
hackzzdogs
@hackzzdogsRed teamer || Lab Creator for Offensive Security and Cyberseclabs || 🙂Human
Similar User

@Octoberfest73

@n1ghtmar3_2421

@AtharvShejwal

@DrippyRobin

@0xdeaddood

@anthemtotheego

@netero_1010

@Geiseric4

@machari4_

@DebprasadBaner9

@tbhaxor

@N1tr0s_ken

@r0g3rmr3n00b

@ahmadi98_

@MayerA7x
Hi everyone, this is my first blog regarding my first red teaming engagement where I bypassed Microsoft Endpoint solutions using the features provided by Microsoft.😛 hackzzdogs.gitbook.io/how-we-bypasse… #EDR #redteam #redteaming #cybersecurity
We proposed renewal of our certificates (#CRTP, #CRTE and others) with an 8 hour live exam without any cost. Received a lot of great comments from our past students. Now throwing it open to everyone. Please RT for reach. How would you like your Infosec certs?
Quick POC this evening looking at how LAPS (v2) passwords are stored and decrypted on Active Directory (tl;dr, msLAPS-EncryptedPassword attr and NCryptStreamUpdate for crypto) gist.github.com/xpn/23dc5b6c26…

Dependency confusion - mismanaged by @Google security VRT giraffesecurity.dev/posts/google-r… Had the exploiter been malicious this could have led to product compromise, back door, and enterprise access.
Just submitted my talk proposal to Black Hat USA!🤞 Psyched to share some wild techniques that should burn for a long time after! #BHUSA
The actual truth of current red teaming🥴
Red Team 2.0 appears to become: 1) Give a machine on the internal network because phish fail. 2) Disable EDR because can't seem to bypass the EDR. 3) Can't figure out how to pivot network segment. 4) ... Dude, why not just ask to be put on the core banking system?
Finally, after 2 years of plan, I "Tried harder"🥴. Now I am a Offensive Security Certified Professional. #OSCP Just got a new Offensive Security credential via @Accredible for sgq.io/Fc7FYij via @offsectraining
So much great information here thanks for taking the time to put it together and share :)
I'm a Head of Finance at Google. I've interviewed 100s of candidates in my career and I know my decision within the first 7 minutes. Do these 5 things to prepare for the interview and I guarantee you'll impress recruiters and hiring managers at your dream company:
After years of using the default examples, I've finally started writing my own custom scripts using Impacket. Wanted to share a few examples that helped me during the learning process. Hope you enjoy! github.com/icyguider/More…
Great 🤩
We worked together with @_zblurx to pull this new feature on CME ! CrackMapExec can now authenticate using kerberos with login/pass/nthash/aeskey without the need of a KRB5CCNAME ticket env 🚀 But wait there is more! by adding this feature we can now mimic kerbrute features 🔥🫡

