
Greenplan
@greenplan_itMalware Researcher and Threat Intelligence Analyst
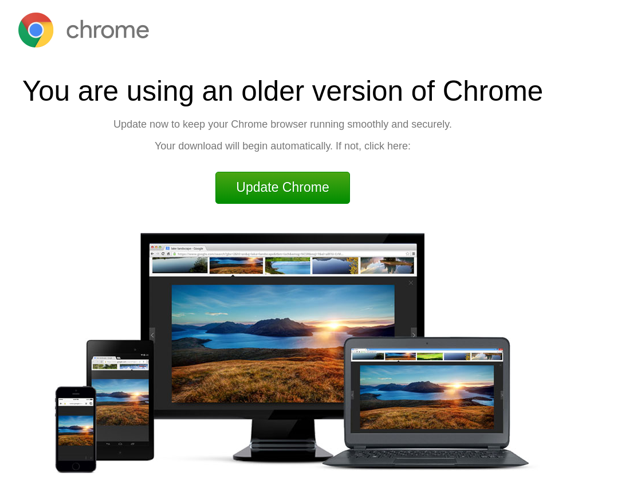
1/X Here's some details on recent SOCGholish / FakeUpdates initial infections and the TDS (Keitaro?) that goes along with it. This loader uses compromised sites to display a fake "browser update" themed lure that, when clicked, downloads the malware.
Emmenhtal Loader (PEAKLIGHT, MustardSandwich) is now "impersonating" Microsoft CertUtil app.any.run/tasks/37ea224d…

Very great resource for those who track ClearFake/ClickFix!!
🔍 TDR investigated the emerging #ClickFix social engineering tactic, which several intrusion sets adopted in 2024 to distribute their malware. Our research provides a chronological overview of the observed ClickFix campaigns and their victimology. blog.sekoia.io/clickfix-tacti…

New Blog: Deobfuscating BBTok loader, ConfuserEx variant with dnlib, Python and PowerShell by @marius_benthin and me #GDATATechblog #GDATA @GDATA #BBTok gdatasoftware.com/blog/2024/09/3…
We are now tracking 7 loader families across 68 active botnets. The most recent addition, not going to name fingers and point names but here is a hint: 🧹 📈Since May 2024 we have observed 21,256 payloads and 4,883 tasks🕵️♂️

My latest blog about Bulletproof hosting services! #Cybersecurity #Cybercrime #BulletproofHosting #BPH #TechBlog #CyberThreats #Infosec #ThreatIntelligence #CyberThreatIntelligence #CTI #InformationSecurity #Investigation #underground #forums cybercrimediaries.com/post/50-shades…
I have spent the last year building MalSearch the world's largest Malware Source Code Search Engine.🔥🔥 We are planning to add thousands of malware source code projects over the next couple months. Check it out: malsearch.com

Unpacking SSLoad: A #Rust loader with diverse delivery methods, new elusive loaders, implementation of dead-drop sites, multiple string decryption, and anti-debugging techniques. Dive into our detailed analysis of its loaders and payloads: intezer.com/blog/research/…



✍️My quick note about #DarkGate 📕How to extract AutoIt script and deobf to recover original code. 📕How to extract shellcode loader. 📕How to decrypt and extract the final #DarkGate payload. kienmanowar.wordpress.com/2024/06/06/qui…
As part of Operation Endgame we shared an initial one-off Special Report on IcedID/Latrodectus bot infections: shadowserver.org/what-we-do/net… Dashboard map view: dashboard.shadowserver.org/statistics/com… Details on Operation Endgame coordinated by @EC3Europol: europol.europa.eu/media-press/ne…

Wrote a quick blog post to document the recent change of #Gootloader's C2. I also included a rough timeline of their infrastructure changes since November 2022. gootloader.wordpress.com/2024/05/30/goo…
Hunt APTs by their images & artifacts! New blog on tracking adversaries using delivery-stage intel by @Joseliyo_Jstnk: blog.virustotal.com/2024/05/tracki…

🦔 📹 New Video: D3fack loader analysis ➡️ Inno Setup pascal script analysis ➡️ string deobfuscation with binary refinery ➡️ JPHP decompilation Sample was first described by @RussianPanda9xx youtube.com/watch?v=y09Zre… #MalwareAnalysisForHedgehogs #D3fackLoader
United States Trends
- 1. Thanksgiving 474 B posts
- 2. $CUTO 7.489 posts
- 3. Custom 73,5 B posts
- 4. Darnold 3.870 posts
- 5. #AskJage N/A
- 6. UNTITLED UNMASTERED N/A
- 7. Dodgers 65,2 B posts
- 8. Happy Birthday Steve N/A
- 9. JJ McCarthy N/A
- 10. #WednesdayMotivation 6.064 posts
- 11. #MigglesArmy 5.075 posts
- 12. #KFANVikes N/A
- 13. Vindman 1.613 posts
- 14. Deleted 55,2 B posts
- 15. #DeFi 26,2 B posts
- 16. Daniel Jones to the Vikings 3.384 posts
- 17. Lake Michigan 3.917 posts
- 18. Section 80 1.989 posts
- 19. Sharon Stone 28,7 B posts
- 20. Kevin O’Connell 1.638 posts
Something went wrong.
Something went wrong.























































































