n3v1l
@n3v1l1Sólo un geek, amante de la tecnología, IoT, robótica, blockchain y por supuesto ciberseguridad
Similar User

@BSidesCL

@N4Security

@8dot8

@dplastico

@WhiloLab

@jheeere

@Hackttori

@vay3t

@d0berm1n

@Lockdown0x0

@Gohanckz

@ivanPorMor

@OpenSec
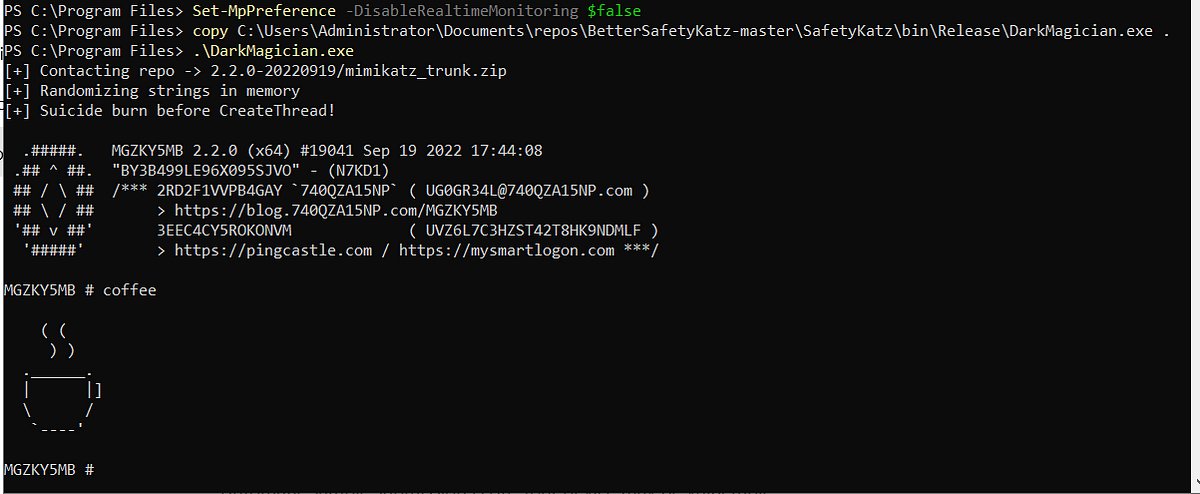
''Obfuscating a Mimikatz Downloader to Evade Defender (2024)'' #infosec #pentest #redteam #blueteam medium.com/@luisgerardomo…
Open source LLM tool primed to sniff out Python zero-days go.theregister.com/feed/www.there…
This is a tool for searching Exploits from some Exploit Databases. Exploits are inserted at sqlite database(go-exploitdb) can be searched by command line interface. In server mode, a simple Web API can be used. github.com/vulsio/go-expl…
BAADTokenBroker: Bypassing Entra ID Conditional Access meterpreter.org/baadtokenbroke…
Researchers Detail Ruby-SAML/GitLab Flaw (CVE-2024-45409) Allows SAML Authentication Bypass securityonline.info/researchers-de…
''GitHub - dafthack/MFASweep: A tool for checking if MFA is enabled on multiple Microsoft Services'' #infosec #pentest #redteam #blueteam github.com/dafthack/MFASw…
Hacking Contents - Reverse Engineering, Exploitation 📍 By: @0xor0ne Source: github.com/0xor0ne/awesom…
Windows doesn't verify the file extension if the file is executable, allowing malicious actors to spoof files and evade detection (PE files) A POC script for generating the payload more efficiently has been uploaded to: github.com/AnonKryptiQuz/…
SHELLSILO: Simplifying Syscall Assembly and Shellcode Creation meterpreter.org/shellsilo-simp…
The orginal RDPthief: github.com/0x09AL/RdpThief Now as a Powershell script made by The-Viper-One (not on X afaik): github.com/The-Viper-One/… Script loops checking for mstsc.exe. When it’s found it will inject RDPthief to capture cleartext credentials.

