ThorMM
@synbytePenetration Tester / Cybersecurity Analyst
Similar User

@NisH0cK

@S41NTsec

@udonandon

@Lozr4_

@ttc2mi

@Mrbekostips

@skn__07

@D__303

@Rando2217

@0xh4ty

@Suresh_3_6
🎤✨ Our security researcher, Konstantin Polishin, presented “Red Team Social Engineering 2024: Initial Access TTP and Project Experience of Our Team” at #ROOTCON18 🚀 Recording: youtube.com/watch?v=6nnZJi…
Mutation XSS: Explained, CVE and Challenge, good mXSS article by @J0R1AN jorianwoltjer.com/blog/p/hacking…
I talk about this on the pod all the time, but CSRF is dead simple. You just need to know the conditions. I'm not gonna recite them again here, but today a new condition came up: No Content-Type header -> no CSRF restrictions Same-site: None POST = CSRF The research:
To summarize what I have learned about Mutation XSS, my CVE, and the solution to my challenge, I wrote a post going through it all. If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this! jorianwoltjer.com/blog/p/hacking…
I have put together a list of publicly known IOC for impacket. Thanks to @Octoberfest73 and others on the awesome research. n7wera.notion.site/Modifing-Impac…
Here's how you can quickly escalate your SQL injections to RCE on different databases! 🤑 A small thread! 🧵 👇
Just launched! Improve your GraphQL skills with my free Upskill Challenge! Takes around 30 minutes and will introduce you to writing queries and mutations, introspection and the differences between GraphQL and RESTful APIs justhacking.com/uc/uc-graphql/
🚀 AD Miner v1.7.0 release! This major update brings greatly improved cypher queries speed (thanks to GDS), brand-new ESC15 edge, a significant code refactoring, post-processing perfs boost, and more. For short, better and faster!🌟 github.com/Mazars-Tech/AD…

How to find bugs in Microsoft iis page. infosecwriteups.com/how-to-find-bu… #bugbounty #bugbountytips #bugbountytip
🚨 100 Red Team Projects for Pentesters and Network Managers Here Link: github.com/kurogai/100-re…

PSA to Red Teams: forking/cloning lsass.exe to get creds from the child is a gift to the blue team as it leaves a lsass child process + makes a trivial event log based detection. The following URL is timestamped to where I discussed this at @BSidesPhilly youtube.com/watch?v=Ow7Az1…
During my research for the video, I compiled the MXSS Evolution and Timeline, which is now public as blog. Awesome MXSS: github.com/msrkp/MXSS youtube.com/watch?v=aczTce…
MXSS Explained Part 1: Why Server-Side HTML Sanitizers Are Doomed to Fail with this XSS! In this video, I dive into how sanitizers work, discuss the first known MXSS in IE, and showcase an MXSS vulnerability in the popular Node.js module, sanitize-html. youtu.be/aczTceXp49U

Ever wanted to quickly test for HTTP request smuggling vulnerabilities? 🧐 Smuggler by @defparam is an automated tool to help you find HTTP request smuggling and HTTP desync attacks! 😎 Smuggler is open-source and available on Github! 👇 buff.ly/37N4ouK

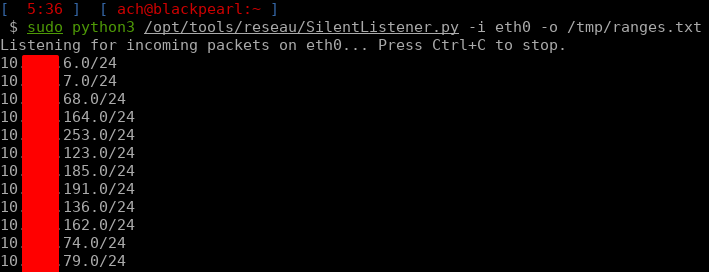
For that need, I wrote a quick Python script that will bind to an interface and build subnets file based on incoming packets: gist.github.com/Dfte/9cfeb8789… was very useful lately 👀
IOS Pentesting Series Learn how to work with useful tools and apps such as Frida, Objection, 3uTools, Cydia, Burp, fsmon, fridump, SSL bypass, reFlutter etc. Part 1: 🔗kishorbalan.medium.com/start-your-fir… Part 2: 🔗kishorbalan.medium.com/ios-pentesting… Part 3: 🔗kishorbalan.medium.com/ios-pentesting…
From a security standpoint, what would you do if you wanted to setup a new Active Directory installation today *and* wanted it to be at least decently secure? In answer, many fashionable IT/tech people would just give you just a laugh. But really, what would it take? A quick🧵:
Top JWT Attacks 😀 Thread 🧵:👇 Here is how to find JWT issues: 1) JWT or JSON web tokens are widely used these days for authorization purposes so it pays off to learn about what JWT’s entail and how we can abuse them. #BugBounty #bugbountytips #infosec
bro just discovered a hackbar variant that has some really old dios queries. And just casually injecting random dios queries and called it "... bypass many WAF's" Great content nevertheless for people who mostly use SQLMap for sql injection.
check out new video the extension i used for this video can Bypass many WAF's youtu.be/KgLKI2oPDtw?si…
United States Trends
- 1. Bama 29 B posts
- 2. Miami 100 B posts
- 3. Clemson 15,1 B posts
- 4. South Carolina 23,6 B posts
- 5. XDefiant 8.915 posts
- 6. Cam Payne N/A
- 7. Warde Manuel 1.927 posts
- 8. Ubisoft 7.795 posts
- 9. #CFBPlayoff 4.429 posts
- 10. Africa 265 B posts
- 11. Gundam 103 B posts
- 12. Eric Dixon N/A
- 13. #MAFS N/A
- 14. Villanova 1.545 posts
- 15. Lindsey 26,9 B posts
- 16. Committee 181 B posts
- 17. Hegseth 132 B posts
- 18. The CFP 12,7 B posts
- 19. #MarriedAtFirstSight N/A
- 20. #NewYorkForever N/A
Something went wrong.
Something went wrong.