Justas Masiulis
@JustasMasiulisRE | Windows Kernel | @the_secret_club
Similar User

@namazso

@mrexodia

@aidankhoury

@vm_call

@_xeroxz

@HyperDbg

@daaximus

@aall86

@33y0re

@iPowerPower

@Intel80x86

@standa_t

@PetrBenes

@_can1357

@_0xnobody_
Happy to release a neat little plugin for IDA Pro! Bitfield and bitflag accesses have been an annoyance that requires another window open and constant fiddling. You can now fix that with just a few key presses! github.com/JustasMasiulis…

New blog entry: C++ Unwind Metadata: A Hidden Reverse Engineering Bonanza msreverseengineering.com/blog/2024/8/20…

YOLO in life, not in cryptography. Using Custom hash constructions is risky; here’s why and what standardized methods to use instead. buff.ly/3WTYnXh

🚨 Trying to find the NTDLL base? 🔥 EDRs ♿ hate this ONE WEIRD TRICK! LEARN HOW YOU 🫵 CAN TOO! #shocking #redteamtips #security #redteam

Excited to share my latest article: PgC - a novel approach to disable Patchguard during runtime using basic memory management principles. It has worked against every version of Patchguard for the last 7 years, without needing any updates! blog.can.ac/2024/06/28/pgc…
“Previously available to Windows security features only, VBS enclaves are now available to third-party application developers” Very cool. Waiting for more details :)