''Red Teaming in the age of EDR: Evasion of Endpoint Detection Through Malware Virtualisation'' #infosec #pentest #redteam #blueteam blog.fox-it.com/2024/09/25/red…
A Python-based toolkit for Information Gathering and Reconnaissance Source: github.com/jasonxtn/Argus
It’s this cmd check if a folder is excluded: & "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\folder_to_check\|*" Tool can be found here github.com/Friends-Securi…
Just found a new, smarter way to reveal Defender exclusion paths using MpCmdRun.exe-way better than the old Event Log 5700 method. Always cool to level up the game! 🔥 You can check it out on our new blog, Friends & Security: blog.fndsec.net #CyberSecurity…

knowsmore: A swiss army knife tool for pentesting Microsoft Active Directory meterpreter.org/knowsmore-a-sw…
OpenSecurityTraining2 is a god tier FREE resource for reverse engineering, malware analysis, exploit dev, OS internals, and more. Full learning paths from x86-64 to Windows kernel internals. There are no words for how good OST2 is. 👇Link in comments.

Deploy stealthy reverse shells using advanced process hollowing with GhostStrike – a C++ tool for ethical hacking and Red Team operations. github.com/stivenhacker/G…
CVE-2024-38200 - Microsoft Office NTLMv2 Disclosure Vulnerability github.com/passtheticket/…
Spider entire networks for juicy files sitting on SMB shares. Search filenames or file content - regex supported! github.com/blacklanternse…
always examine the .js files in the source code, for this I can recommend this simple but effective tool github.com/w9w/JSA from here you can access the endpoints of critical data, the places where backup files are stored and many endpoints 🌹🥰🥳 #bugbountytip #bugbounty…

🚀Just Released Bypass-Four03! 🎯 🛠️ It's a bash script to help bypass HTTP 403 errors using path & header fuzzing, HTTP method & protocol version testing, and more. Check it out on GitHub: [github.com/nazmul-ethi/By…] #bugbountytips #403Bypass

United States Trends
- 1. Tyson 542 B posts
- 2. Karoline Leavitt 21,2 B posts
- 3. Paige 8.194 posts
- 4. #wompwomp 7.179 posts
- 5. Syracuse 23,2 B posts
- 6. Pence 63,2 B posts
- 7. Kash 110 B posts
- 8. Kiyan 28 B posts
- 9. The FBI 266 B posts
- 10. Frankie Collins N/A
- 11. Debbie 36,5 B posts
- 12. Jarry N/A
- 13. Whoopi 120 B posts
- 14. #TOKKIVSWORLD 1.971 posts
- 15. #LetsBONK 16,9 B posts
- 16. White House Press Secretary 24,3 B posts
- 17. Dora 25,1 B posts
- 18. Juanfer 7.136 posts
- 19. Quintero 14,4 B posts
- 20. Ace Bailey N/A
Who to follow
-
 Bsides Chile
Bsides Chile
@BSidesCL -
 NIVEL4
NIVEL4
@N4Security -
 8.8 RELOADED - 31/10 - CDMX - México
8.8 RELOADED - 31/10 - CDMX - México
@8dot8 -
 dplastico (pwn)
dplastico (pwn)
@dplastico -
 Fundación Educacional WhiloLab
Fundación Educacional WhiloLab
@WhiloLab -
 xJhere
xJhere
@jheeere -
 h4tt0r1
h4tt0r1
@Hackttori -
 Vay3t
Vay3t
@vay3t -
 Sebastian Döll
Sebastian Döll
@d0berm1n -
 Lockdown Fest
Lockdown Fest
@Lockdown0x0 -
 Iván González
Iván González
@Gohanckz -
 Ivan Portillo
Ivan Portillo
@ivanPorMor -
 Open-Sec
Open-Sec
@OpenSec
Something went wrong.
Something went wrong.