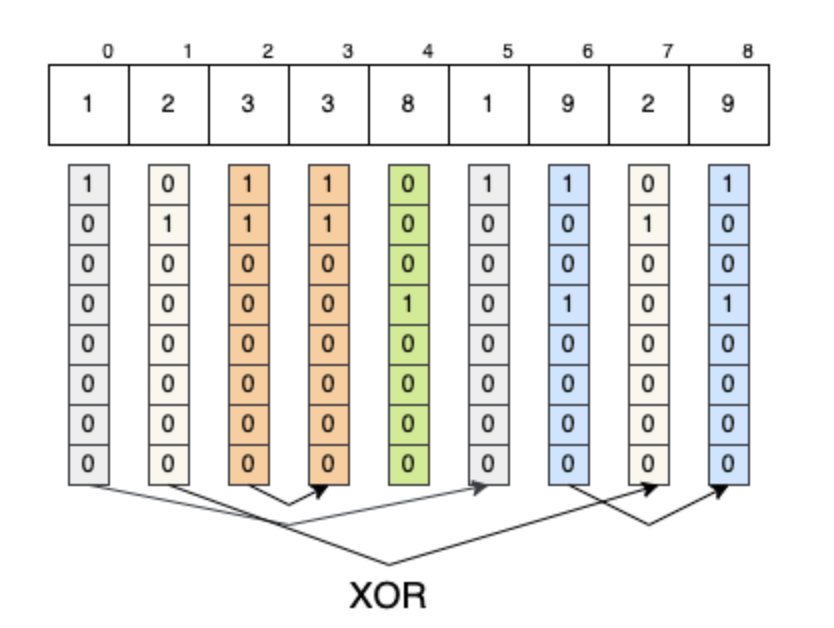
1/5: There is a quick explanation about this payload for the people who are asking: Certainly, here's a more detailed tweet comment explaining the payload: This payload is an attempt to bypass WAF. It disguises 'echo' and uses '$IFS' to evade detection.
All my current bug bounty knowledge is gone. Here's how I get it back and make $100k in the first year: First, I've got to learn the basics. For this, I will make sure I understand at a high level how the components I'm working with function. I'll need to understand...

Here is a meme that was shared by a group of disassembler enthusiasts.

The Security Reference Guide by @s0cm0nkeysec is an excellent, well-curated and well-organised repository of cybersecurity resources! 👇 s0cm0nkey.gitbook.io/s0cm0nkeys-sec…
My talk is now available on youtube. Thanks @owasplisboa, for giving me the opportunity to share my experience. youtube.com/watch?v=l_ODT7…
Finding 0-day vulnerabilities in apps using the Red Team approach redteamrecipe.com/Finding-0-day-… `if ($credential == 'password') {` Probably vulnerable to type juggling and should be `if ($credential === 'password') {` #redteam #redteamrecipe #appsec #codeql
<3 <3 <3
So far I've written 559 pages to help the security community: 1. exploitreversing.com/2021/12/03/mal… 2. exploitreversing.com/2022/02/03/mal… 3. exploitreversing.com/2022/05/05/mal… 4. exploitreversing.com/2022/05/12/mal… 5. exploitreversing.com/2022/09/14/mal… 6. exploitreversing.com/2022/11/24/mal… 7. exploitreversing.com/2023/01/05/mal… 8. exploitreversing.com/2023/04/11/exp…
Analysis and exploitation of a buffer overflow vulnerability (CVE-2022-47949) in Nintendo games network code by @Pablomf6 github.com/PabloMK7/ENLBu… #cybersecurity


