Similar User

@Silvia_Felici

@reecdeep

@TheAudioHead

@BModularis

@andreasurbone

@MagdyHenidak

@cinzia_ercolano

@sonobiondascusa

@JAMES10GG

@InfoSecLeader

@BenguettaiaRida

@pavel_cmp

@Netbanger4

@solclarin

@jacopomorelli1
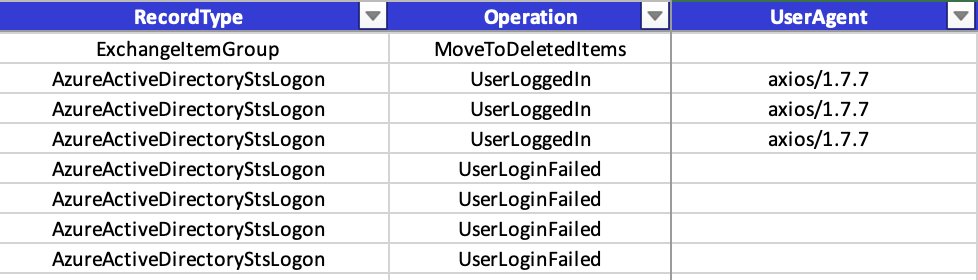
Analyzed a phishing case in M365: attacker bypassed MFA using axios HTTP client, leaving a telltale "axios/1.7.7" in sign-in logs. Lesson: regularly check sign-in logs for unusual user-agents to spot suspicious activity.
I developed an SSH client rootkit to test EDR detection. When a user logs in, it captures the root password and sends it covertly via a DNS TKEY record. With high daily DNS traffic, EDR systems are unlikely to flag this, as analyzing every query would impact performance.

In 1974, Steve Jobs came to India in search for enlightenment. 7 months later, he returned with a philosophy that would later build Apple into a $1 trillion empire. Here’s the philosophy: 🧵

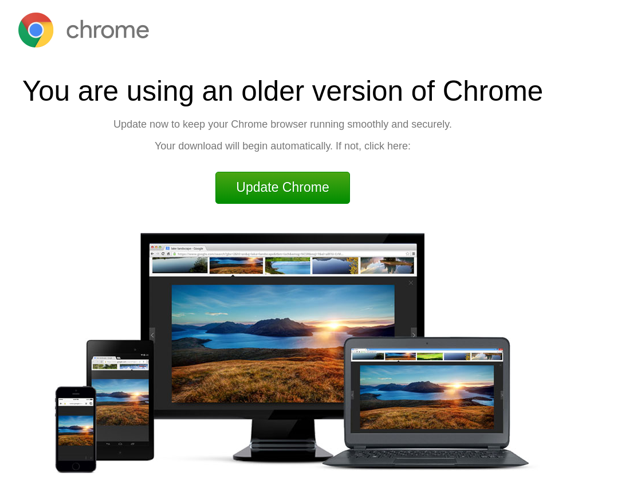
1/X Here's some details on recent SOCGholish / FakeUpdates initial infections and the TDS (Keitaro?) that goes along with it. This loader uses compromised sites to display a fake "browser update" themed lure that, when clicked, downloads the malware.
This incident was identical to the behavior of a compromised account as described in this recent article microsoft.com/en-us/security… --- TimeLine (9 days session) --- [Day 1] Initial Compromise - The victim received a phishing email with a subject line similar to "… shared ……

Cyberoo’s research on the illegal sale of a database with 60 million Italian records reveals a critical need for stronger data protection.

Had occassion to dig into ADCS and SCCM for the first time. Seriously impressive work from @tifkin_, @harmj0y, @subat0mik, @_Mayyhem and others over at @SpecterOps Super professional presentation of information which led to some high impact easy wins. github.com/subat0mik/Misc…
🚨🕷️ Proud to share my latest research on the LUNAR SPIDER campaign. Our findings reveal how RaaS operators leveraged LUNAR SPIDER’s malware, including IcedID and the Latrodectus loader, along with Brute Ratel C4 infrastructure, to enable their attacks on the financial sector.…

Working on a script that, when run, automatically extracts all browser data on the system—including passwords, cookies, history, and bookmarks—and sends it to my server.
This book is one of the best that gets into memory forensics, exploring how to analyze memory dumps for security investigations. It beautifully covers the structure of memory, process address spaces, and techniques for uncovering evidence of malware or attacks.

Offensive Security Tool: TerminatorZ TerminatorZ is developed by Chris Abou-Chabké from Black Hat Ethical Hacking and is an efficient web security tool designed to scan for potential vulnerabilities in your web applications. It uses a combination of advanced techniques and…
United States Trends
- 1. Jake Paul 970 B posts
- 2. #Arcane 225 B posts
- 3. Jayce 49,9 B posts
- 4. #SaturdayVibes 3.026 posts
- 5. Good Saturday 25,7 B posts
- 6. Serrano 237 B posts
- 7. #saturdaymorning 2.057 posts
- 8. Vander 16,4 B posts
- 9. #SaturdayMotivation 1.971 posts
- 10. Pence 81,5 B posts
- 11. #HappySpecialStage 94,4 B posts
- 12. maddie 20,6 B posts
- 13. Isha 38,6 B posts
- 14. Jinx 108 B posts
- 15. WOOP WOOP 1.382 posts
- 16. Rizwan 8.600 posts
- 17. Caturday 7.170 posts
- 18. John Oliver 14,2 B posts
- 19. Father Time 10,7 B posts
- 20. Fetterman 36,5 B posts
Who to follow
-
 Silvia Fel
Silvia Fel
@Silvia_Felici -
 reecDeep
reecDeep
@reecdeep -
 AudioHead
AudioHead
@TheAudioHead -
 Brunella modularis
Brunella modularis
@BModularis -
 Andrea Surbone
Andrea Surbone
@andreasurbone -
 Specter
Specter
@MagdyHenidak -
 Cinzia Ercolano
Cinzia Ercolano
@cinzia_ercolano -
 Bionda 🎀
Bionda 🎀
@sonobiondascusa -
 JJG,
JJG,
@JAMES10GG -
 Gh0sT*23
Gh0sT*23
@InfoSecLeader -
 Rida Benguettaia
Rida Benguettaia
@BenguettaiaRida -
 Paolo
Paolo
@pavel_cmp -
 Netbanger
Netbanger
@Netbanger4 -
 vanellope
vanellope
@solclarin -
 jacopo morelli
jacopo morelli
@jacopomorelli1
Something went wrong.
Something went wrong.









































































































