Similar User

@inhibitor181

@gwendallecoguic

@hd_421

@sergeybelove

@dnkolegov
So, you can upload a file to the web app.. Bonus! Repo with slightly old exploits for image upload: github.com/barrracud4/ima… XMind source: github.com/hackerscrolls/… Thanks to hacktricks and @HolyBugx for new tricks (at least for us) book.hacktricks.xyz/pentesting-web…
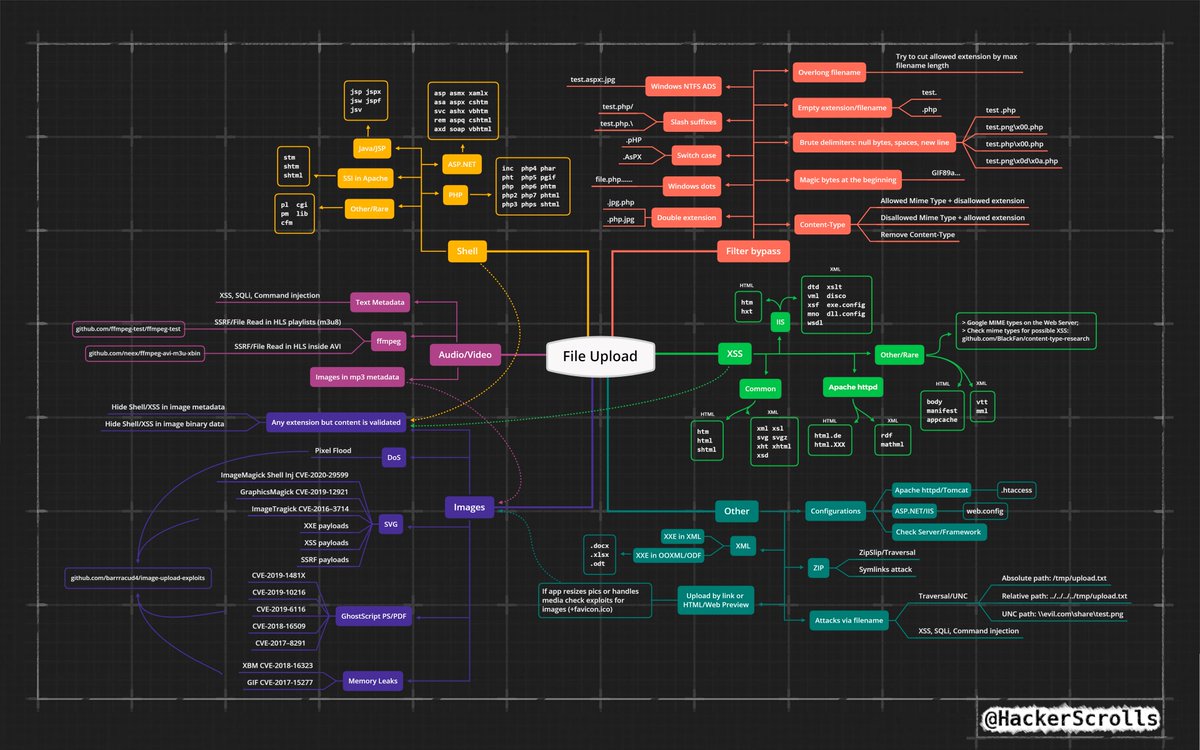
My File Upload Checklist, detailed version of @hunter0x7 checklist, and also some extra methods I personally use and gathered during the time. #BugBounty #BugBountyTip #BugBountyTips #TogetherWeHitHarder #InfoSec




Found a hidden HTTP param? Look deeper, maybe there is a mass assignment/autobinding vulnerability. Sometimes changes in objects are hidden too and you need to closely explore the app. Source: itzone.com.vn/en/article/mas… #CyberSecurity #BugBountyTip #BugBounty

Looking for a stable reverse proxy for pivoting? Check frp! Useful when you've hacked a server and want to establish a channel to the internal network. A lot of options for pivoting, multiplatform and easy to use. github.com/fatedier/frp #CyberSecurity #Pentest #RedTeam

We often get confused how Samesite affects cookies in different attacks in modern browsers. So, we have made a memo and now share it with you. #CyberSecurity #BugBountyTip #BugBounty

We have combined all the tricks we know about SSRF into a single mindmap. If we missed something, write about it in the comments! High resolution: raw.githubusercontent.com/hackerscrolls/… XMind source: github.com/hackerscrolls/… #CyberSecurity #BugBountyTip #BugBounty

Incredible mindmap about hacking iOS applications by @hd_421 Pay attention, we have prepared two versions: 1. Full Security Assessments 2. Shorter BugBounty version XMind source: github.com/hackerscrolls/… #CyberSecurity #BugBountyTip #BugBounty #iOS

We continue to talk about attacks on CORS. This time, we have prepared a set of ideas for bypassing lists of allowed hosts. #CyberSecurity #BugBountyTip #BugBounty

There is a popular opinion: bad CORS like <Access-Control-Allow-Origin: *> is unexploitable. Browser won't send cookies in this case. It is a delusion. You can exploit it with a Chrome cache feature! For example: hackerone.com/reports/761726 #BugBountyTip #CyberSecurity #BugBounty

Next up on #HITBLockdown002 Track 1: "The Weakest Element of Acquiring Bank Infrastructure" Presented by Ilia Bulatov & Gleb Cherbov Starts 17:00 SGT at youtu.be/Yp7W4hiLpJY Ask questions via our Slido channel #askinthebox



