Similar User

@borrello_pietro

@0xhilbert

@PurnalToon

@redrabbyte

@notbobbytables

@BloodyTangerine

@herbertbos

@cat_easdon

@paetscan

@barbaragigerl

@____salmon____

@MariaEichlseder

@notimaginary_

@weber_daniel

@LosFuzzys
My #PhD thesis: "Remote Side-Channel Attacks and Defenses" is available here: martinschwarzl.at/media/files/th… Thanks to all my colleagues and friends, especially, @lavados, @misc0110 and @mlqxyz for your support!
Today over half the QUIC connections transfer fewer than 8kB. Of those about 40% is for the certificates. That'll be a whole lot more with drop-in PQ certificates. Read our new blog for more stats and an overview of PQ signature schemes on the horizon. blog.cloudflare.com/another-look-a…
Guess what? #IBPB (the speculation barrier) was broken in microcode for return instructions on the latest Intel CPUs. Linux also used it wrongly for AMD CPUs, so we could revive #Inception!
HW defenses against Spectre are tricky: they need to be applied correctly by the SW, and we need to trust that the HW does what its supposed to. Our latest work "Breaking the Barrier" exploits loopholes in both of these issues on Intel and AMD parts. comsec.ethz.ch/breaking-the-b…
Excited to announce the release of the Rapid Data Analysis (RDA) framework! RDA streamlines side-channel analysis with plotting, processing, and analysis tools—usable directly from the terminal or in scripts. Check it out: github.com/0xhilbert/rda #SideChannel

Confused deputy attacks on EDA software generate vulnerable hardware from secure RTL. TransFuzz discovers 20 such translation bugs in open-source EDA (25 CVEs). Will be presented at USENIX Security '25. comsec.ethz.ch/wp-content/fil… @kavehrazavi @K_CeesaySeitz
The whitepaper is live! Listen to the whispers: web timing attacks that actually work. Read it here -> portswigger.net/research/liste…
New paper on automating data only attacks. If you can overwrite certain data but can't execute arbitrary code (which has been getting much harder) this might be the attack for you. usenix.org/publications/l…

Congratulations to @marv0x90 for winning Austria's most prestigious PhD award, the Heinz Zemanek Award! This is so well deserved. Martin is incredibly brilliant, talented, and hard-working but also one of the kindest people I know. Really happy that he receives this recognition!
This year‘s Heinz Zemanek Award (Austria‘s most prestigious PhD Award by @OCG_aktuell ) goes to… … @BurgholzerLukas! 🎉 Lukas’ work is essential for the development of #software for #QuantumComputing! Huge congratulations! 🙂 More (in German) at ocg.at/blog/heinz-zem…

