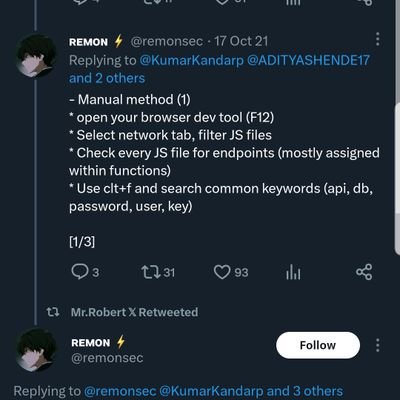
Shivang Maurya
@shivangmauryaaBug Bounty Hunter at hackerone and BugCrowd .
Got self XSS binded it with CSRF but program do not accept reflected and DOM.. Any idea to increase severity? Or would u like to collaborate? #bugbounty #cybersec #hackerone #bugcrowd #hacking #yeswehack #bounty #bugbountytips
Hello @yeswehack can you check my report #YWH-PGM5447-272 Which is closed as RFTS. Well this is actually an issue where I'm able to make an open redirect. Example..Com//@evil..Com Where the request is getting generated from example..com but they are are saying it's usernam
Bug accepted intigriti on public program. Bug : open redirect POC : example.com//shivang.com/%….. #bugbounty #bug #bounty #hackerone #intigriti #hacker #cybersecurity #shivangmauryaa

Blind- SQLI duplicates here I have reported 4 SQLI on 3 Different Subdomain. but all got duplicated by one Report #277862* I have asked triager many times since 15 days no reply from them. @Hacker0x01 @HackerOneStatus @coffinxp7

Got self XSS in json via CVE-2021-20323 As self XSS don't have any impact is there any idea I can chain it with *CSRF*. However content-type: is required application/json . If it's not provided it gives error. I got this bug on almost 15 domains If you can bypass lemme know
I have reported one bug regarding open redirect on @yeswehack program . Eg : example .com//@evil.com But they are giving me an example of google.com@evil.com But the request is getting forward from their website . I'm still waiting for their response .
Got CRLF injection in one program on YesWeHack. But unable to show impact tried 1.XSS but content type not changing one more header getting created 2. By location and Host not redirecting Getting 400 error Any ideas??
N/A CRLF on Friday I was able to reproduce bug however I'm not able to reproduce same bug on Monday and got N/A by team @Bugcrowd @coffinxp7 What u think guys on this ?


recently I discovered a vulnerability with that I'm able to login into random accounts . 1. search on web archive 2. find %40 .... %40= @ 3. got lots of mail with token 4. simply copy paste the URL. Any some tips for me. @coffinxp7 @GodfatherOrwa @fattselimi @Bugcrowd


AWS Credentials leaking Is informational 🤔 I was able to read write and delete . #bugbounty #security #cybersecurity #bugbountytips #ScamAlert

United States Trends
- 1. ICBM 109 B posts
- 2. Good Thursday 22,8 B posts
- 3. Dnipro 39,1 B posts
- 4. The ICC 17,4 B posts
- 5. Bezos 22,2 B posts
- 6. #ThursdayMotivation 4.272 posts
- 7. #thursdayvibes 2.898 posts
- 8. Happy Friday Eve N/A
- 9. #KashOnly 8.143 posts
- 10. #21Nov 2.201 posts
- 11. #ThursdayThoughts 2.880 posts
- 12. $DUB 7.342 posts
- 13. Nikki Haley 28 B posts
- 14. MIRV 4.462 posts
- 15. Bitcoin 638 B posts
- 16. Adani 690 B posts
- 17. Happy Birthday Nerissa 7.399 posts
- 18. Juice WRLD 24,1 B posts
- 19. Ellen DeGeneres 69 B posts
- 20. Aunt Jemima N/A
Something went wrong.
Something went wrong.