Maya
@IRMeetsSecurityCTI Analyst | Threat Intel Analyst @KC7Cyber | Interested in Geopolitics, Influence Operations and Cybercrime. #DigitalSherlock #BlacksInCybersecurity
Similar User

@Mar_Pich

@james_w_luke

@SaltyWikoff

@rfackroyd

@In0de_16

@bestriv2

@Casey9461

@Ususamah2nd

@Danthefan22

@2RunJack2

@beenimmanuel

@Kaiioju

@marius_benthin

@RogerMorales__

@W4KRN
🚨 New Lazarus Analysis Video! 🚨 Just dropped a deep dive into Group-IB's latest on Lazarus Group's stealthy tactics! 🎥 🔗 Watch the full breakdown and learn how to defend against these threats ➡️ youtu.be/eKyhMvC8sEE #CyberSecurity #APT #Lazarus #ThreatIntel #CTI #TA444…
🚨 Exciting news TLP R3D has a YouTube Channel! 🚨 Check out my new channel where I break down the latest CTI insights and show beginners how to pivot using Shodan, FoFA and VT to uncover hidden threats. 🔍💻 Dive into my analysis of BlueNoroff and more!…

Tomorrow I'm going to publish a podcast episode which has nothing to do with politics. Surely you can't have an appetite for more politics. Don't stuff yourself. Take a walk and zone out with me for a bit.
🇨🇳 A new report from Microsoft on the #Quad7 botnet, which the #TDR team studied in depth over the summer, along with two public reports available on blog.sekoia.io. Thanks for the quote!
Microsoft has observed intrusion activity targeting and successfully stealing credentials from multiple Microsoft customers that is enabled by highly evasive password spray attacks. msft.it/6016Wuqcr
Imagine a ruthless war criminal and dictator brazenly meddling in the most anticipated election in the free world, openly backing one side. Multiple intelligence agencies exposed the interference, again and again—yet the campaign benefiting from this dark alliance stayed silent.
2024-10-28 #Phishing alert: We’re tracking malicious infrastructure hosting domains mimicking popular cybersecurity vendors and VPNs. Active domains now return error messages, and we continue searching for new domains from this campaign. More info at bit.ly/48HXo1X




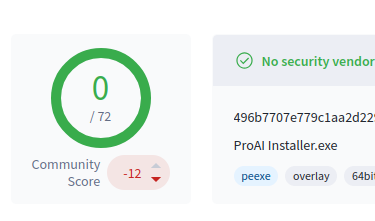
Again recommending my fun VirusTotal course on @KC7cyber: kc7cyber.com/modules/VT101 It covers basics I've not seen elsewhere to empower analysts. Example: Signed File has 0/72 score virustotal.com/gui/file/496b7… Is it benign or not? How can we quickly come to a conclusion? /1
👋 Following the positive reviews of the Ransomware Tool Matrix I shared in August, I created another. ➡️ I'm happy to share the Ransomware Vulnerability Matrix: github.com/BushidoUK/Rans… Hopefully CTI, DFIR, and TVM teams will find this useful! I shall continue to update it :)

🧵 Our threat analysts have detected recently registered domains impersonating Vietnamese government services and utilities, targeting users based in #Vietnam. The websites are spoofing the Vietnamese @GooglePlay store layouts— but clicking on the 'Install' button causes the…




⚡️ With under two weeks until Election Day, a new report out this morning from our influence operations team at @RecordedFuture: Operation Overload Impersonates Media to Influence 2024 US Election. A 🧵

Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
Russian threat actor Aqua Blizzard was observed to hand off access to compromised Ukrainian devices to the cybercriminal group Storm-0593, who then established C2 infrastructure and deployed Cobalt Strike beacons on the devices.
Likely StealC URLs on UrlScan👀 These can be found by searching URLScan for pages containing an IP (no domain), and ending in a 16 character .php file. urlscan.io/search/#page.u…


We are excited to announce the release of newest feature - Hunt SQL for threat hunting and analysis 🔐 Read more about it in our latest post! hunt.io/blog/sql
PATCH! PATCH! PATCH! 🛡️ Today, the NCSC and partners in the 🇺🇸 have issued a joint advisory containing known vulnerabilities that are being exploited by Russia’s Foreign Intelligence Service (SVR), also known as APT29 👇 ncsc.gov.uk/news/russian-f…
This is so cool. You can hunt for #FakeBat C2s with @ValidinLLC using the banner hash (37875588c49849c2fed4de1eb787de1b) I am so in love with this tool 😍

4️⃣ Create a quick visualization of any threat report to spot on the key finding in no time using mermaid with the pattern create_mermaid_visualization 📊🕘 Below is an example with this great report on LummaC2 obfuscation. 🧐 cloud.google.com/blog/topics/th…


Scraping Telegram channels and messages with Python! Making quick work of the Telethon library for at least a small showcase as to how you could monitor different channels or crawl from through new links to others 🐍 jh.live/kCDUbJU99F8

United States Trends
- 1. Bengals 80,4 B posts
- 2. Chargers 69,9 B posts
- 3. McPherson 12,3 B posts
- 4. Herbert 35,6 B posts
- 5. Joe Burrow 21,9 B posts
- 6. #BaddiesMidwest 21,7 B posts
- 7. #BoltUp 5.644 posts
- 8. Zac Taylor 4.419 posts
- 9. #ช็อตฟีลMV 135 B posts
- 10. MILKLOVE SHOT FEEL 218 B posts
- 11. #CINvsLAC 10,5 B posts
- 12. Money Mac N/A
- 13. WWIII 179 B posts
- 14. JK Dobbins 4.680 posts
- 15. #SNFonNBC N/A
- 16. 60 Minutes 32,8 B posts
- 17. Harbaugh 16,3 B posts
- 18. Ladd 5.862 posts
- 19. Scotty 10,3 B posts
- 20. Tee Higgins 3.919 posts
Who to follow
-
 Marine Pichon
Marine Pichon
@Mar_Pich -
 James Luke
James Luke
@james_w_luke -
 Allison Wikoff
Allison Wikoff
@SaltyWikoff -
 Richard Ackroyd
Richard Ackroyd
@rfackroyd -
 Will Huang
Will Huang
@In0de_16 -
 Kim
Kim
@bestriv2 -
 Danson Ray
Danson Ray
@Casey9461 -
 Ususamah
Ususamah
@Ususamah2nd -
 Dan Farrell
Dan Farrell
@Danthefan22 -
 𝓙𝓪𝓬𝓴2
𝓙𝓪𝓬𝓴2
@2RunJack2 -
 Immanuel
Immanuel
@beenimmanuel -
 🐝 Ion 🐝
🐝 Ion 🐝
@Kaiioju -
 Marius Benthin
Marius Benthin
@marius_benthin -
 Roger
Roger
@RogerMorales__ -
 Karen 73 dit-dit
Karen 73 dit-dit
@W4KRN
Something went wrong.
Something went wrong.