New blog announcing new security capabilities for Windows 11 at #BUILD microsoft.com/en-us/security…
vanguard 2 now on league of legends, cheating to be deprecated this patch leagueoflegends.com/en-au/news/gam…
Seems like there is malware abusing GitHub attachments to create file links in legitimate repositories. Here's a funny example github.com/microsoft/MSRC… nothing special, but just seemed neat.
I try an avoid this hellsite, but I did a quick dive into sudo in Windows and here are my initial findings. tiraniddo.dev/2024/02/sudo-o… The main take away is, writing Rust won't save you from logical bugs :)
Has been out for a while, but does anyone know what does MS plan to do with *SyscallProvider* stuff that replaces the *AltSystemCallHandler*? It also seems to not be protected by "classic" PG (only SK based protection)🙈
My new blog post for @huntandhackett is finally out! 🥳 "The Definitive Guide to Process Cloning/Forking on Windows" 🔥 Technical and design decisions, attack and defense vectors, features and limitations, code samples… The blog covers them all! huntandhackett.com/blog/the-defin…
Today, we are releasing RPC Investigator, made for exploring RPC clients and servers on Windows. This .NET application builds on the NtApiDotNet platform, adding features that offer a new way to explore RPC blog.trailofbits.com/2023/01/17/rpc…
