Similar User

@xxxxyyyy99

@FlatleyAdam

@niksadecimal

@Goody537

@ckj1232

@PflashPunk

@St0rmNT85
Reverse Engineering and exploit development Download 100% Free For First 1000 User's.. Simply: 1. Follow (So I Will Dm) 📥 2. Like and Repost 3. Comment “ Send ” to receive your copies!! 📚

Proxy Phishing is taking off to the degree that it seems to be becoming the rule and not the exception. Here is a video of how fast you can pull it off and with MFA bypass. For protection and detection this is better than anything I could write: jeffreyappel.nl/aitm-mfa-phish…
Playing dirty with AV/EDR/sandbox, part 4: the webserver compiles a new exe file each time you download it. And the exe downloads a new file from the same server and runs it. 😈 Enjoy C: github.com/gtworek/PSBits… EXE: hxxp://20230906t192146.ltiapmyzmjxrvrts.info/v4/whatever.exe

microsoft-edge + ms-search + MSDT path traversal 0day = fun of 2-clicks (one click additional due to Protected View if docx is coming from remote btw).
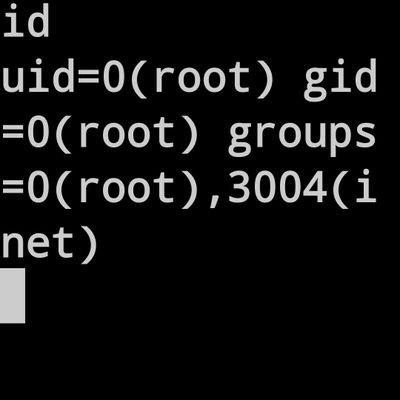
webarchive > internal.domain.com > dirsearch > found .git/index file used gin to read the index file pip3 install gin gin <index file> found .env file opened > full of credentials access to their mysql database connect using #bugbounty
Bypassing most FILE Uploads filters for $$$$ * .htaccess <- upload htaccess * file.svg <- uploading svg = xss * file.SVg <- must try case mismatch * file.png.svg * file.php%00.png * file.png' or '1'='1 * ../../file.png * file.'svg <- invalid ext. #bugbountytips #BugBounty
Some github search keywords. Assuming target(.)com *"target(.)com" password *"target(.)com" "pass" 'email' *"target(.)com" "api" *"target(.)com" FTP *"target(.)com" SMTP *"target(.)com" LDAP *"target(.)com" PEM (For Keys) If found nothing try to change it.
Web Apps Testing: Focuses on gathering more info about the app and mapping out the network / infrastructure where the app is hosted. Popular tools commonly used during Web Apps Testing include: W3af Burp Suite SQLMap Metasploit Hydra John Ripper Skipfish Ratproxy Wfuzz Watcher
Dump AES keys from wireless Logitech receivers using Chrome Browser. Demo page: mame82.github.io/munifying-web/ Source: github.com/mame82/munifyi…
United States Trends
- 1. Thankful 66,7 B posts
- 2. #RTXOn 7.501 posts
- 3. #PMSLive 3.977 posts
- 4. #twug 3.257 posts
- 5. Sharon Stone 2.784 posts
- 6. Happy Thanksgiving 29,4 B posts
- 7. $ELONIA 1.702 posts
- 8. Hezbollah 160 B posts
- 9. Creighton 2.581 posts
- 10. Lebanon 192 B posts
- 11. #PumpRules 3.836 posts
- 12. Johnie Cooks N/A
- 13. Xanadu 1.268 posts
- 14. Rivian 9.679 posts
- 15. Mack Brown 5.064 posts
- 16. $CUTO 7.456 posts
- 17. #GivingTuesday 3.290 posts
- 18. Broyles Award N/A
- 19. Avocados 10,3 B posts
- 20. Billboard 581 B posts
Something went wrong.
Something went wrong.