Similar User

@0x_shaq

@patch1t

@pwningsystems

@infosecb

@tsunek0h

@terrynini38514

@zyn3rgy

@danrevah

@K3vinLuSec

@gergely_kalman

@CodeColorist

@yo_yo_yo_jbo

@NexusFuzzy

@malwarezoo

@PartyD0lphin
Last month, I completed a practical training course at CYBERSEC on how to hunt threat with sigma rules. "Lumos! Illuminate the dark hacker attack trail use Sigma rules to enhance threat hunting capabilities" speakerdeck.com/will03/lumos-i… Lab materials are provided below. #SIGMA
As promised, I just dropped a dozen new sandbox escape vulnerabilities at #POC2024 If you missed the talk, here is the blog post: jhftss.github.io/A-New-Era-of-m… Slides: github.com/jhftss/jhftss.… Enjoy and find your own bugs 😎
Actually, 15+ new sandbox escape vulnerabilities discovered. All of them are simple logic issues. You may find your own sandbox 0-days by yourself after listening to this talk!🔥🔥🔥
Finding #TeamViewer 0days Part 1 - The story begins pgj11.com/posts/Finding-… Part 2 - Reversing the Authentication Protocol pgj11.com/posts/Finding-… Part 3 - Putting it all together. PARTY TIME pgj11.com/posts/Finding-…
NEW 🥫🍝 ya’ll!!! iOS 18.0 / macOS 15.0 xnu github.com/apple-oss-dist… dyld github.com/apple-oss-dist… Security github.com/apple-oss-dist… objc github.com/apple-oss-dist…
I've published a new blog post detailing how to write an iOS kernel exploit for PhysPuppet from scratch. Enjoy! alfiecg.uk/2024/09/24/Ker…
I finished the promised article about System Integrity Protection #SIP, which introduces the #Apple idea of #rootless on #macOS. The article is for anyone interested in: #Programming #Re #Cybersecurity karol-mazurek.medium.com/system-integri… Enjoy reading!
Latest awesome-detection-engineering addition: DEBMM - Elastic's qualitative and quantitative approach to measuring threat detection program maturity. elastic.co/security-labs/… github.com/infosecB/aweso…
Hooking Objective C code is pretty straightforward

Wow! Microsoft Recall reviews! "⭐️⭐️⭐️⭐️⭐️, it helped our customers get more and faster" - Redline stealer "⭐️⭐️⭐️⭐️⭐️, helped us optimize our code base. Love it!" - Formbook stealer "⭐️⭐️⭐️⭐️⭐️, so easy to use! Required no work to get information" - Rhadamanthys stealer

1/4: We've discovered a fully undetectable #stealer targeting #macOS. It has maintained a zero-detection rate on VirusTotal since its first submission on 17/05/2024. This stealer is allegedly linked to Rodrigo4, a known Russian-speaking threat actor from XSS underground forums.


C’mon Apple, iOS kernel vulnerability is not eligible for bounty? What would then be? It could have been ended up in @DonnchaC or @jsrailton blogs. 🤦♂️
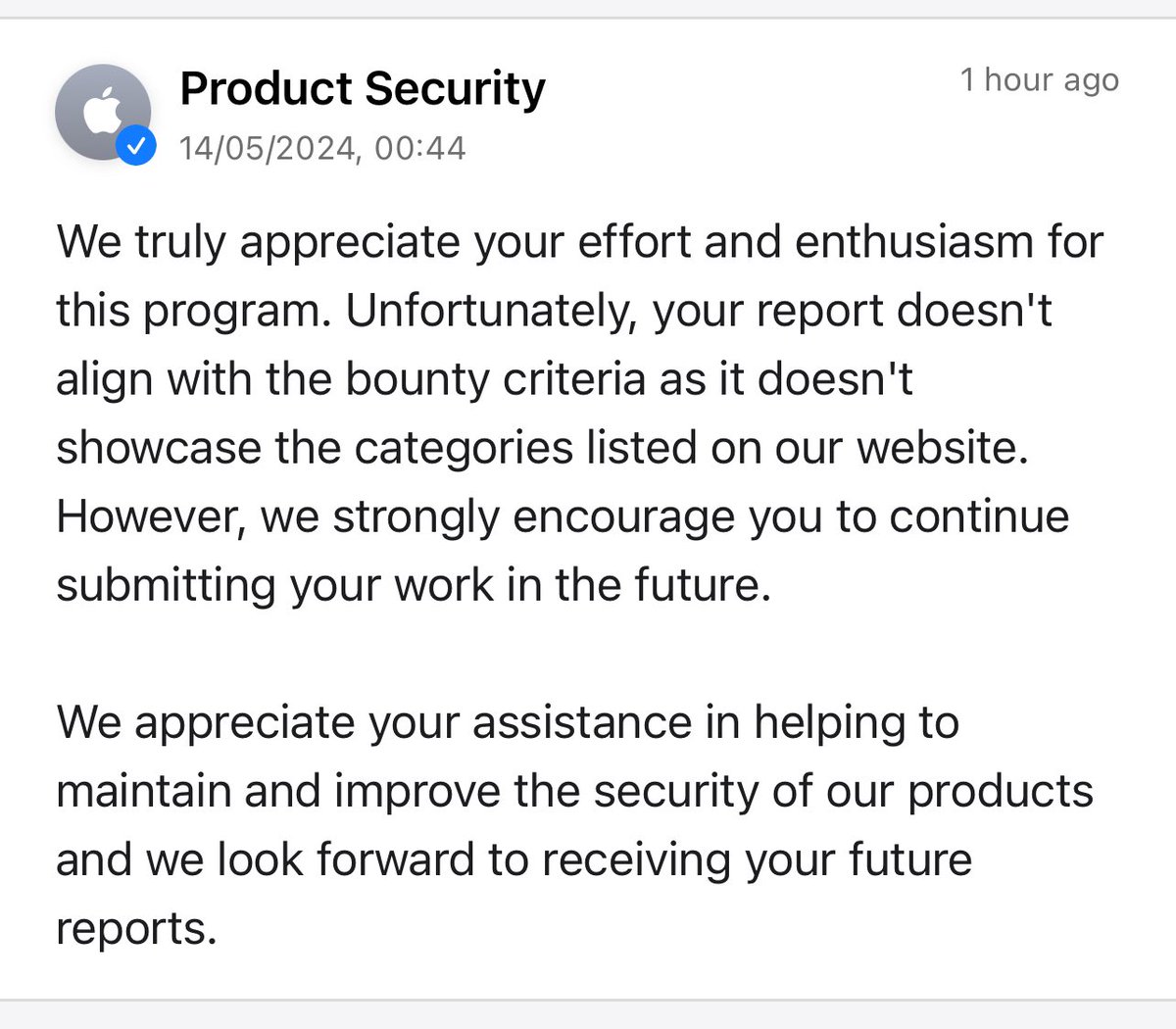
I reported CVE-2024-27804, an iOS/macOS kernel vulnerability that leads to the execution of arbitrary code with kernel privileges. Will publish the POC soon. support.apple.com/en-gb/HT214101
DYLD_INSERT_LIBRARIES still works !!!
CVE-2024-34456: Trend Micro Antivirus One Dylib Injection syrion.me/CVE-2024-34456… #applesecurity #macossecurity #macosredteam
Hey @windscribecom congrats on 69M customers! Here's a 0day LPE in your shitware: gergelykalman.com/why-you-should… (I posted this twice as Windscribe doesn't even own @windscribe :D)