Presenting D-Generate , syscall tracing as its supposed to be! raw.githubusercontent.com/jonaslyk/temp/… usage: dg cmd.exe - displays all syscalls done by process with cmd.exe as imagefile. dg 4736 - by pid 4736 dg - just everything example of recording: raw.githubusercontent.com/jonaslyk/nt/ma…
Improving MBA Deobfuscation using Equality Saturation by @fvrmatteo and @mr_phrazer secret.club/2022/08/08/eqs…
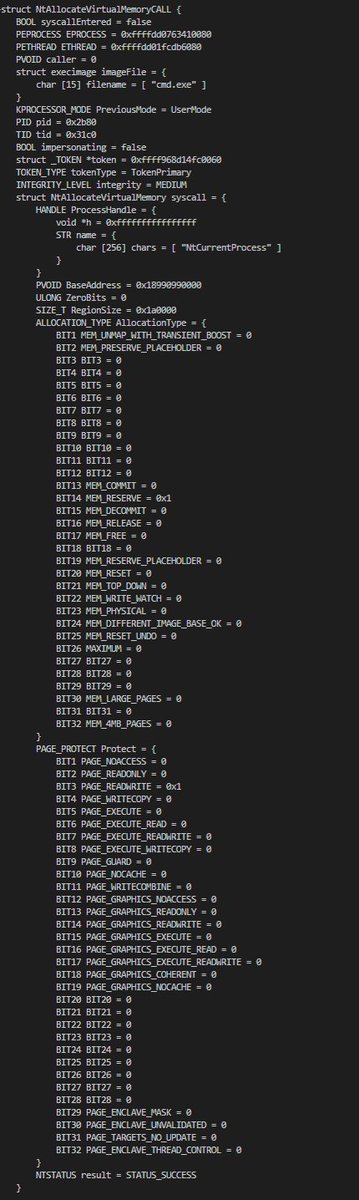
My full-binary, static type reconstruction toolkit is becoming increasingly robust. Pictured are fully-automated results from RPCRT4/x64, an experiment to see if public PDBs make the problem any easier than the stripped case (answer: not by much). Bootleg private PDBs!
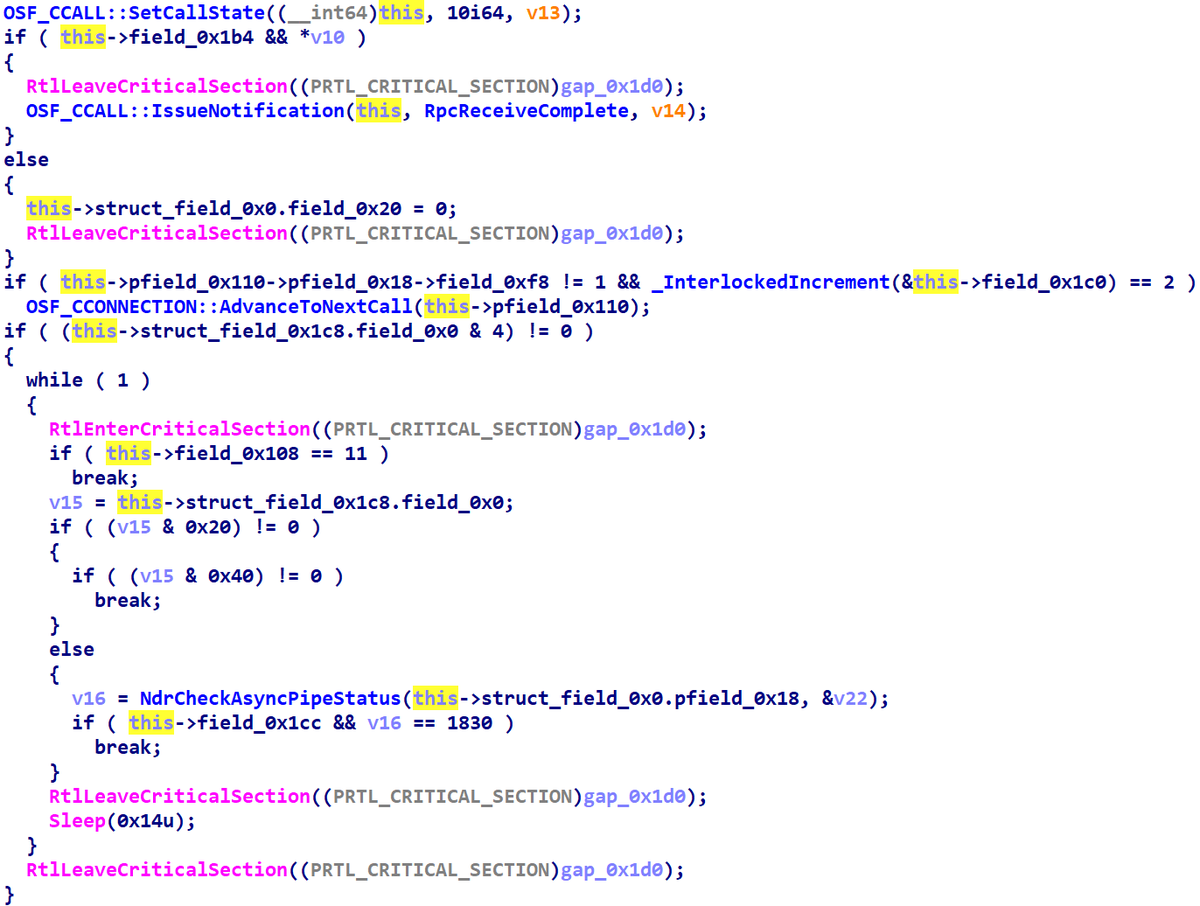
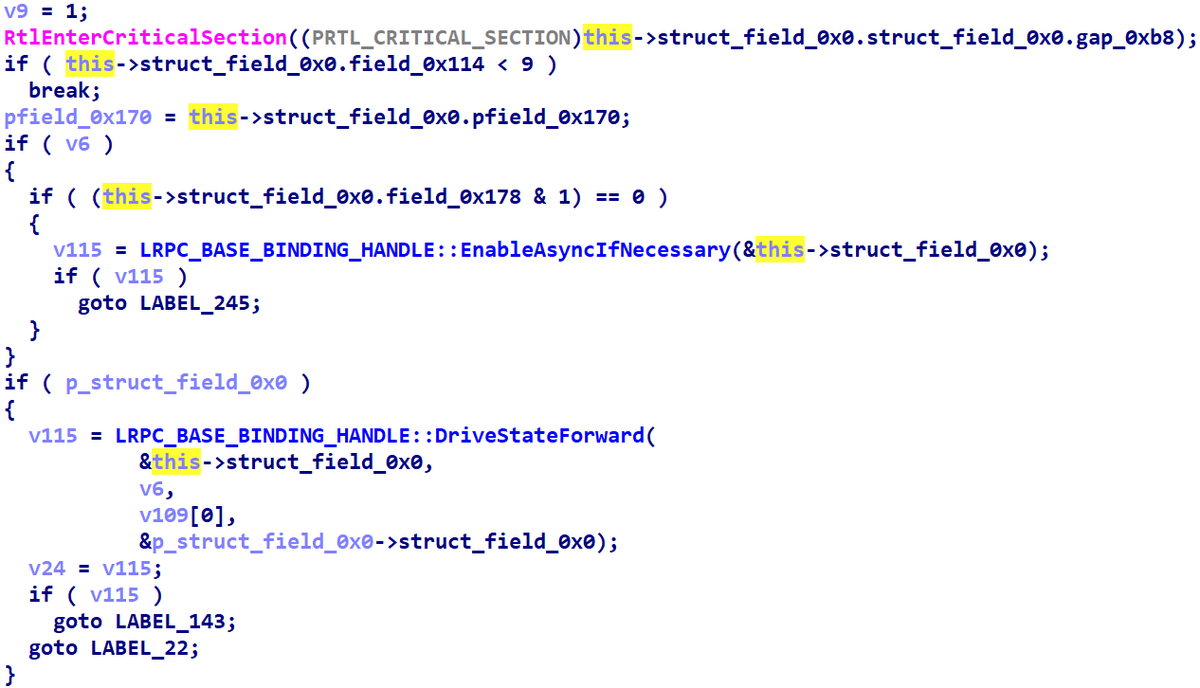
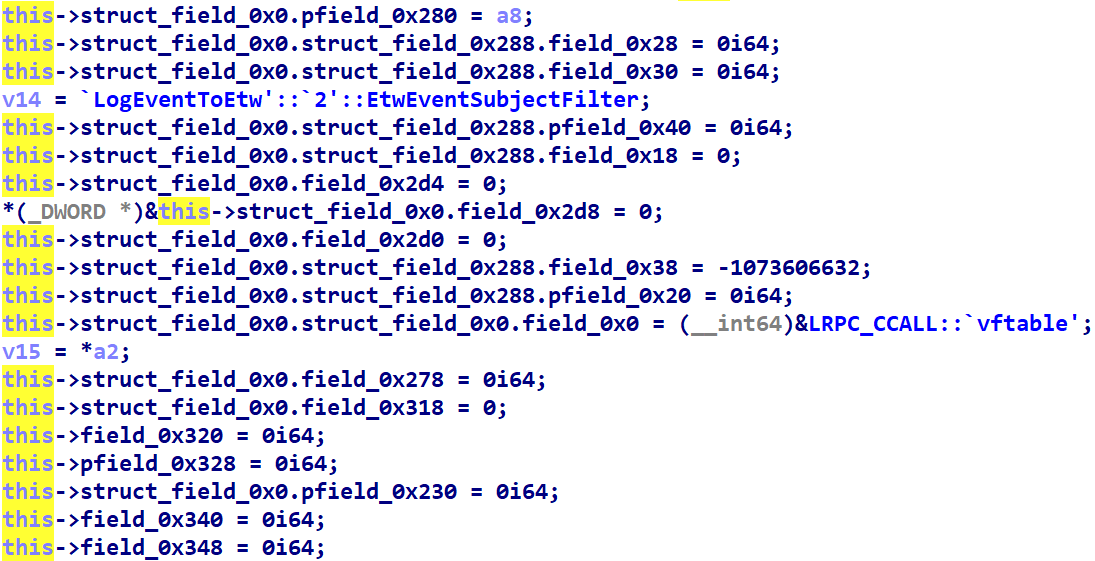
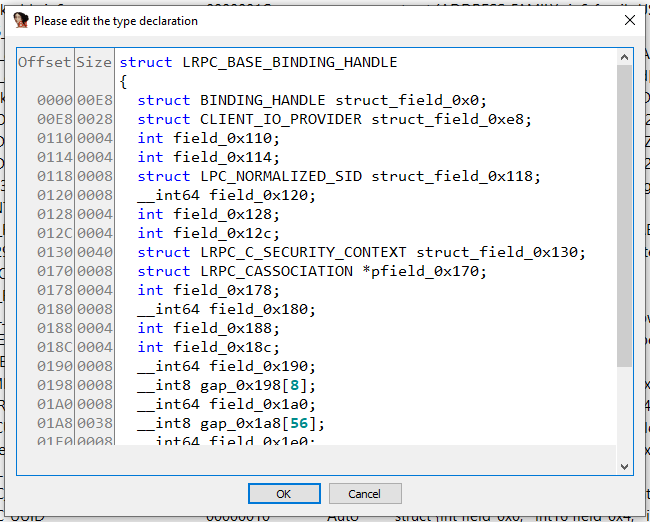
Been experimenting with Hex-Rays API today and wrote a plugin that simplifies NT Kernel decompilation. So far it can remove instrumentation, lift dynrelocs and RSB flushes. Source code and the binary are below, let me know if you have any feedback! github.com/can1357/NtRays