#HITBLockdown002 D2T1 - The Weakest Element of Acquiring Bank Infrastructure - Ilia Bulatov & Gleb Cherbov - conference.hitb.org/hitb-lockdown0…
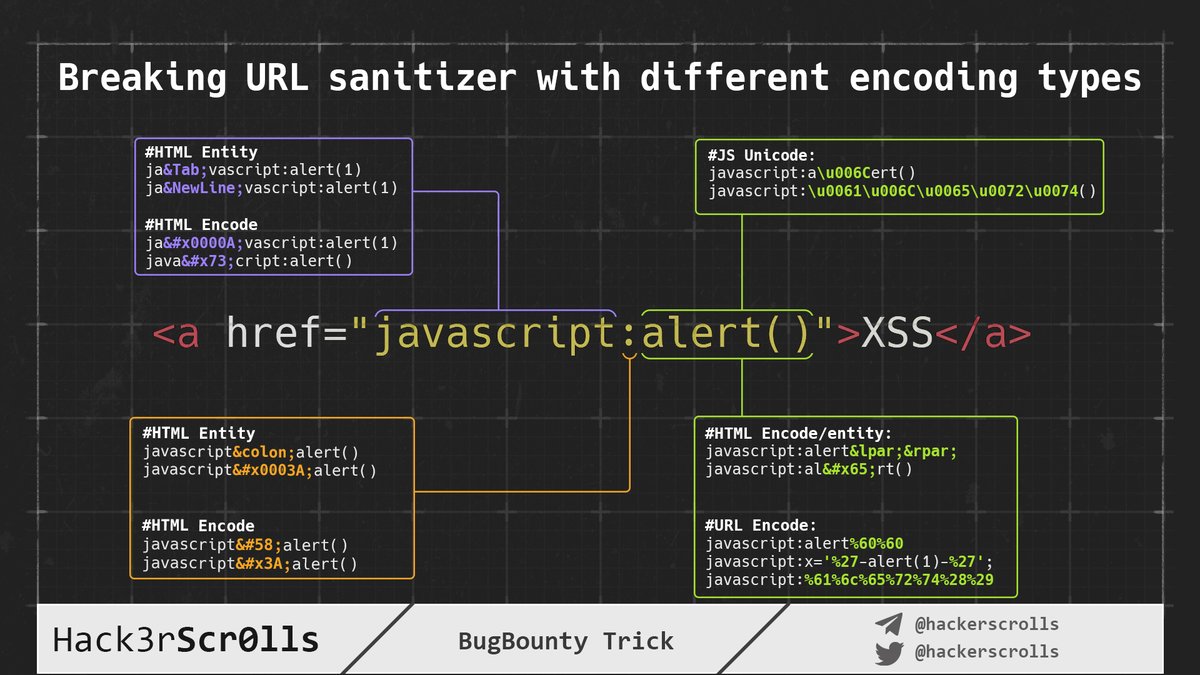
Last time we showed you how to use encodings in <a>. Now we've made a scheme what symbols in which points you can inject to bypass WAF, filters, sanitizers. gist.github.com/hackerscrolls/… #BugBounty #CyberSecurity #BugBountyTip

Sometimes you can control the href value in HTML tag<a>. So it's a good place for XSS payload! We've created a scheme how to use various encodings in href to bypass filters. gist.github.com/hackerscrolls/… @XssPayloads #BugBountyTip #Bypass
You asked for something about OAuth — we did. Here is a mindmap about hacking OAuth 2.0. We tried to cover all possible ways even with low impact. Our inspiration was homakov.blogspot.com/search?q=oauth Thanks to @homakov for outstanding articles. #BugBountyTip #CyberSecurity #BugBounty

Faced with CSRF protection? Try to bypass it! Save these 6 common CSRF bypasses that we use too. #BugBountyTip

SSRF + CRLF + HTTP Pipeline + Docker API = RCE… How dangerous is Request Splitting, a vulnerability in Golang or how we found the RCE in Portainer and hacked Uber link.medium.com/dSWQ6ewPL6
Sometimes there is no time to install/configure a fully functioning server. Here are 6 simple servers which can be used during pentest. Catch SSRF callbacks and exploit OOB attacks! Check the replies, there are commands to install and run them. #BugBountyTip #Pentest 1/7

We have prepared a mindmap for you with 16 ways how to perfom 2FA security testing. It is based on our practical experience and articles by @0xw2w and @ahack_ru bit.ly/2T95RWU blog.deteact.com/common-flaws-o… #BugBountyTip #TogetherWeHitHarder

Sometimes restrictions on "/admin" page can be easily bypassed. You should always check this simple tricks for easy win! #BugBountyTip #BugBounty #YourNextBugTip

WebArchive greatly expands your knowledge about the target. WayBackUrls is an awesome tool written by @TomNomNom It fetches all the URLs from WebArchive for a domain and it's subdomains. github.com/tomnomnom/wayb… #BugBountyTip

United States Trends
- 1. #ForTT_socideveloper_com N/A
- 2. #SendeTTol_wp_О85О3О329О6 N/A
- 3. #BuradaOl_wp_О85О3О329О6 N/A
- 4. Syria 1,2 Mn posts
- 5. Assad 1,02 Mn posts
- 6. Good Sunday 57,1 B posts
- 7. Bama 43,7 B posts
- 8. Clemson 61,4 B posts
- 9. #HBD22ndBeckySoloConcert 1,13 Mn posts
- 10. #UFC310 163 B posts
- 11. REBECCA STAGE QUEEN B 1,12 Mn posts
- 12. Penn State 43 B posts
- 13. Pantoja 44,6 B posts
- 14. Ghana 148 B posts
- 15. Oregon 69,4 B posts
- 16. trisha paytas 6.749 posts
- 17. ISIS 129 B posts
- 18. Iran 310 B posts
- 19. Damascus 436 B posts
- 20. Rangchu 1.427 posts
Something went wrong.
Something went wrong.