Tornike
@tornikepa#Linux #Malware Researcher #Pent3ster published vulnerabilities #0day #Exploits advisories from various resources by #Cybersecurity #Bug #ReverseEngineering :wq
Similar User

@ddiwakr

@TeamSecureio

@ITJunkie

@egeblc

@magumison

@geekypanda411

@bohansec

@f00fc7c800

@x64koichi

@luigi_martire94

@VeryVillanous

@m8_brh

@charmarkeh_ys

@FoxtrotBugcrowd

@shivanirsharma
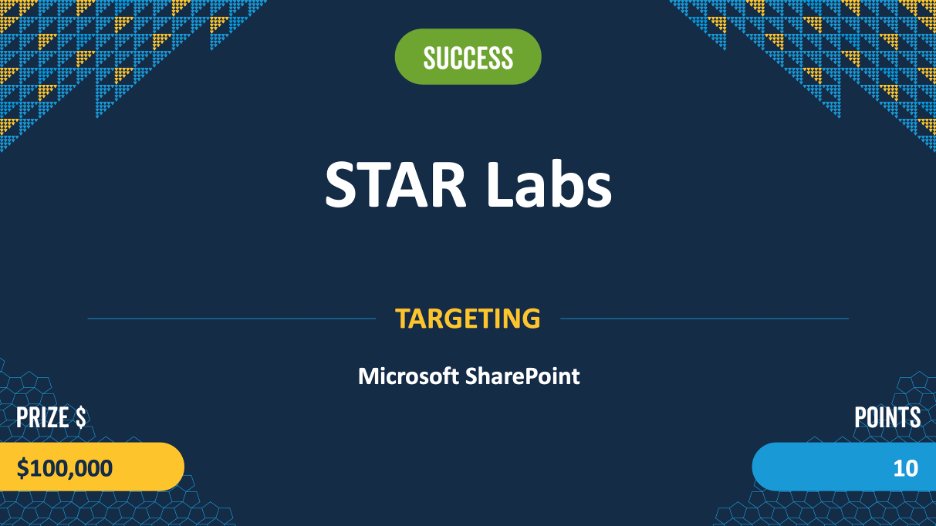
Success! @testanull of @starlabs_sg was able to execute a 2-bug chain on Microsoft SharePoint. They earn $100,000 and 10 Master of Pwn points. #Pwn2Own #P2OVancouver

Using Fav-Up github.com/pielco11/fav-up is a simple and effective tool for identifying the real IP address of a server behind #Cloudflare. By using the #favicon associated with a web application as a starting point #search for the server's real IP address using #Shodan. #OSINT

#Telegram data leak: 395 Million User allegedly put on sale online #DarkWeb Data expose the content messages it is worrying Telegram has yet to confirm the #dataleak, that the only evidence thus far consists of unsubstantiated screenshots posted to the dark web. #databreach



#Telegram leak votre username dans l'header TLS [Server_Name_Indication extension] Sympa non ? :)

The #msdt Organisations may be able to defend themselves from attack, while they wait for an official patch from Microsoft, by tweaking their computers’ Registry keys to unregister the ms-msdt protocol. #0day #follina #microsoftoffice #malicious #security #infosec #vulnerability



What is hidden in the number 68? Just a coincidence? #UkraineRussiaWar #Ukraine️ #war #History

Check if your #Linux servers have been compromised. Scan them to detect traces of post-exploitation activity or #malicious code. Sign up for free at protect.intezer.com #Log4Shell #vulnerable app #POC used github.com/christophetd/l…

run this in your Linux hosts to see where's your vuln code #Log4J #Log4Shell #vulnerability #intezer find / 2>/dev/null -regex ".*.jar" -type f | xargs -I{} grep JndiLookup.class "{}" Also open source tool to scan for #log4j usage in runtime github.com/intezer/log4js…
A security researcher has discovered a command injection #vulnerability that affects millions of Hikvision's #IoT devices, @MihirBagwe reports: #CVE-2021-36260 cyber.gov.au/acsc/view-all-…
Apple patches an XSS iCloud vulnerability after the bug was reported by a bug bounty hunter 9to5mac.com/2021/02/22/sec… #apple #icloud #xss #vulnerability #bug

Linux Hardening Guide madaidans-insecurities.github.io/guides/linux-h… #Pentesting #Linux #Kernel #CyberSecurity #Infosec



A Threat Actor is selling a Database of the Italian mobile service provider ho. (ho-mobile.it) owned by @VodafoneIT 🇮🇹. The dump allegedly includes 2,500,000 customers' PII Data, Phone Numbers & ICCID that can be exploited for SIM swap attacks to empty Bank accounts.

Data recovery engineers and digital forensics experts consider the #PC3000 #Flash as the #tool №1 #hardware #software #Data #Repair #Tool #SDCard #recovery #microchip #forensics
United States Trends
- 1. #SpotifyWrapped 267 B posts
- 2. Pete 523 B posts
- 3. #CUTOSHI 4.511 posts
- 4. Happy Birthday Dan 6.517 posts
- 5. $santa 5.468 posts
- 6. Brian Thompson 16,8 B posts
- 7. DeSantis 53 B posts
- 8. Apple Music 232 B posts
- 9. United Healthcare 8.026 posts
- 10. Conor McGregor 1.456 posts
- 11. #NSD25 16,8 B posts
- 12. #NationalCookieDay 2.253 posts
- 13. #OurOceanOfLoveSoobin 37,8 B posts
- 14. chappell 12,8 B posts
- 15. Midtown 11,7 B posts
- 16. ACLU 17,1 B posts
- 17. Hilton Hotel 10,9 B posts
- 18. National Signing Day 8.313 posts
- 19. Happy Founders N/A
- 20. SecDef 19,6 B posts
Who to follow
-
 Divyanshu Diwakar
Divyanshu Diwakar
@ddiwakr -
 Team Secure
Team Secure
@TeamSecureio -
 Neal Bridges
Neal Bridges
@ITJunkie -
 ege
ege
@egeblc -
 magumison
magumison
@magumison -
 GeekyPanda
GeekyPanda
@geekypanda411 -
 Bohan Zhang
Bohan Zhang
@bohansec -
 f00fc7c800
f00fc7c800
@f00fc7c800 -
 Koichi
Koichi
@x64koichi -
 Luigi Martire
Luigi Martire
@luigi_martire94 -
 Cyber Villain 🛡️
Cyber Villain 🛡️
@VeryVillanous -
 MrM8BRH 🇵🇸
MrM8BRH 🇵🇸
@m8_brh -
 Charmarkeh Y.
Charmarkeh Y.
@charmarkeh_ys -
 foxtrot.sol
foxtrot.sol
@FoxtrotBugcrowd -
 Shivani Sharma
Shivani Sharma
@shivanirsharma
Something went wrong.
Something went wrong.




















































































