So can we get an explanation? PH doesn't allow kernel writes at all and reads are limited to binary images. Or is "responsible disclosure" something that only applies to Microsoft where they get to hound people like @0xAmit on LinkedIn after they mention a bug known for 4 years?
United States Trends
- 1. Jon Jones 224 B posts
- 2. Jon Jones 224 B posts
- 3. #UFC309 328 B posts
- 4. Chandler 91,5 B posts
- 5. Good Sunday 51,2 B posts
- 6. Aspinall 26,2 B posts
- 7. #Jays_Neighborhood 2.045 posts
- 8. Oliveira 75,9 B posts
- 9. Kansas 24,2 B posts
- 10. Mike Johnson 48,4 B posts
- 11. Alec Baldwin 9.558 posts
- 12. #discorddown 7.365 posts
- 13. #ปิ่นภักดิ์ตอนจบ 1,34 Mn posts
- 14. Pereira 12,9 B posts
- 15. THE LOYAL PIN FINAL EP 1,21 Mn posts
- 16. Bo Nickal 9.418 posts
- 17. ARod 2.215 posts
- 18. Dana 266 B posts
- 19. Do Bronx 12,1 B posts
- 20. Mayu 18,5 B posts
Who to follow
-
 namazso
namazso
@namazso -
 Duncan Ogilvie 🍍
Duncan Ogilvie 🍍
@mrexodia -
 Aidan Khoury
Aidan Khoury
@aidankhoury -
 vmcall
vmcall
@vm_call -
 IDontCode
IDontCode
@_xeroxz -
 HyperDbg
HyperDbg
@HyperDbg -
 Daax
Daax
@daaximus -
 Andrea Allievi
Andrea Allievi
@aall86 -
 Connor McGarr
Connor McGarr
@33y0re -
 iPower
iPower
@iPowerPower -
 Sinaei
Sinaei
@Intel80x86 -
 Satoshi Tanda
Satoshi Tanda
@standa_t -
 Petr Beneš
Petr Beneš
@PetrBenes -
 Can Bölük
Can Bölük
@_can1357 -
 Adam Niezabitowski
Adam Niezabitowski
@_0xnobody_
Something went wrong.
Something went wrong.



































































































