Similar User

@bxmbn

@0xRAYAN7

@GodfatherOrwa

@sl4x0

@_2os5

@RahmatQurishi

@Tur24Tur

@Hammad7361

@RootxRavi

@7odamoo

@bug_vs_me

@lu3ky13

@nihad_rekany

@0x_rood

@01alsanosi
#bugbountytips Account Takeover When you sign up, try to register using existing email by adding \n at the end, it could sign you into someone's account/overwrite his account. ✍️ Example: {"email":"eman@example.com"} ↓ {"email":"eman@example.com\n"}


الحمدلله تأهلنا مع ال32 فريق الى دور المجموعات وضمن الفرق الاساسية (افضل 8 فرق) في مسابقة كأس العالم هكر ون 2024 🇸🇦💪 Saudi Arabia qualified to group stage with 32 teams and as one of the main teams for the next round (Top 8) 🇸🇦💪 #AWC2024
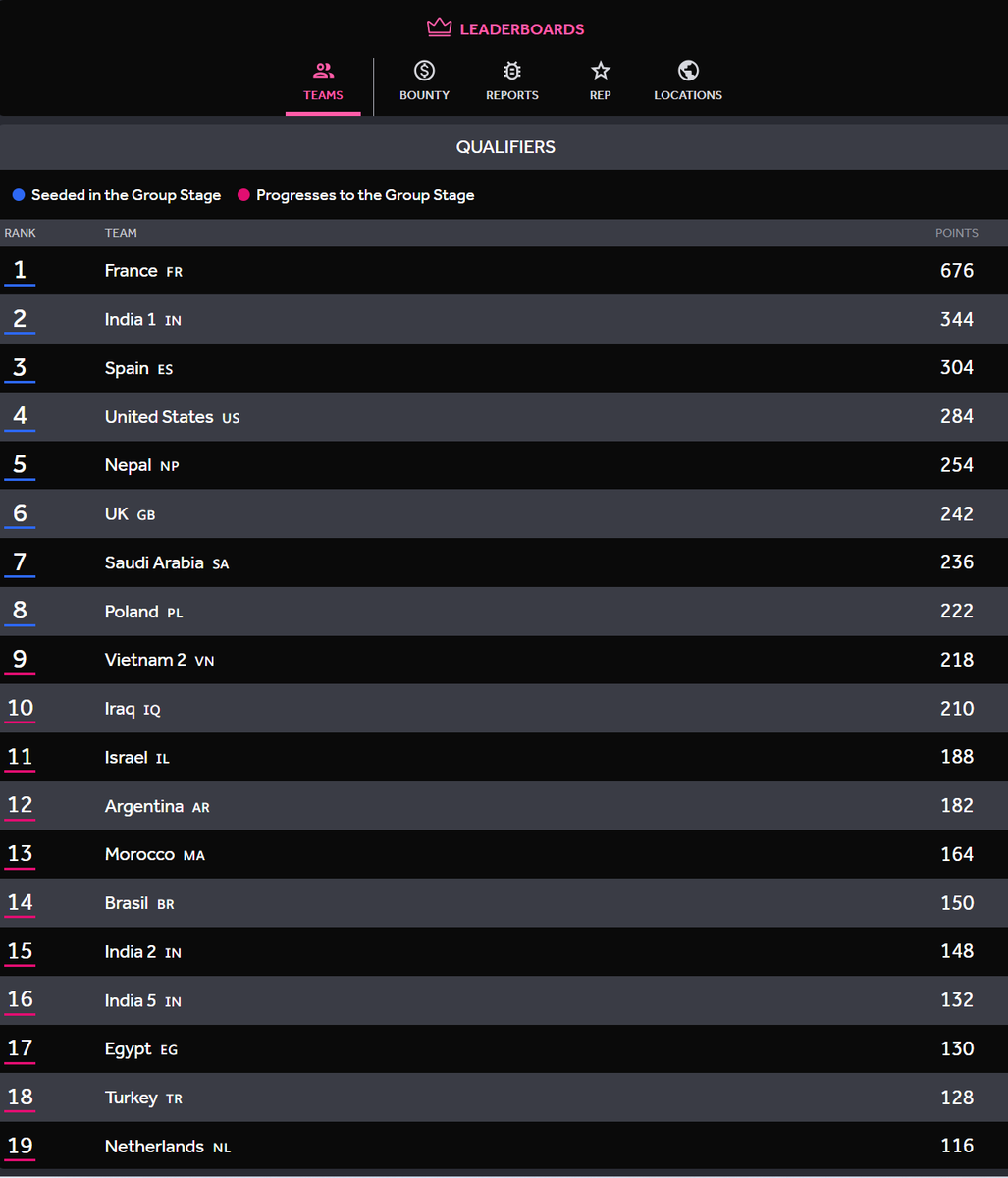
تم قبول ممثلي المملكة العربية السعودية 🇸🇦 لمسابقة AWC 2024 هكر ون @Hacker0x01 🏆 المشاركين: @AMakki1337 @0x_rood @eman_yazji @r00t_nasser @0xRaw @0xRAYAN7 @Ahmed0Makki @Ibrah1m_0x @leetibrahim @AlHomaidNoor @abdlah_md @stuipds @Liliexx2 @omarzzu @9yk @Dr_Ro0T