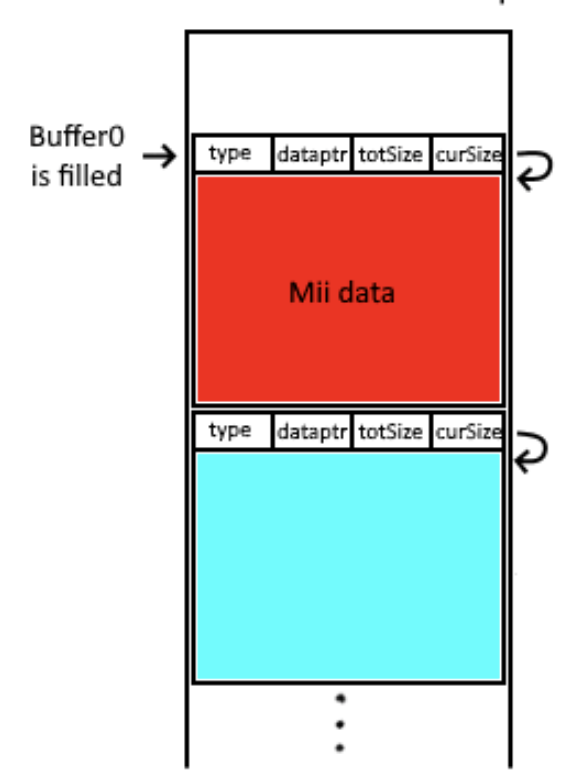
Excellent introduction to Linux kernel exploitation Series by @k3170Makan Debugging with QEMU: blog.k3170makan.com/2020/11/linux-… Stack Overflows: blog.k3170makan.com/2020/11/linux-… RIP control: blog.k3170makan.com/2021/01/linux-… #cybersecurity

