Sohom Datta
@doas_matroshkyaPhD student NCSU, CS'23 Manipal, open-source dev working on VisibleV8, Wikimedia
Similar User

@sanchitrckbttm

@AmanPriyanshu6

@an_kitna

@SupritiVijay

@thisis_hsr

@sanyasingla15

@aaylmaooo

@imniminjoshi

@rajat18agarwal

@surroorian

@bunnypanwar

@routrayswadhin

@nayak_shamanth

@dhaniyapattaa

@osheeeeeeeeen
I’m recruiting PhD students interested in system security/privacy, trustworthy ML, @UCLA ECE/CS for Fall 2025! Please reach out via email anytime or find me at @acm_ccs next week. Retweets are greatly appreciated!
I’m planning to hire 2 PhD students in Fall25 at @KhouryCollege! How do we make privacy easier for people? How do we address people’s real privacy needs objectively and subjectively? How does AI play a role in introducing and mitigating risks? Talk to me at #UIST2024 #HCOMP2024
How does it feel like to do world-class research? If you are a CS undergrad who is interested in our topics, the Software Security group at #MPI_SP is hiring interns for summer & winter 2025! Details: 📅 01 November 2024 ✍️ cis.mpg.de/internships/ 🛡️ mpi-softsec.github.io
We've had to block what we assume are ai companies spamming our APIs instead of downloading our freely available database dumps over here at Wikipedia
Are you into hypervisor security and fuzzing? Consider applying for a PhD position in my group. More info: ali-abbasi.info
i’ll never stop messing with companies 💖

A quick way to check if this is enabled: Run the following in the developer console ``` await chrome.runtime.sendMessage( 'nkeimhogjdpnpccoofpliimaahmaaome', { method: 'cpu.getInfo' } ); ``` on meet.google.com, if it comes back with info, it's enabled.

So, Google Chrome gives all *.google.com sites full access to system / tab CPU usage, GPU usage, and memory usage. It also gives access to detailed processor information, and provides a logging backchannel. This API is not exposed to other sites - only to *.google.com.
🚫 DOM XSS, begone! 👋 Discover how we used Trusted Types to protect AppSheet, and how that can inform your own web application's journey to a safer security posture where DOM XSS vulnerabilities are a thing of the past. bughunters.google.com/blog/603789066…
The award-winning Qualys Threat Research Unit (TRU) has discovered a critical vulnerability in OpenSSH, designated CVE-2024-6387 and aptly named "regreSSHion." This Remote Code Execution bug grants full root access, posing a significant exploitation risk. blog.qualys.com/vulnerabilitie…
Google stated that "In 2024, less than 1% of all installs from the Chrome Web Store were found to include malware". But how big is this 1% exactly? You can check it out by reading our @ASIACCS2024 paper arxiv.org/pdf/2406.12710 & attending @SherylHsu02 talk on July 4! CC @CISPA
280 Million Google Chrome Users Installed Dangerous Extensions, Study Says trib.al/NJLg1FH
The libarchive e8 vulnerability is actually really cool, but the ZDI advisory doesn't explain why it's so wild lol. For some reason, I know about RAR filters, so let me provide the background. 🧵 1/n
Our second keynote speaker for #SecWeb2024 will be Prof. Alexandros Kapravelos @kapravel from NC State! He will present "Unveiling Web Threats: Insights from JavaScript Behavior". See you in San Francisco on May 23rd! @IEEESSP @blueminimal
I love how you can see literally see the level of exasperation from the maintainers grow over time




“But social engineering requires skill”. Wrong. It requires you to be a bigger asshole than your victim. The only “skill” you need is to ignore all empathy. That’s what I love about hacking. It doesn’t require a human victim to still be fun. Just pure technical skill.
Hi all! I'm looking to hire research interns for the Summer/Fall 2024 to work with me at MPI-SP in Bochum, Germany, research the harms of emerging technologies. More information can be found at mhaidli.github.io/workingwithabr…. Please share among your networks!
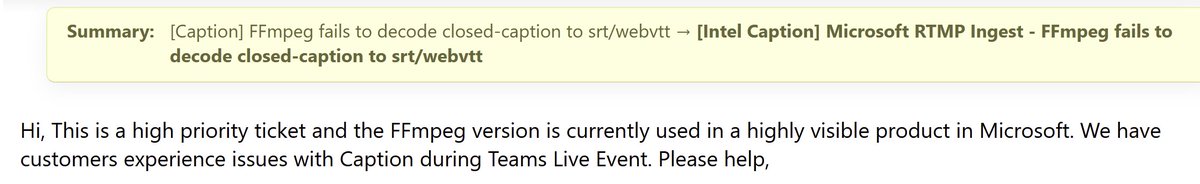
The xz fiasco has shown how a dependence on unpaid volunteers can cause major problems. Trillion dollar corporations expect free and urgent support from volunteers. @Microsoft @MicrosoftTeams posted on a bug tracker full of volunteers that their issue is "high priority"
Jia Tan's git commit to turn off Landlock sandboxing one week after Lasse Collin improved it. I understand the sandbox is for xz, the command line tool, and Jia did not need to disable it for the SSHD backdoor. 🤔The xz command also activates the backdoor?

United States Trends
- 1. #UFC309 314 B posts
- 2. Jon Jones 193 B posts
- 3. Jon Jones 193 B posts
- 4. Jon Jones 193 B posts
- 5. Chandler 89,7 B posts
- 6. Oliveira 74,1 B posts
- 7. Kansas 23,6 B posts
- 8. #discorddown 7.017 posts
- 9. Bo Nickal 9.238 posts
- 10. Do Bronx 11,5 B posts
- 11. ARod 2.207 posts
- 12. Dana 265 B posts
- 13. Pereira 11,7 B posts
- 14. #BYUFootball 1.425 posts
- 15. Mike Johnson 47 B posts
- 16. Rock Chalk 1.449 posts
- 17. Alec Baldwin 8.801 posts
- 18. #MissUniverse 452 B posts
- 19. Big 12 16,8 B posts
- 20. Keith Peterson 1.411 posts
Who to follow
-
 sanchit
sanchit
@sanchitrckbttm -
 Aman Priyanshu
Aman Priyanshu
@AmanPriyanshu6 -
 ankita.v
ankita.v
@an_kitna -
 Supriti Vijay
Supriti Vijay
@SupritiVijay -
 Harsh Singh Rathore
Harsh Singh Rathore
@thisis_hsr -
 Sanzz
Sanzz
@sanyasingla15 -
 aaylmao
aaylmao
@aaylmaooo -
 Naman Joshi
Naman Joshi
@imniminjoshi -
 Rajat Agarwal
Rajat Agarwal
@rajat18agarwal -
 RT
RT
@surroorian -
 Bunny
Bunny
@bunnypanwar -
 swadhin
swadhin
@routrayswadhin -
 Shamanth R Nayak
Shamanth R Nayak
@nayak_shamanth -
 Ankit
Ankit
@dhaniyapattaa -
 pinky
pinky
@osheeeeeeeeen
Something went wrong.
Something went wrong.