We published our blog post "Bringing process injection into view(s): exploiting all macOS apps using nib files", about a process injection vulnerability in macOS. It's a follow up to our insecure deserialization in saved application state research. sector7.computest.nl/post/2024-04-b…
🚨📢 Insomni'hack 2024 🛡️[SPEAKER] Patch Different on *OS by John McIntosh 👉 Don’t miss the opportunity to attend this conference! Details and registration: ow.ly/X28F50R11Fy #INSO24 #Insomnihack #CyberSecurity

iVerify (@IsMyPhoneHacked) released the industry's only commercial tool capable of detecting Pegasus and other advanced iOS malware today: iverify.io/post/introduci…


Full Disclosure time: Here's a quick LPE for macOS that affects you if you have Homebrew installed under /usr/local (Intel macs or Apple Silicon with Game Porting Toolkit) github.com/gergelykalman/… You have to wait for periodic.daily to run, but that's a small price to pay
xpcroleaccountd Root Privilege Escalation: jhftss.github.io/CVE-2023-42942…
🔺New on the Apple Security Research blog: introducing PQ3, a groundbreaking post-quantum cryptographic protocol for iMessage. To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world. security.apple.com/blog/imessage-…
🚨 Please check our in-depth analysis report regarding #RustDoor, a macOS #malware disguised as VisualStudio update. 🕵️♂️ Further dig reveals Windows version, dubbed #GateDoor—coded in Golang. Stay vigilant! #Cybersecurity #ThreatIntel #S2W medium.com/s2wblog/rustdo…
The #GoldDigger family grows: Group-IB's TI Unit finds GoldPickaxe.iOS, the first #iOS #Trojan harvesting #FacialRecognition data for unauthorized bank access, targeting #APAC. It is linked to the GoldDigger family discovered last October. Learn more: bit.ly/3UHDaAq

United States Trends
- 1. Good Monday 35,4 B posts
- 2. #MorningJoe N/A
- 3. #MondayMotivation 12,1 B posts
- 4. Bengals 82,6 B posts
- 5. #MondayVibes 1.965 posts
- 6. Chargers 71,7 B posts
- 7. #MondayMood 1.504 posts
- 8. Victory Monday N/A
- 9. #Wordle1248 N/A
- 10. WWIII 196 B posts
- 11. 60 Minutes 38,2 B posts
- 12. McPherson 12,7 B posts
- 13. Herbert 36,4 B posts
- 14. Joe Burrow 22,9 B posts
- 15. Myron 12,8 B posts
- 16. Margaret Thatcher 5.579 posts
- 17. TAEYEON 58,9 B posts
- 18. Scotty 10,7 B posts
- 19. Brendan Carr 15,2 B posts
- 20. Ahna 3.262 posts
Who to follow
-
 faulty *ptrrr
faulty *ptrrr
@0x_shaq -
 Mickey Jin
Mickey Jin
@patch1t -
 Jordy Zomer
Jordy Zomer
@pwningsystems -
 Brendan Chamberlain
Brendan Chamberlain
@infosecb -
 tsunekoh
tsunekoh
@tsunek0h -
 NiNi
NiNi
@terrynini38514 -
 Nick Powers
Nick Powers
@zyn3rgy -
 Dan Revah
Dan Revah
@danrevah -
 KevinLu
KevinLu
@K3vinLuSec -
 Gergely Kalman
Gergely Kalman
@gergely_kalman -
 [email protected]
[email protected]
@CodeColorist -
 Jonathan Bar Or (JBO) 🇮🇱🇺🇸🇺🇦🎗️
Jonathan Bar Or (JBO) 🇮🇱🇺🇸🇺🇦🎗️
@yo_yo_yo_jbo -
 NexusFuzzy 💩
NexusFuzzy 💩
@NexusFuzzy -
 Ferdous Saljooki
Ferdous Saljooki
@malwarezoo -
 Brandon Dalton
Brandon Dalton
@PartyD0lphin
Something went wrong.
Something went wrong.










































































































