Similar User

@eternalsakura13

@starlabs_sg

@YanZiShuang

@KeyZ3r0

@seal9055

@mj0011sec

@pwn_expoit

@80vul

@vv474172261

@_L4ys

@bestswngs

@linhlhq

@CurseRed

@P4nda20371774

@jq0904
dma-buf: heaps: Fix off-by-one in CMA heap fault handler - Patchwork patchwork.freedesktop.org/patch/611976/ @1ce0ear 没想到给大佬提交了🤣
Chomre delete this UAF.I missed this one🤡 chromium-review.googlesource.com/c/chromium/src…
UPSTREAM: binder: fix UAF caused by offsets overwrite (5843736) · Gerrit Code Review (googlesource.com)
Speaker YYJB will be presenting "How to Exploit in Key Isolation Services Vulnerabilities at SgHACK 2024 (sghack.org) #SgHACK #WhiskeyCon #Cybersecurity #CybersecurityinSG
Our researcher Slim (@HBh25Y) shared at @offbyoneconf: The Forgotten Treasure in Classic Targets: Despite powerful fuzzers like AFLplusplus & syzkaller, recent vulnerabilities show secrets lie deep in the code. Manual audits on Linux kernel & mobile decoders reveal many…

@offbyoneconf participants in 💡 deep-thoughts & fielding questions @ Q&A with @peterpan980927 & @st424204 from ✨ @starlabs_sg , at their presentation 𝐆𝐏𝐔𝐀𝐅 - 𝐔𝐬𝐢𝐧𝐠 𝐚 𝐠𝐞𝐧𝐞𝐫𝐚𝐥 𝐆𝐏𝐔 𝐞𝐱𝐩𝐥𝐨𝐢𝐭 𝐭𝐞𝐜𝐡 𝐭𝐨 𝐚𝐭𝐭𝐚𝐜𝐤 𝐏𝐢𝐱𝐞𝐥𝟖. Go go 🚀@starlabs_sg


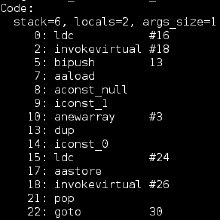
In this post I'll use CVE-2024-3833, a type confusion in v8 to gain remote code execution in the Chrome renderer sandbox: github.blog/2024-06-26-att…
today learn a lot.Thanks off by one!
United States Trends
- 1. Ravens 76,1 B posts
- 2. Steelers 103 B posts
- 3. Bears 109 B posts
- 4. Packers 68,8 B posts
- 5. Lamar 29,7 B posts
- 6. Jets 53,3 B posts
- 7. #HereWeGo 18,3 B posts
- 8. #GoPackGo 9.012 posts
- 9. Lions 87,9 B posts
- 10. Caleb 31,1 B posts
- 11. Justin Tucker 19,3 B posts
- 12. Taysom Hill 9.185 posts
- 13. Bills 95,8 B posts
- 14. Falcons 9.993 posts
- 15. WWIII 34,6 B posts
- 16. Russ 14,4 B posts
- 17. Browns 29,6 B posts
- 18. Worthy 45,5 B posts
- 19. Eberflus 8.663 posts
- 20. Colts 30,7 B posts
Something went wrong.
Something went wrong.