
Pavel
@pppturtleHead of Vulnerability Research @ https://t.co/B0f2yNQvoA CTF player @ SPRUSH
To pwners and reversers: Have you tried my GEF fork? Features: - Kernel commands (without "vmlinux with symbols"; for qemu-system) - More architectures support (for qemu-user) - Minor heap allocator dumper And many more! Bugs? Please report them:) Enjoy! github.com/bata24/gef
Vulnerability Research team at BI.ZONE has proved the exploitability of CVE-2024-38812 and CVE-2024-38813 which are critical vulnerabilities in VMware vCenter.
Hi, here is my memory corruption PoC for CVE-2024-7965 github.com/bi-zone/CVE-20… . Topic with writeup bi.zone/expertise/blog… . (English version will be soon).
I successfully triggered vulnerability and got memory corruption. Wait some days for paper =)
From Theory to Practice: Kernel Heap Spray Exploitation for Privilege Escalation💥 Part two of the blog series by my colleague Alex: northwave-cybersecurity.com/exploiting-ent…
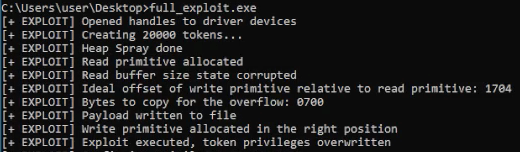
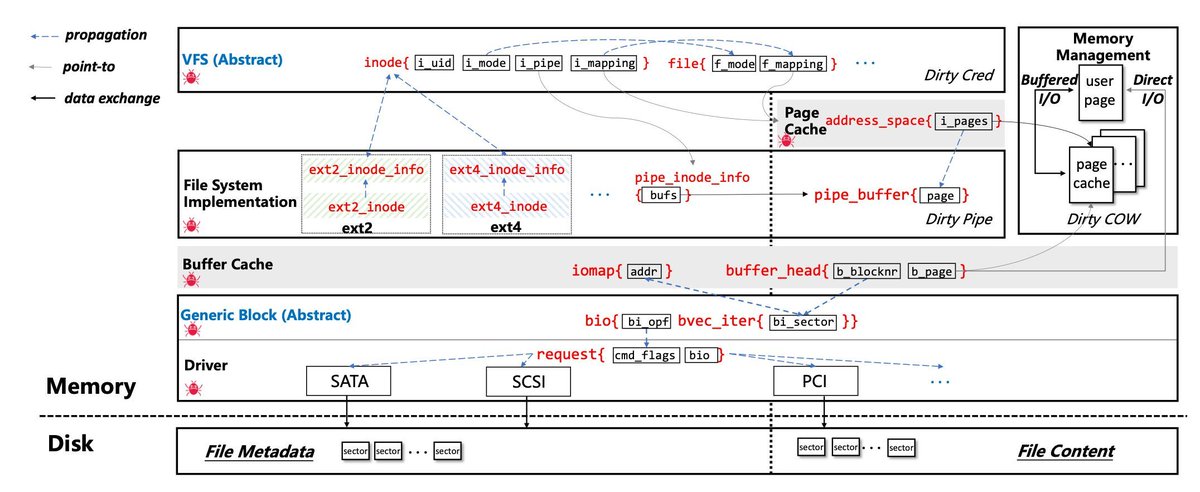
Analyze the exploitability of non-control objects (data only) objects in Linux kernel arxiv.org/pdf/2401.17618 #Linux #cybersecurity

United States Trends
- 1. Chiefs 138 B posts
- 2. Bengals 26,8 B posts
- 3. Josh Allen 3.653 posts
- 4. Herbert 16,2 B posts
- 5. Chargers 25,6 B posts
- 6. #BaddiesMidwest 8.239 posts
- 7. 49ers 41,9 B posts
- 8. WWIII 119 B posts
- 9. #RHOP 4.631 posts
- 10. Super Bowl 5.543 posts
- 11. Mahomes 38,2 B posts
- 12. Niners 8.288 posts
- 13. Geno 35 B posts
- 14. Bo Nix 17,4 B posts
- 15. #BoltUp 2.233 posts
- 16. Jim Harbaugh 1.842 posts
- 17. #KCvsBUF 22,4 B posts
- 18. #CINvsLAC 3.297 posts
- 19. Falcons 21 B posts
- 20. Seahawks 29,5 B posts
Something went wrong.
Something went wrong.













































