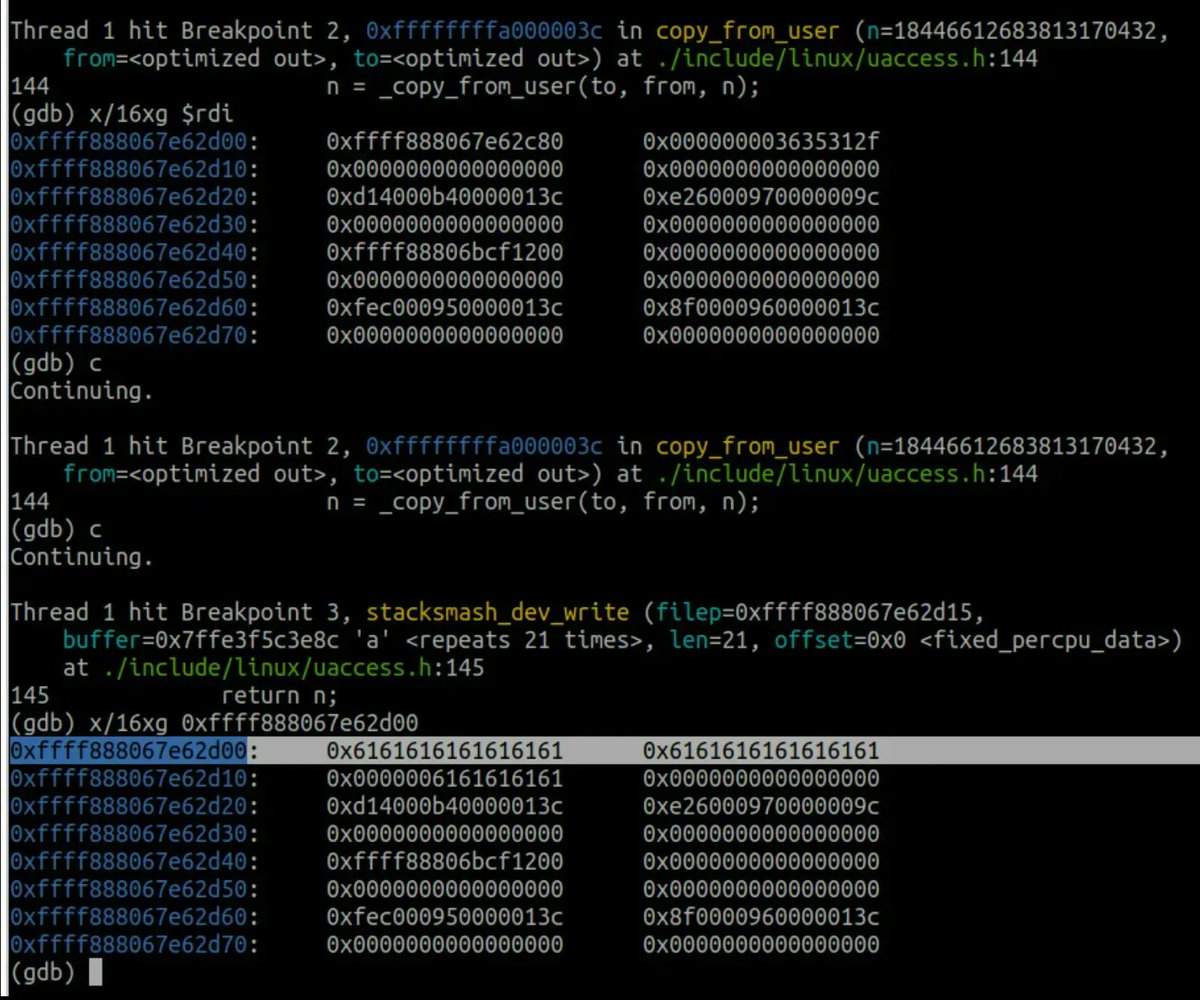

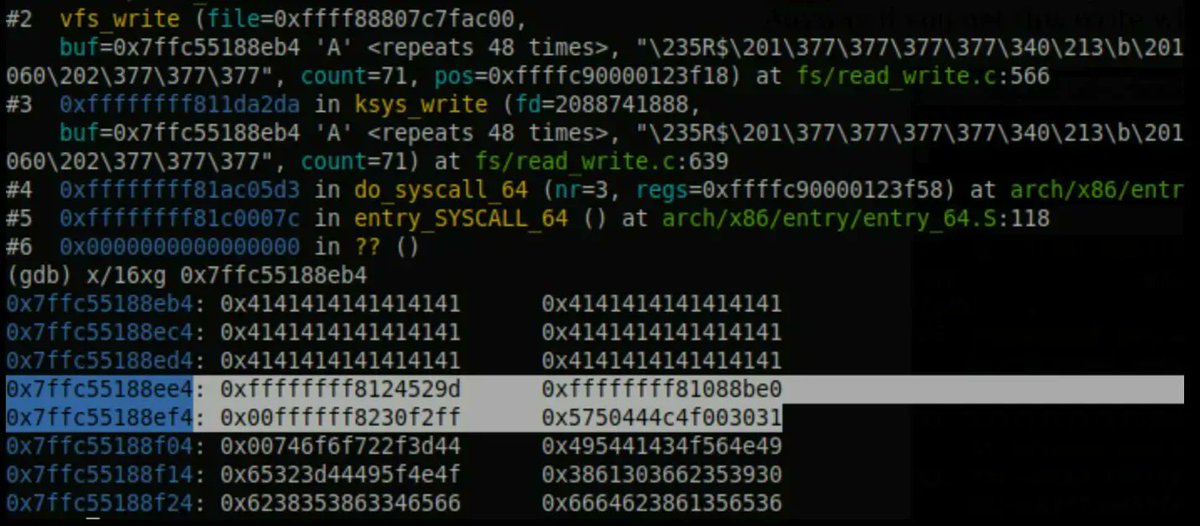
Great blog post for beginners on bitwise operations in C by Andrei Ciobanu andreinc.net/2023/02/01/dem… #infotech



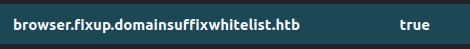
If you play CTFs with a fake TLD (like *.htb), you're probably used to typing siteisup.htb into firefox and getting a google search. Just learned you can add this key in about:config, and now it will stop searching! support.mozilla.org/en-US/question… I'm overly excited about this.
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec

