Similar User

@pulsoid

@raelizecom

@doegox

@hardwear_io

@mr_phrazer

@Riscure

@aseemjakhar

@newaetech

@antriksh_s

@jzvw

@h3artcontainer

@therealsaumil

@max_r_b

@nedos

@_m46s
We are looking forward to give our #BootPwn experience at #HITB2023AMS in Amsterdam. There are still tickets available and April is often a very nice time to visit Amsterdam! But you know what they say: 'april doet wat hij wil'... (i.e., bring a rain coat).
Our first upcoming #BootPwn training will be on April 17-20 at #HITB2023AMS in Amsterdam, The Netherlands. More info: sectrain.hitb.org/courses/bootpw…
Join @tieknimmers for his advanced course, The Art of Fault Injection: Advanced Techniques and attacks. Come to BOOTSTRAP25 in Austin, TX, March 2025 and get complimentary access to our BOOTSTRAP25 event! ringzer0.training/bootstrap25-th…
At #hw_ioNL2024 we're in the process of creating the Van Goghs of the Hardware industry—The Art of Fault Injection (TAoFI) 🎨🖌️🔧 Along with brilliant minds @tieknimmers & @pulsoid Know More: hardwear.io/netherlands-20… #faultinjection #attacks #techniques

Having some fun with an old CVE to explore ARM TrustZone more. Having no proper debuggability can really be a nightmare, especially when the MMU/caching is involved. Cool research by @raelizecom
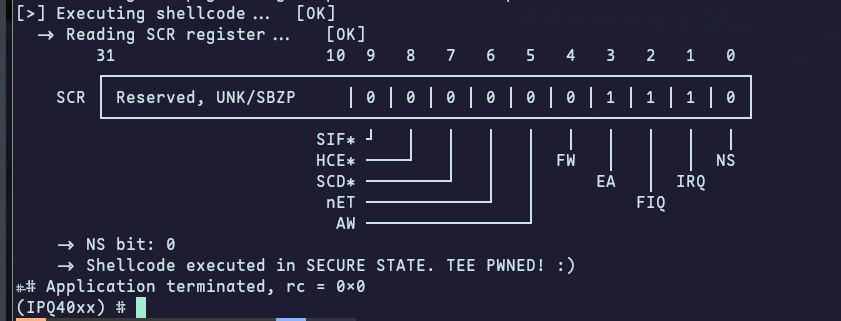
Looking forward to presenting my research tomorrow @hexacon_fr !
"HSM Security and Exploitation of USB over SPI bug" 💸 by Sergei Volokitin

Our first keynote for #H2HC2024 (21 years): Cristofaro Mune @pulsoid @h2hconference

If you are looking for the #ChipWhisperer Husky, there is currently stock on @crowd_supply The Husky will be back in stock on @MouserElec shortly. crowdsupply.com/newae/chipwhis…
Pi Pico2 EMFI update: Not enough time; no chance of the $10k bounty, but fun testing glitch detection (spoiler: it’s good). Pics: 1. Glitch detection disabled 2. Detection enabled Red=Successful loop corruption Green=No effect Blue=Reboot Yellow=Caught by detector (1mm coil@200V)


This paper was the perfect length for my flight home. Such an awesome attack. A little lost in the linear equation section but excited to try replicating it and seeing if it’s possible with voltage instead of EMFI or with much lower cost EMFI tooling
The air in Philadelphia is feeling very charged right now, as Jeroen Delvaux talks about using electromagnetic glitches that they used for “Breaking Espressif’s ESP32 V3: Program Counter Control with Computed Values using Fault Injection” #woot24


The air in Philadelphia is feeling very charged right now, as Jeroen Delvaux talks about using electromagnetic glitches that they used for “Breaking Espressif’s ESP32 V3: Program Counter Control with Computed Values using Fault Injection” #woot24


[#POC2024 Training] 👤 @pulsoid & @tieknimmers - The Art of Fault Injection: Advanced Techniques & Attacks 📅 Date: 4th ~ 6th Nov (3days) 🇰🇷 Venue: Four Seasons Hotel, Seoul, South Korea ‼️Registration ends on the "20th Sept"