Finally got around to publishing the slides of my talk @offensive_con from ~two weeks ago. Sorry for the delay! The V8 Heap Sandbox: saelo.github.io/presentations/… Fantastic conference, as usual! :)
For the first time, we imaged and reverse engineered 6 modern DDR4/5 DRAM chips (comsec.ethz.ch/hifi-dram) Due to the incredibly small feature size of modern ICs, we use SEM combined with FIB reaching pixel resolutions as low as 3.4nm. Then we evaluate 10 years of DRAM research.
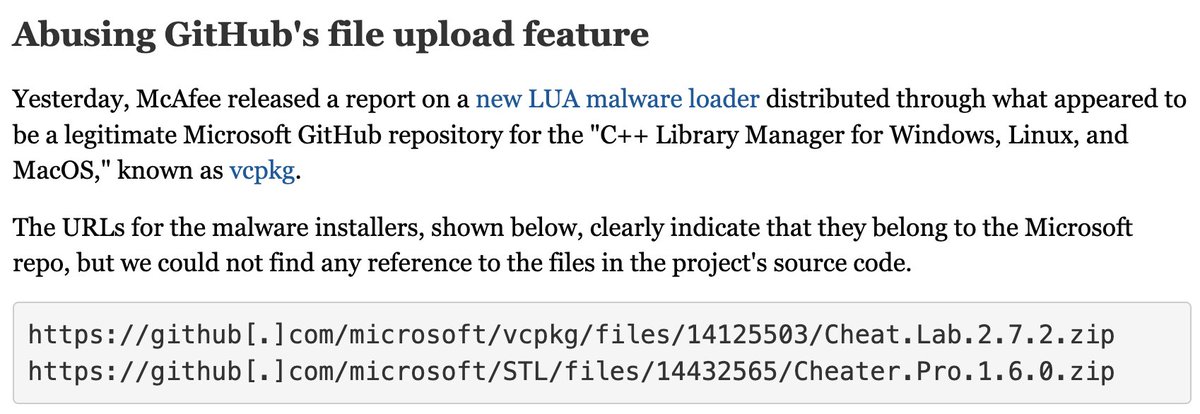
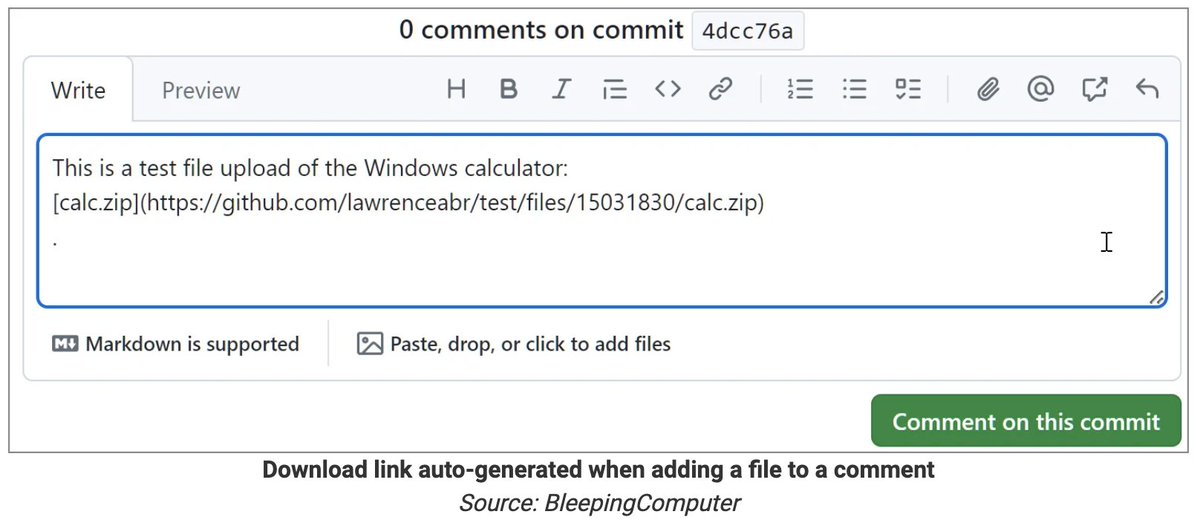
