Richard Bethwels
@Cs_richyke#Accountant. Ethical Hacker #Cyber_Security General Computing, Networking, Hacking and Technology CHELSEA 💙.
Similar User

@mvubu_lungelo

@amady_ace

@JackmMurimi

@HitlerTheonean1

@TrazyTheInCar

@JaminOutis
Life is not for complaining about pain and sorrows, it's about prioritizing countless other reasons to be grateful for the privileges we often take for granted. #BEGRATEFULALWAYS
Unashangaa mbona hutoki soko, kumbe wewe ndio kibanda☠️☠️☠️😂
....Many types of threat actors, ranging from individual criminal hackers to organized crime rings and government agencies, carry out DDoS attacks. In certain situations -- often ones related to poor coding, missing patches or unstable systems -- ➖@TermuxForAndroid
....The flood of incoming messages, connection requests or malformed packets to the target system forces it to slow down or even crash and shut down, thereby denying service to legitimate users or systems.
❇️ What is a DDoS attack ? In a distributed denial-of-service (DDoS) attack, multiple compromised computer systems attack a target and cause a denial of service for users of the targeted resource. The target can be a server, website or other network resource.
Web App Hacking: Getting Started with OWASP-ZAP #owasp #webapphacking #vulnerability #cybersecurity hackers-arise.com/post/2016/10/1…

Demystifying the Server Side bugbountyguide.org/bug-bounty/min…



Overview of Glibc Heap Exploitation Techniques (currently up to v2.34) 0x434b.dev/overview-of-gl…
"ransomwhere: A PoC ransomware sample to test out your ransomware response strategy." #pentest #redteam #infosec github.com/hazcod/ransomw…

Introduction to the Windows Filtering Platform scorpiosoftware.net/2022/12/25/int…
DirtyCred Remastered: how to turn an UAF into Privilege Escalation @LukeGix and @kiks7_7 published two articles about exploiting CVE-2022-2602, another use-after-free in the io_uring subsystem. [1] exploiter.dev/blog/2022/CVE-… [2] blog.hacktivesecurity.com/index.php/2022…
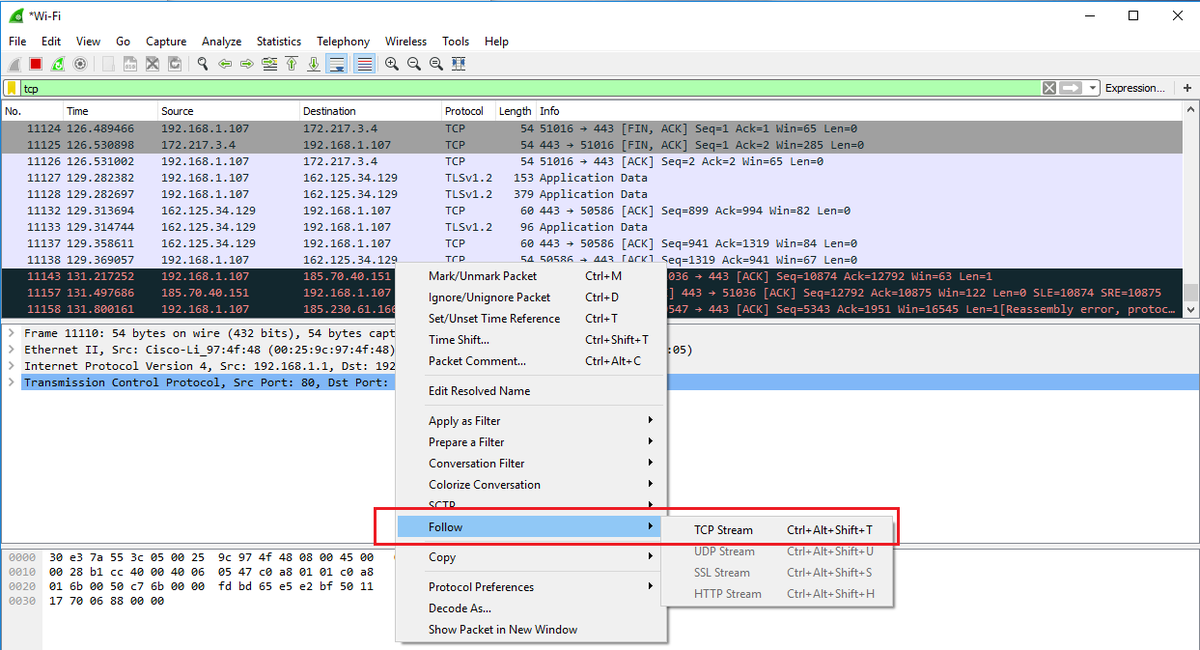
Network Forensics, Part 1: Wireshark Basics #wireshark #networkforensics #cybersecurity #cyberwarrior hackers-arise.com/post/2018/09/2…
Linux kernel exploit development series breaking-bits.gitbook.io/breaking-bits/…
APIKit:Discovery, Scan and Audit APIs Toolkit All In One. github.com/API-Security/A…
United States Trends
- 1. Mike 1,7 Mn posts
- 2. Serrano 228 B posts
- 3. #NetflixFight 66,6 B posts
- 4. Canelo 14,2 B posts
- 5. #netflixcrash 14,6 B posts
- 6. Father Time 10,4 B posts
- 7. Rosie Perez 13,5 B posts
- 8. Logan 72,1 B posts
- 9. #buffering 10,5 B posts
- 10. Shaq 14,4 B posts
- 11. #boxing 41,8 B posts
- 12. ROBBED 96,6 B posts
- 13. My Netflix 78,1 B posts
- 14. He's 58 18,5 B posts
- 15. Tori Kelly 4.782 posts
- 16. Ramos 69,4 B posts
- 17. Roy Jones 6.631 posts
- 18. Cedric 20,3 B posts
- 19. Gronk 6.290 posts
- 20. Barrios 49,9 B posts
Something went wrong.
Something went wrong.