Great video🙂🔥
Mystified by HTTP/3 connection contamination? I've recorded a 5-minute, ultra simple explanation also covering the entire history of HTTP connection-reuse! youtube.com/watch?v=-mHjTE…
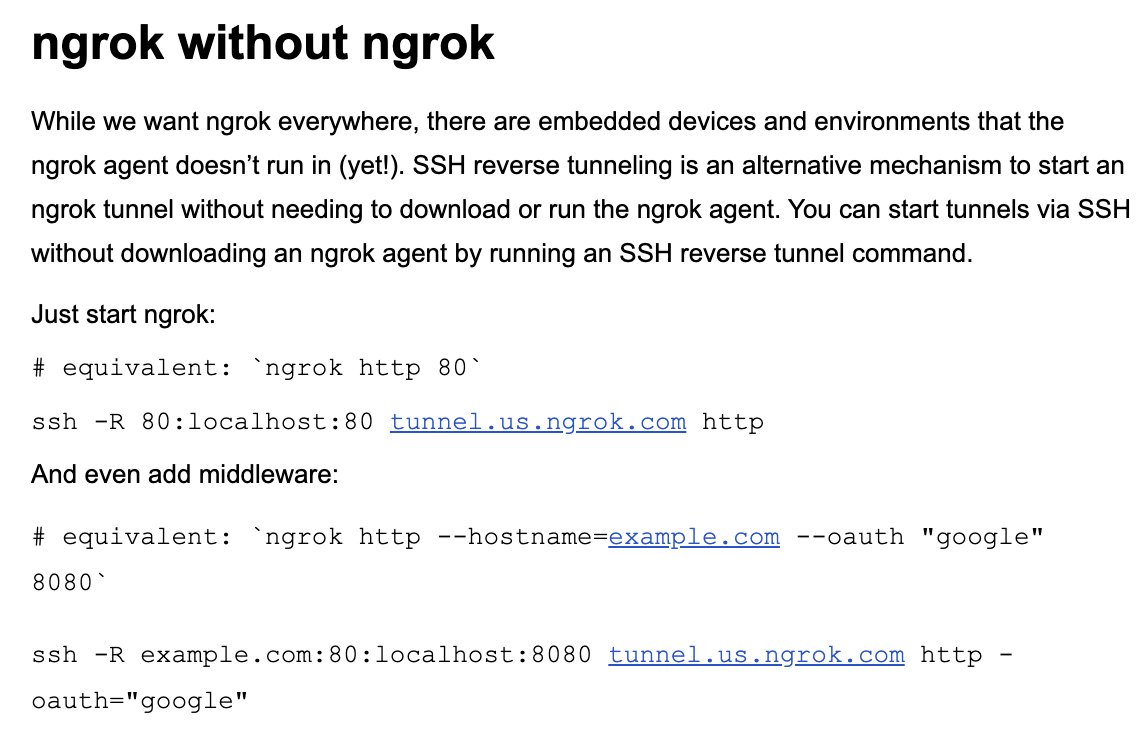
You can now use ngrok without even installing ngrok 🤯
The good old "attacker@attacker.com,victim@victim.com" strikes again github.com/advisories/GHS…
United States Trends
- 1. #IDontWantToOverreactBUT 1.233 posts
- 2. #Superman 44 B posts
- 3. #mondaymotivation 25,4 B posts
- 4. #SkylineSweeps N/A
- 5. Victory Monday 2.454 posts
- 6. John Williams 1.876 posts
- 7. Good Monday 57,6 B posts
- 8. SoftBank 9.327 posts
- 9. #IN_HALLUCINATION 39,1 B posts
- 10. James Gunn 17,2 B posts
- 11. Big Bass Xmas Extreme N/A
- 12. Look Up 108 B posts
- 13. Lamar 63,9 B posts
- 14. Man of Steel 2.372 posts
- 15. Freeland 26,7 B posts
- 16. $BOOST 12,3 B posts
- 17. Zimmer 3.754 posts
- 18. Schiff 59,9 B posts
- 19. Plymouth Rock N/A
- 20. Burna 35 B posts
Who to follow
-
 Octoberfest7
Octoberfest7
@Octoberfest73 -
 MD. GOLLAM RABBI
MD. GOLLAM RABBI
@n1ghtmar3_2421 -
 Atharv Shejwal
Atharv Shejwal
@AtharvShejwal -
 Robin Winchester
Robin Winchester
@DrippyRobin -
 leandro
leandro
@0xdeaddood -
 Shawn
Shawn
@anthemtotheego -
 Chris Au
Chris Au
@netero_1010 -
 Geiseric
Geiseric
@Geiseric4 -
 martin
martin
@machari4_ -
 Ravaan:)
Ravaan:)
@DebprasadBaner9 -
 ĐARK々MÁTTER
ĐARK々MÁTTER
@tbhaxor -
 N1tros
N1tros
@N1tr0s_ken -
 rsmnoob
rsmnoob
@r0g3rmr3n00b -
 M.Sadeq Ahmadi
M.Sadeq Ahmadi
@ahmadi98_ -
 Mayer.A7X
Mayer.A7X
@MayerA7x
Something went wrong.
Something went wrong.

































































































