the_storm
@the_st0rmSecurity Engineer @Lacework, Ex @Meta, @Deloitte, @SecForce_LTD. CTFer with LCBC, vulnerability researcher and exploit dev. Opinions are my own
Similar User

@malcolmx0x

@0x4148

@Agarri_FR

@Zigoo0

@gwendallecoguic

@uraniumhacker

@Zombiehelp54

@SecurityMB

@dia2diab

@FlEx0Geek

@GeneralEG64

@ngalongc

@pwntester

@dPhoeniixx

@artsploit
I am thrilled to announce that I will be presenting @BlackHatEvents "Do You Speak My Language? Make Static Analysis Engines Understand Each Other" blackhat.com/us-21/briefing… Using static analysis to find security bugs cross-language and cross-repo #BHUSA
Anyone spending the brief liminal window between Christmas and Georgian new year in Hamburg, with the hackers, at CCC? I am! And I'll be presenting new research and a new talk ☺️ . What happens when we put love and intimacy at the center of our understanding of privacy, and…

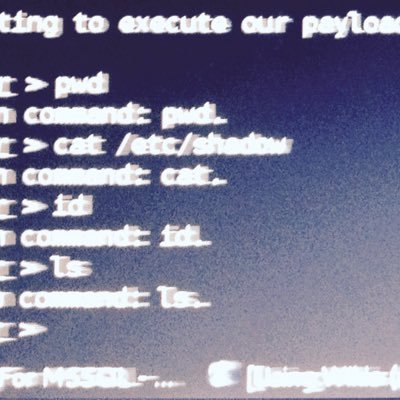
A no bull shit staright up fAcTuAl RCE, choke on this
hop skip jump over to our latest blog post - analysing Fortinet's FortiJump CVE-2024-47575, FortiJump-Higher (we love this name😄) and beyond (PoC included) labs.watchtowr.com/hop-skip-forti…
👋 a bit of late news, but I recently left Microsoft to build a startup. We closed our pre-seed and have a nice position. I'm looking for a solid SWE with experience in KVM/Xen/Hypervisors. If you are interested or know someone, please DM. JD here: stealthium.notion.site/Software-Engin…
CVE-2024-9143 (openssl-library.org/news/secadv/20…) was disclosed recently, which was found by OSS-Fuzz-Gen! This is a pretty proud example of our team showing the promise of leveraging LLMs enable more fuzzing coverage.
Exploiting two kernel vulnerabilities within the Mali GPU in Google Pixel 7 and 8 Pro models (Android 14) github.com/0x36/Pixel_GPU… Credits @_simo36 #Android #infosec


Impressive research and writeup! You have to include imgs.xkcd.com/comics/depende…

New writeup from @_specters_ and I: we're finally allowed to disclose a vulnerability reported to Kia which would've allowed an attacker to remotely control almost all vehicles made after 2013 using only the license plate. Full disclosure: samcurry.net/hacking-kia
there is a challenge in idekCTF 2024 called srcdoc-memos made by icesfont, it's about iframe, sandbox, CSP, navigation, session history and policy container. I spent like a week to understand how it works lol, really complex but also interesting. blog.huli.tw/2024/09/07/en/…
Such a delight to sit down with the great @a_greenberg for a long engaged convo on surveillance, AI, my wild path through tech, and how by rejecting the toxic norm Signal provides a shining model for better, healthier tech futures♥️ wired.com/story/meredith…
Signal is blocked in several countries but you can set up a proxy server to help people access Signal no matter where they live. Here’s how: signal.org/blog/proxy-ple… Thank you for helping keep Signal available for everyone who needs it. To share your proxies use #SignalProxy
Absolutely! 🚀 It's been an incredible journey working on code security at @Lacework Big shoutout to the amazing team!
I've been fortunate to work with some great people on code security @Lacework . Here's a description work we've been up to on the security of 1st-party code. (with @dildog , @the_st0rm , @Vatlidak , @pascalkesseli + FrancescoP, JeremyD, LinpengZ) lacework.com/blog/sast-for-…
1/ A world first reverse engineering analysis of AWS Session Tokens. Prior to our research these tokens were a complete black box. Today, we are making it more of a glass box, by sharing code and tools to analyze and modify AWS Session Tokens. medium.com/@TalBeerySec/r…
My @LocoMocoSec keynote slides on "Google's Recipe for Scaling (Web) Security" are online now: speakerdeck.com/lweichselbaum/…

Linux システムの起動プロセス、勉強になった。 1. 電源オン 2. BIOS/UEFI が起動し、POST (Power-On Self-Test) を実行 3. デバイスの検出 4. 起動デバイスの選択 5. ブートローダー (GRUB) の実行 - /etc/grub2.cfg の読み込み - カーネルの実行 - 必要なライブラリの読み込み 6. systemd…

This weekend, I played with Blue Water in GoogleCTF. Here are my challenge writeups. Give them a read, I had a lot of fun writing them! TL;DR: Rust reversing, inverting a crappy cipher, finite fields :D 👇 github.com/perfectblue/ct…
For what is worth, I gave a talk about "Python specialized bytecode" and a "pycjail returns" CTF challenge recently. A TL;DR of specialized bytecode as well as the talk video and slides (where I also talk about Python jails) can be found on disconnect3d.pl/2024/06/20/pyt…
United States Trends
- 1. soobin 97,3 B posts
- 2. Cowboys 72,1 B posts
- 3. KADOKAWA 37,1 B posts
- 4. Clippers 12,2 B posts
- 5. Eliza 13,4 B posts
- 6. Texans N/A
- 7. #EeveeDay N/A
- 8. Fultz 1.579 posts
- 9. Jerry 42,7 B posts
- 10. Norman Powell 2.035 posts
- 11. #پاکستان_میری_پہچان 1.020 posts
- 12. Lindy 3.780 posts
- 13. Eevee Evolution N/A
- 14. sabrina 114 B posts
- 15. Cooper Rush 12 B posts
- 16. #AskShadow 7.624 posts
- 17. Mixon 18,2 B posts
- 18. Herta 47,9 B posts
- 19. Dyson Daniels 2.913 posts
- 20. Trey Lance 3.269 posts
Who to follow
-
 mohammed eldeeb
mohammed eldeeb
@malcolmx0x -
 Ahmed Sultan 🇵🇸
Ahmed Sultan 🇵🇸
@0x4148 -
 Nicolas Grégoire
Nicolas Grégoire
@Agarri_FR -
 Ebrahem Hegazy 🇵🇸
Ebrahem Hegazy 🇵🇸
@Zigoo0 -
 Gwendal Le Coguic
Gwendal Le Coguic
@gwendallecoguic -
 Uranium238
Uranium238
@uraniumhacker -
 Mahmoud Gamal
Mahmoud Gamal
@Zombiehelp54 -
 @[email protected]
@[email protected]
@SecurityMB -
 dia2diab
dia2diab
@dia2diab -
 Mohamed Sayed (ret2flex) 🇵🇸
Mohamed Sayed (ret2flex) 🇵🇸
@FlEx0Geek -
 Youssef A. Mohamed
Youssef A. Mohamed
@GeneralEG64 -
 Ron Chan
Ron Chan
@ngalongc -
 Alvaro Muñoz
Alvaro Muñoz
@pwntester -
 Sayed Abdelhafiz
Sayed Abdelhafiz
@dPhoeniixx -
 Michael Stepankin
Michael Stepankin
@artsploit
Something went wrong.
Something went wrong.