Similar User

@alien0x_

@AlsadeqKareem

@0xHasanM

@FlEx0Geek

@0xbahaa

@0xMM0X

@Elawadly77

@serWazito0

@n3r0li

@Anubi5x0

@1nclud3

@SN1PER47

@XDev05

@m19o__

@irsheidat1
We got 6th in #BHMEA23 CTF over the week. Didn't manage to get top 5 but it was a close battle! Big congrats to @dicegangctf for winning + @Blackhatmea for the nicely organised event. We will come back stronger next year!

During the weekend, we participated in BRICS+ CTF Quals organized by C4T BUT S4D team and secured 1st place. As a reward, we also receive an invitation to compete in the 8th XCTF finals in China next year. We enjoyed the event and look forward to both upcoming finals!

Co-authoring Regexplore, a new @volatility 3 plugin, with ChatGPT😄 to bring Registry Explorer plugins' @EricRZimmerman tool to Volatility. 🛠️ Contribute and help improve its features!: github.com/0xHasanM/regex… 🔗 #Volatility #DigitalForensics #RegistryExplorer #ChatGPT
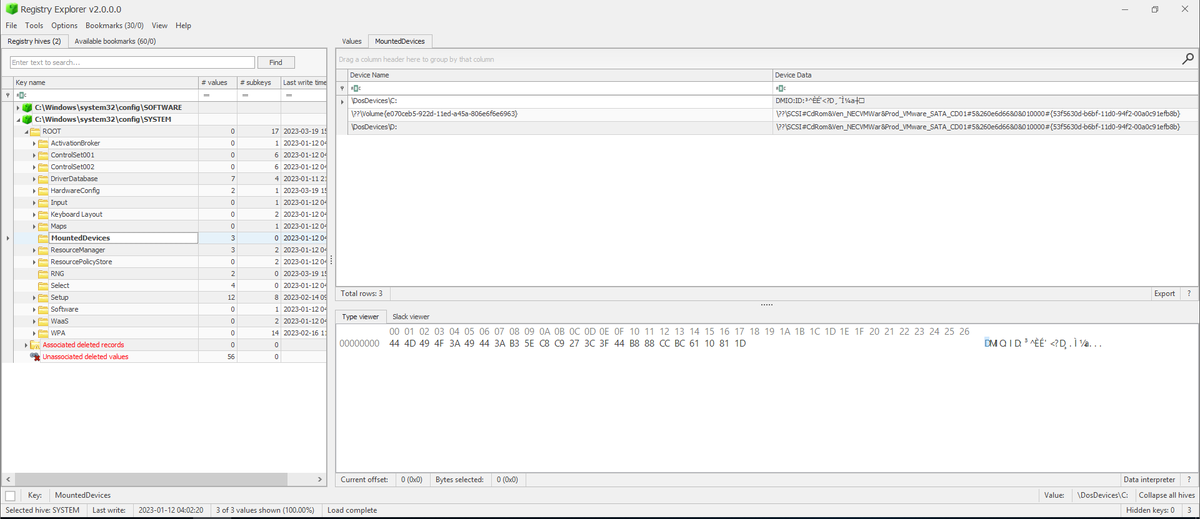

Defeating #dotRunpeX — New #virtualized .NET injector abusing advanced techniques to deliver numerous malware families. CP<r> provides an in-depth analysis of this threat introducing several PoC techniques for reversing protected/virtualized #dotnet code. research.checkpoint.com/2023/dotrunpex…
I've published 2 quick tutorials about writing #x64dbg scripts and plugins, hope you learn something new :) n1ght-w0lf.github.io/tutorials/writ… n1ght-w0lf.github.io/tutorials/writ…

Hi,I just published a write-up about how I solved Leaker challenge from WiCSME CTF 2022 and How I got RCE on XSLeak challenge ( Unintended Solution ) omakmoh.github.io/xsleak-is-2-wa…
Curious about C2 Development? Read my new blog post, where I showed how to implement External C2 like Cobalt Strike to let the operator operate through his custom communication channel. xret2pwn.github.io/Myths-About-Ex… Peace out! ✌ #Redteam #CyberSecurity