A GitHub flaw lets attackers upload executables that appear to be hosted on a company's official repo, such as Microsoft's—without the repo owner knowing anything about it. The following URLs, for example, make it seem like these ZIPs are present on Microsoft's source code repo:…
Tidied up the old NetSpectre repository and pushed the proof-of-concepts to Github: github.com/mschwarzl/nets…
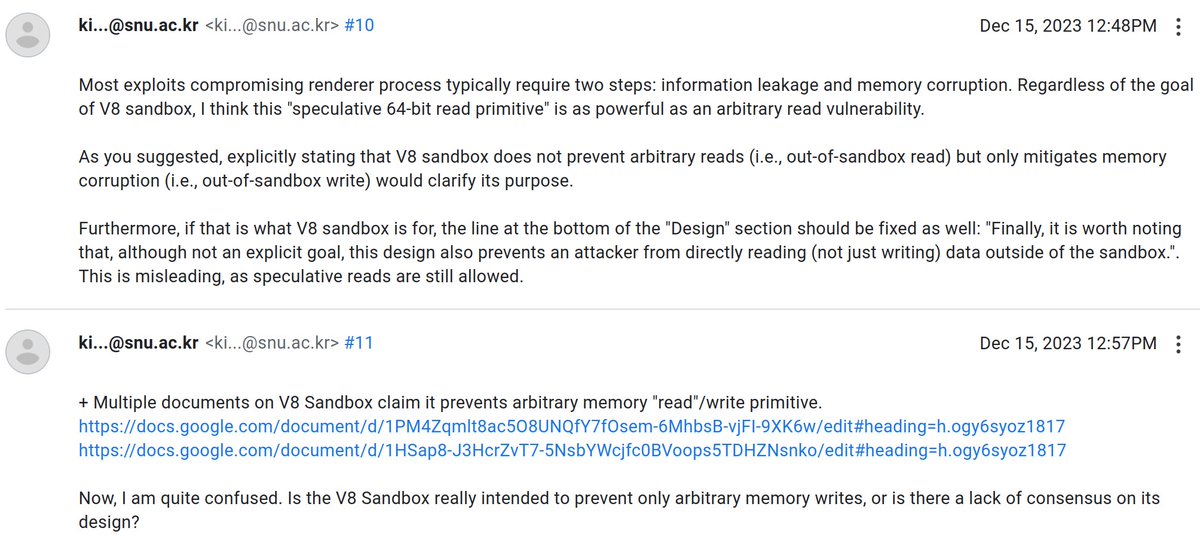
[1511448]V8 Spectre-v1 Vulnerability in V8-optimized code that allows speculative memory access to arbitrary 64-bit memory addresses, which bypasses the V8 Sandbox. issuetracker.google.com/issues/41484034 @5aelo Juhee Kim Youngjoo Lee