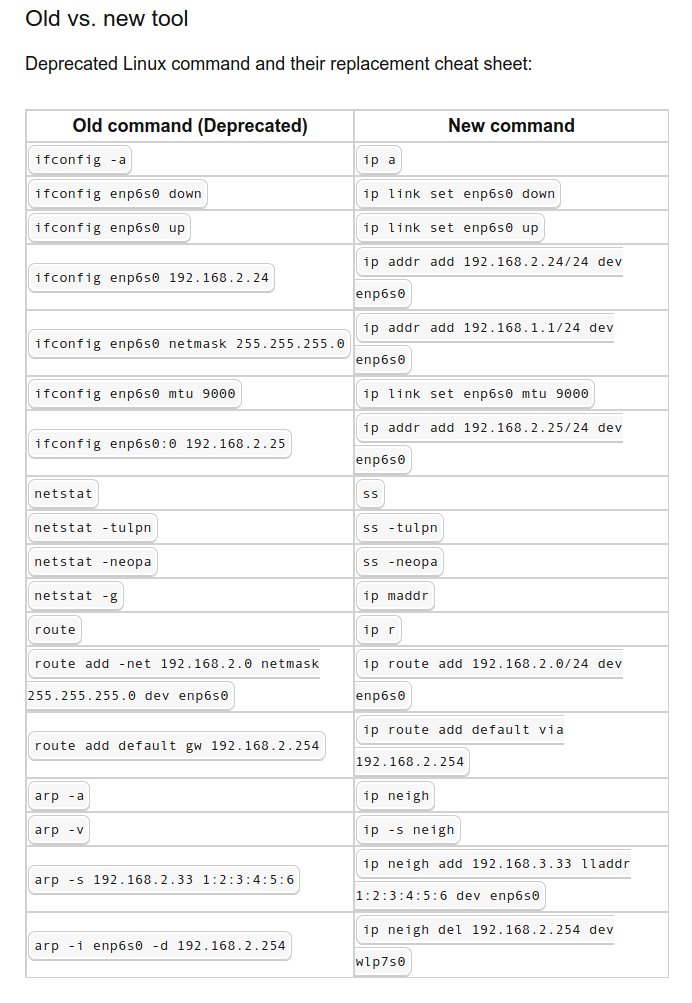
Old vs New Linux Commands #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec #networking #networksecurity #CheatSheet #infosecurity #cyberattacks #security #linux #hacker #vulnerabilities #bugbounty #bugbountytips
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec

That's how you do it, EASYYYY
United States Trends
- 1. Dalton Knecht 46,3 B posts
- 2. Lakers 60,9 B posts
- 3. #LakeShow 5.545 posts
- 4. Jay Leno 4.170 posts
- 5. $QUANT 11,2 B posts
- 6. Hampton Inn 1.812 posts
- 7. Spurs 16,7 B posts
- 8. Jaguar 116 B posts
- 9. #DWTS 26,8 B posts
- 10. Linda McMahon 43,1 B posts
- 11. #RHOBH 11 B posts
- 12. Cavs 52,5 B posts
- 13. Celtics 59,6 B posts
- 14. Dorit 5.492 posts
- 15. Chris Paul 2.982 posts
- 16. Cenk 31 B posts
- 17. Chase U 6.112 posts
- 18. Reaves 5.552 posts
- 19. Tatum 34,9 B posts
- 20. Honduras 49,2 B posts
Who to follow
-
 R.B.C.
R.B.C.
@G3tSyst3m -
 Dharmendra Lakhara
Dharmendra Lakhara
@rover_ninja -
 Gwyomarch
Gwyomarch
@Gwyomarch -
 ARioCosta
ARioCosta
@ariocosta -
 Adrian Denkiewicz
Adrian Denkiewicz
@a_denkiewicz -
 Lizardqueen
Lizardqueen
@Lizardqueen954 -
 castilho
castilho
@castilho101 -
 Sérgio Pedro
Sérgio Pedro
@sergiopedro_99 -
 w3th4nds
w3th4nds
@w3th4nds -
 Francisco
Francisco
@andr0idp4r4n0id -
 Bruno Mendes
Bruno Mendes
@s3np41k1r1t0 -
 GhostPwner
GhostPwner
@ghostpwner -
 Nuno Mateus-Coelho
Nuno Mateus-Coelho
@nunomcoelho -
 Nuno Humberto
Nuno Humberto
@_nunohumberto -
 Pedro Bernardo
Pedro Bernardo
@bl4ck_pwn
Something went wrong.
Something went wrong.