Hey everyone, I published a new blog about using #YARA for malware config extraction. I used #RedLine stealer for demonstration (extracting C2 and BotnetID). n1ght-w0lf.github.io/tutorials/yara…
Here we go again! Will randomly choose at end of next Monday 6/6 one person to attend the @cyber5w #CCDFA certification course LIVE with me starting June 13th. #DFIR #C5W All I ask you is to Retweet/RT, not even a like or follow!!! academy.cyber5w.com/courses/ccdfa-…
Thanks to @hackthebox_eu for the wonderful event, we managed to clear all challenges and stay in Top 5 :)

Two Parts of Access Token Manipulation, I just talked about How to steal token of another process, make token, revert token, and finally How to build a token vault to store your stolen tokens in memory. Part1 : xret2pwn.github.io/Access-Token-P… Peace out!✌️ #redteam
Bypassing CrowdStrike, Microsoft Defender for Endpoint etc. for fun.. not profit vanmieghem.io/blueprint-for-…

04 Windows Registry - DFIR | Digital Forensics & Incident Response الحلقة الرابعة من سلسلة التحقيق الجنائى الرقمى و الاستجابة للحوادث باللغة العربية. youtu.be/3SFNyFKKLCY #DFIR #dfirtip #امن_المعلومات
Really cool tool and awesome README that discusses in detail how EDR works (kernel callbacks, ETW, userland hooking, etc.) and how it can be bypassed with a vulnerable driver. They also put defensive considerations at the bottom! github.com/wavestone-cdt/…
It was a thrilling experience to participate as challenge creators in such an amazing event @athackcon #FwordFTW
Write-ups for 3 challenges from @CSAW_NYUTandon finals were we able to get 1st place as #Fword 🥇 1. lnkd.in/d4hpue9Z 2. lnkd.in/dWS-vuYJ 3. lnkd.in/d9wmTNmJ #dfir #CyberSecurity #infosec
We got 1st Place in @CSAW_NYUTandon CTF MENA 2021 Finals 🥳 This could not be done without the huge effort by all members through the Qualification Round and the Final Round. Thank you @DeadSec @Heaven's Bird @team7even1 for the great competition. #Fword


United States Trends
- 1. #SmackDown 48,3 B posts
- 2. #BlueBloodsFinale 5.464 posts
- 3. #iubb 1.406 posts
- 4. #OPLive 2.469 posts
- 5. #TheLastDriveIn 2.368 posts
- 6. Embiid 7.008 posts
- 7. Standard 106 B posts
- 8. Mike Woodson N/A
- 9. Michin 7.574 posts
- 10. Naomi 14,5 B posts
- 11. Paul George 2.327 posts
- 12. Reggie Bush N/A
- 13. Melo 23,1 B posts
- 14. Daylight Savings Time 15,6 B posts
- 15. Sweets 13,4 B posts
- 16. Braun 8.432 posts
- 17. Sixers 5.865 posts
- 18. Myles Rice N/A
- 19. Chelsea Green 3.645 posts
- 20. Mayorkas 17,8 B posts
Who to follow
-
 Hagar Yousef
Hagar Yousef
@alien0x_ -
 Kareem Alsadeq
Kareem Alsadeq
@AlsadeqKareem -
 Mohammed Hasan
Mohammed Hasan
@0xHasanM -
 Mohamed Sayed (ret2flex) 🇵🇸
Mohamed Sayed (ret2flex) 🇵🇸
@FlEx0Geek -
 Ahmad
Ahmad
@0xbahaa -
 Mostafa-Abdelaziz
Mostafa-Abdelaziz
@0xMM0X -
 Mohamed Elawadly
Mohamed Elawadly
@Elawadly77 -
 Mohamed Serwah 🇵🇸
Mohamed Serwah 🇵🇸
@serWazito0 -
 Yasser Ali
Yasser Ali
@n3r0li -
 Abd Elrhman Anter
Abd Elrhman Anter
@Anubi5x0 -
 🇵🇸 1nclud3 🇵🇸
🇵🇸 1nclud3 🇵🇸
@1nclud3 -
 MUHAMMAD
MUHAMMAD
@SN1PER47 -
 Ahmed Fatouh
Ahmed Fatouh
@XDev05 -
 Mohamed AbuMuslim (أبومُسْلِم)
Mohamed AbuMuslim (أبومُسْلِم)
@m19o__ -
 Abdalazez irsheidat
Abdalazez irsheidat
@irsheidat1
Something went wrong.
Something went wrong.























































































