Shot Through the Heart: An Introduction to Fault Injection (@crowd_supply #Teardown2024) slides are up! grandideastudio.com/portfolio/secu…
What a weekend! Thanks to everyone who joined us at #Teardown2024. Keep the conversation going and catch up with the folks you met this weekend by joining our Discord community: discord.gg/RRsHCW9H6X
Are you a cool hacker? 🤔 Of course you are! ✨ It's time to stop hiding in plain sight and present your most recent findings at Hardwear.io Netherlands 2024. 🔺 The Call For Papers is open! Submit before 10th August 2024 👉 hardwear.io/netherlands-20… #cfp #hw_ioNL2024

Exciting news! 🤩 18 papers were accepted and will be part of an amazing WOOT program on August 12-13 in Philadelphia! usenix.org/conference/woo… Stay tuned for more details on the program!
W00t! We're happy to share that our paper "Breaking Espressif's ESP32 V3: Program Counter Control with Computed Values using Fault Injection" will be presented at WOOT '24 (@wootsecurity). usenix.org/conference/woo…
Want to learn how to break Trusted Execution Environments (TEEs)? @pulsoid will teach TEEPwn: Breaking TEE by experience this July: ringzer0.training/doubledown24-t…
[#POC2024 NOTICE] ⏰Date: 7-8th November, 2024 🇰🇷Venue: Four Seasons Hotel, Seoul, South Korea 🎟️Registration: 2nd Sept ~ [CFP & CFT is opened] CFP - until 5th Oct CFT - until 31st July For more: powerofcommunity.net

CVE-2024-4760: cve.org/cverecord?id=C… We used Chipwhisperer for voltage injection from @newaetech Also a current probe for power analysis from @Riscure Stay tuned for part 2&3
Everyone has their faults, but now you can learn how to inject faults into ESP32s with @pulsoid's The Art of Fault Injection course in Las Vegas, August 3 - 6: buff.ly/3QlZJYi
Changes on EVERY page, new chapter "Cryptocurrency cryptography" inc. PoW, algebraic hashing & Poseidon, multi-signatures, threshold signatures, zero-knowledge proofs, and more. NEW: section about Ed25519; the new Linux PRNG; NIST's PQC standards nostarch.com/serious-crypto…

True benchmark for a FI tool is not a loop but PC/LR control through memcpy or any memory operation. Managed to corrupt the load instruction from register to PC and execute any code.

United States Trends
- 1. Tyson 528 B posts
- 2. Karoline 21 B posts
- 3. #wompwomp 6.925 posts
- 4. Syracuse 22,2 B posts
- 5. Paige 7.802 posts
- 6. Kiyan 26,6 B posts
- 7. Pence 61,7 B posts
- 8. Kash 107 B posts
- 9. The FBI 274 B posts
- 10. Debbie 35,8 B posts
- 11. Jarry N/A
- 12. Whoopi 117 B posts
- 13. #LetsBONK 16,6 B posts
- 14. Dora 24,7 B posts
- 15. #TOKKIVSWORLD 1.775 posts
- 16. Villanova 1.848 posts
- 17. White House Press Secretary 21,2 B posts
- 18. Ace Bailey N/A
- 19. Kyle Neptune N/A
- 20. Bucks County 98,2 B posts
Who to follow
-
 Cristofaro Mune
Cristofaro Mune
@pulsoid -
 Raelize
Raelize
@raelizecom -
 Philippe Teuwen
Philippe Teuwen
@doegox -
 hardwear.io
hardwear.io
@hardwear_io -
 Tim Blazytko
Tim Blazytko
@mr_phrazer -
 Keysight Device Security Testing
Keysight Device Security Testing
@Riscure -
 Aseem Jakhar
Aseem Jakhar
@aseemjakhar -
 NewAE Technology Inc
NewAE Technology Inc
@newaetech -
 Antriksh (Yoda) #NullconGoa2025
Antriksh (Yoda) #NullconGoa2025
@antriksh_s -
 Jasper van Woudenberg
Jasper van Woudenberg
@jzvw -
 Dennis Elser
Dennis Elser
@h3artcontainer -
 🐘 @[email protected]
🐘 @[email protected]
@therealsaumil -
 Maxime Rossi Bellom
Maxime Rossi Bellom
@max_r_b -
 Dmitry Nedospasov
Dmitry Nedospasov
@nedos -
 Maggie
Maggie
@_m46s
Something went wrong.
Something went wrong.
















































































![Account for the day[0] podcast + media.](https://pbs.twimg.com/profile_images/1221600753904537601/8sV0PIy_.png)