Big day for the V8 Sandbox: * Now included in the Chrome VRP: g.co/chrome/vrp/#v8… * Motivation & goals discussed in a new technical blog post: v8.dev/blog/sandbox If there is ever a Sandbox "beta" release, this is it!
My Ph.D. thesis is now online theses.fr/2023SORUS546.p…
Today some people told me that I got a Ph.D. degree, finally many important doctors like Dr. Dre, Dr. Doom, Dr. Who, Dr. House and Dr. Jekyll are my peers.
Remote Red Unlock with the access to the microarchitecture? Yes, it's now possible for new Intel Xeons: meet Intel BMCJTAG...

This information is invaluable for PCODE (firmware that runs on PUNIT) reverse engineering. It seems one more disassembler is coming...


The deadline for the @wootsecurity Practitioner Track has been extended by 2 weeks!
⚠️ We heard you! The deadline for the WOOT practitioner track has been extended by 2 weeks. New submission deadline is Mar 5th (AoE), so get your offensive research in soon! No changes to the academic track (deadline: Mar 12th). Your submission goes here: woot24.usenix.hotcrp.com

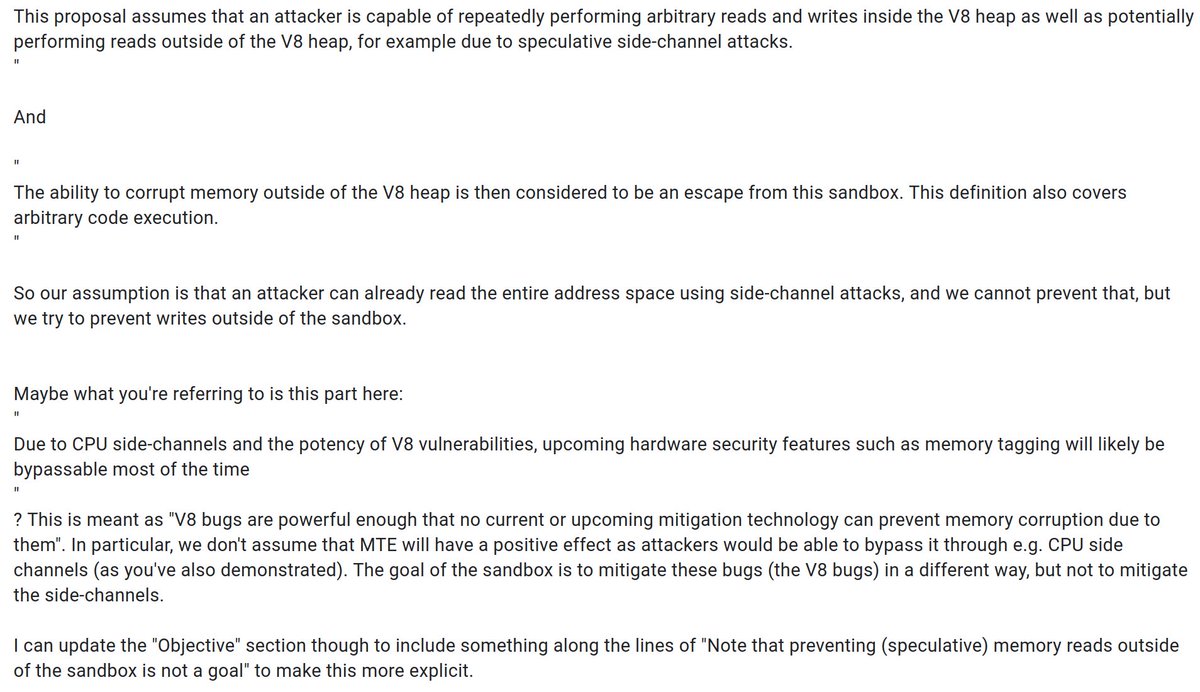
New V8 Sandbox design document is out: docs.google.com/document/d/12M… This discusses how a hardware-based sandbox instead of the currently purely software-based one might look like in a somewhat distant future (if at all)
Do you work on cool attack or other offensive research (Black Hat/DEF CON type of work)? 🥷 Consider submitting your research to the WOOT practitioner track to get valuable feedback from an amazing PC 😍 and reach a wider audience 🎤! usenix.org/conference/woo…
Congrats to Dr. Michael Schwarz on earning tenure! We're excited to have his expertise shaping our future. Check out a brief interview on our website to learn more about what this milestone means for @misc0110 cispa.de/en/schwarz-ten…

United States Trends
- 1. Auburn 34,3 B posts
- 2. Bama 35,7 B posts
- 3. Lakers 38,1 B posts
- 4. #LasVegasGP 142 B posts
- 5. Max Verstappen 53,8 B posts
- 6. UCLA 10,2 B posts
- 7. Lewis 78,2 B posts
- 8. Oklahoma 50,1 B posts
- 9. Nuggets 30 B posts
- 10. #AEWFullGear 82,1 B posts
- 11. LAFC 3.262 posts
- 12. Chuck Woolery 3.769 posts
- 13. Jokic 20 B posts
- 14. Milroe 16,9 B posts
- 15. Texas 148 B posts
- 16. Sainz 26,5 B posts
- 17. Lincoln Riley 1.085 posts
- 18. Sounders 1.379 posts
- 19. Lando 20,3 B posts
- 20. War Eagle 2.403 posts
Who to follow
-
 Pietro Borrello
Pietro Borrello
@borrello_pietro -
 Andreas Kogler
Andreas Kogler
@0xhilbert -
 Antoon Purnal
Antoon Purnal
@PurnalToon -
 Lukas Giner
Lukas Giner
@redrabbyte -
 Stefan Gast
Stefan Gast
@notbobbytables -
 Clémentine Maurice
Clémentine Maurice
@BloodyTangerine -
 Herbert Bos
Herbert Bos
@herbertbos -
 Cat Easdon
Cat Easdon
@cat_easdon -
 Anna Pätschke
Anna Pätschke
@paetscan -
 Barbara Gigerl
Barbara Gigerl
@barbaragigerl -
 Lukas Gerlach
Lukas Gerlach
@____salmon____ -
 Maria Eichlseder
Maria Eichlseder
@MariaEichlseder -
 Jonas - j²
Jonas - j²
@notimaginary_ -
 Daniel Weber
Daniel Weber
@weber_daniel -
 LosFuzzys
LosFuzzys
@LosFuzzys
Something went wrong.
Something went wrong.