جاهزين لكأس العالم هكر ون ٢٠٢٤ 🔥 🏆 للمشاركة وتمثيل المملكة العربية السعودية 🇸🇦 يرجى تعبئة النموذج: docs.google.com/forms/d/e/1FAI…

الحمدلله تأهلنا من دور المجموعات بأصعب مجموعة في كأس العالم 2023 هكر ون 🔥💪🇸🇦 شكرا لكل اللي شارك معنا في المسابقة وتمنياتكم لنا بالتوفيق في المباريات القادمة. @AMakki1337 (C) @eman_yazji @0xRAYAN7 @Ahmed0Makki @stuipds @leetibrahim @0xRaw @aa_8989 @0x_rood @0xNasser_…

Today marks the start of the 2023 #AmbassadorWorldCup! 29 teams, and over 600 hackers are taking on the challenge to help our AWC partners @OpenSea, @ShopifyEng, Epic Games, @TheParanoids and @stripe strengthen their security. Who will come out on top? bit.ly/400LpGY

#bugbountytips Account takeover by bypassing rate limit When you try to brute force the OTP rate limit will stop you, try to add this header to bypass it ✍️ X-Forwarded-For: 127.0.0.1
#bugbountytips Sometimes when you visit a website using burp suite cloudflare stops you, but when you disable the proxy it works. here is how to bypass it using burp suite ✍️ Enable match and replace with the following: pastebin.com/raw/HRZzeZLJ #Cloudflare #BugBounty

تم اختيار ممثلي المملكة العربية السعودية بمسابقة World Cup 2023 هكر ون 🏆🇸🇦 - @AMakki1337 (C) - @0xRaw - @0xRAYAN7 - @aa_8989 - @0xNasser_ - @eman_yazji - @Hattan_515 - @r00t_nasser - @3zizMe_ - @0x_rood - @GodfatherOrwa - @Ahmed0Makki - @Mohamed87Khayat
When you hunt on a shopping website try this trick: Add these items to your cart Item 1: 50$ Item 2: 49$ Change the quantity of Item 2 to -1 (negative amount) Subtotal: 1$ With this trick you can buy Item 1 for 1$ #bugbountytips #bugbountytip #bugbounty
Hacker Cup @Bugcrowd 😎🔥 With the best collaborator in the world @AMakki1337 #BugBounty #bugbountytips

Sometimes parameter pollutions can also lead to IDORS: if GET/api_v1/docs? user_id=youruserid Send it like this: GET /api_v1/docs? user_id=youruserid&user_id=anotheruserid or, GET /api_v1/docs? user_id=anotheruserid&user_id=youruserid Rare but can be tried:) #bugbountytips
الحمدلله حصلت على المركز الثاني في كأس منصة مكافآت الثغرات في حدث بلاك هات🥈 I placed 2nd place in Bug Bounty Cup during Black Hat MEA event🥈 #bugbountytips #bugbountytip #bugbounty #BHMEA22 #بلاك_هات22 @Faisal @malobeiwi @SAFCSP @BugBountySA @Blackhatmea

Can you spot the vulnerability? 🔎 Show us how you'd be able to read ANY local file you want in the comments 👇 The best explanation gets a 25€ SWAG voucher! 👕

SSRF Tip If you found something similar to this in your request body {"endpoint":"/adduser","name:"test"} add @burpcollab.com before / {"endpoint":"@burpcollab.com/adduser"} in the backend it will be "https://website@burpcollab.com/adduser" #bugbountytips


United States Trends
- 1. #AcousticPianoCollection 2.039 posts
- 2. $CUTO 7.484 posts
- 3. Jaguar 197 B posts
- 4. #TSTheErasTour 1.906 posts
- 5. #ASKJAGE N/A
- 6. #wednesdayfeelings 3.151 posts
- 7. Hobi 68,4 B posts
- 8. $TGT 3.828 posts
- 9. Ray Lewis 1.714 posts
- 10. Hampton Inn 3.722 posts
- 11. Vatican City N/A
- 12. Vinatieri N/A
- 13. Jay Leno 6.936 posts
- 14. Hump Day 18,9 B posts
- 15. #WorldChildrensDay 21,7 B posts
- 16. Good Wednesday 32,9 B posts
- 17. DeFi 112 B posts
- 18. Antonio Gates N/A
- 19. Bud Light 7.852 posts
- 20. Liam Payne 97,7 B posts
Who to follow
-
 🇪🇨🍫
🇪🇨🍫
@bxmbn -
 0xRAYAN
0xRAYAN
@0xRAYAN7 -
 Godfather Orwa 🇯🇴
Godfather Orwa 🇯🇴
@GodfatherOrwa -
 Abdelrhman Allam 🇵🇸
Abdelrhman Allam 🇵🇸
@sl4x0 -
 Fares
Fares
@_2os5 -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 Tur.js
Tur.js
@Tur24Tur -
 Hammad 🇵🇰🇵🇸
Hammad 🇵🇰🇵🇸
@Hammad7361 -
 Ravindra Lakhara 🇮🇳
Ravindra Lakhara 🇮🇳
@RootxRavi -
 Mahmoud Hamed
Mahmoud Hamed
@7odamoo -
 Deepak bug_vs_me
Deepak bug_vs_me
@bug_vs_me -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 Nihad
Nihad
@nihad_rekany -
 🇸🇦 ROOD | GOAT
🇸🇦 ROOD | GOAT
@0x_rood -
 Alsanosi
Alsanosi
@01alsanosi
Something went wrong.
Something went wrong.