Similar User

@Arkbird_SOLG

@ShadowChasing1

@h2jazi

@cyber__sloth

@KseProso

@ViriBack

@reecdeep

@xorhex

@fr0s7_

@cyberwar_15

@Timele9527

@neonprimetime

@WaChinYu1

@souiten

@Artilllerie
Nice change in spamming from #TA577 (aka TR aka BB) #QBot #Qakbot today 🔥 They now have the name of the spoofed company from the stolen email thread in both the display name and URL. Guess this will make some regex based rules on URLs to break.

#qbot #qakbot #quakbot is back after the traditional summer break. Right now it seems to be dropped by #Smokeloader (according to "DAS-Security Orcas" sandbox, I have no clue who they are) probably from fake installers. Botnet snow01. tria.ge/220908-lzag5ae…

I am beyond excited to drop new research today with my coauthor @cyberoverdrive on TA423/RedLadon (aka Leviathan). It’s rare for @threatinsight to partner with others but Sveva and @PwC Global Threat Intelligence Team are among the rarest talents. 1/3🧵 proofpoint.com/us/blog/threat…
Interesting wee file we found back in March, turned out to be one part of a bigger modular malware framework. This is what we know so far. I hope someone out there has the other pieces of the jigsaw puzzle. 🤔 Have a wee gander hai! #malware #Linux intezer.com/blog/research/…
Cybersecurity Has a Talent Shortage & Non-Technical People Offer a Way Out bit.ly/3yOmxaQ by @Circuitous__ @Anomali #talentgap
Possibly a #china based APT is testing their payload against Indonesia with a COVID-related lure. @Arkbird_SOLG @markus_neis Hashes: e6765333768bfd66b15b7cf91d25be09 abab41222abe98f35da3581d15618bde d1d08866b0cc889d29336c4639fa8d9c 260c9d3ff5377a25eca55e9138503ea5

#primitivebear #Gamaredon #maldoc using their standard template injection / remote template Аллах велик.rtf 9a67af06bf2f48631d0551af3bdeaf66 surname192.temp.swtest[.]ru XML 6f134f11ff456a8458319171ba8cd16a @500mk500 @h2jazi @t0001100000

#sidecopy aka #TransparentTribe #apt targeting #india using PDF lures. There are more PDF files and tar files part of the campaign. C2: email-gov-in[.]digital, mailnic[.]info IP: 162.213.255[.]21 Files: https://email-gov-in[.]digital/email.gov.in/docs/SOP-For-Range-Allotment.tar

Rishikesh Bhide, Manager of Cyber Intelligence Engineering at @Anomali will be presenting 'Wireshark Forensics Toolkit' at #BlackHatEurope #Arsenal tomorrow. Date: Wednesday, November 10, 2021 Time: 10:00 AM to 11:00 AM GMT (virtual) Track: Data Forensics/Incident Response

More potential #evlinum or just crimeware? Basic template and remote domain. It's similar to IOCs in DBAPPSecurity's report: ti.dbappsecurity.com.cn/blog/articles/… Documents.docx e726520b3ad875b516df6c3d25476444 http://wazalpne[.]com/ xml 54bcaa83d71232b1b4fa4aa47a41b3fa @t0001100000 @h2jazi


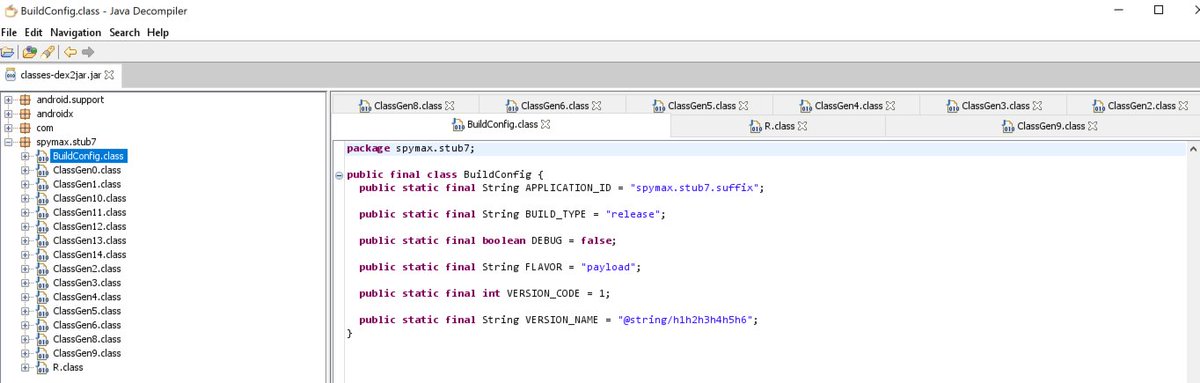
It appears to be recently discovered Snow Leopard group that monitors Pakistani users via SpyMax and AndroSpy RATs Based on the C&C, there have been more APKs with Pakistan name uploaded on VT this year Source of distribution is still 3rd party app store xinbs.net/a/xwdt/xydt/96…



#spymax #Android RAT with interesting #Pakistan-themed name. Anyone else have anything on this? /apks/Constitution_of_Pakistan_1973_v1.2.apk 6b7aaaacd33b8da0c8cb4a43d60259a0 37.221.115.62 @bl4ckh0l3z @malwrhunterteam @c3rb3ru5d3d53c @t0001100000


Wireshark is the most widely used network traffic analyzer. It is an important tool for both live traffic analysis & forensic analysis for forensic/malware analysts. Dive into Wireshark Forensics Toolkit in #BHEU Arsenal - informatech.co/2XEmn5V
🧨Inside TeamTNT’s Impressive Arsenal: A Look Into A TeamTNT Server @Anomali Source code: gist.github.com/tgould0/ anomali.com/blog/inside-te…

☣ #Groooboor (?) #malware distributed via maldocs using template injection (CVE-2017-0199), reportedly associated w/ #Gamaredon #APT 🧐 IOCs otx.alienvault.com/pulse/615cb8c1…



Looks like more potential #LazarusGroup? More #Azure and remote template but the domain 404s Z Venture Capital Presentation(Protected).docx 98e30453bbf1c9c9f48368f9bbe69edd word.azureword[.]com 104.168.162.167 @t0001100000 @h2jazi @c3rb3ru5d3d53c @ShadowChasing1


Looks like some potential #LazarusGroup? Seems to fit their crypto interests and the same #Azure lure prev-used Rapid Change of Stablecoin (Protected).docx 9be0075b9344590b3cabf61c194db180 secure.azureword[.]com/k6q3afrxddx/yoibgjjd7e/evuethwpcj/cn65qhpls2/ @t0001100000 @h2jazi

United States Trends
- 1. #OnlyKash 58,4 B posts
- 2. Starship 197 B posts
- 3. Jaguar 63,6 B posts
- 4. Sweeney 11,9 B posts
- 5. Nancy Mace 88 B posts
- 6. Medicare and Medicaid 24,6 B posts
- 7. Jim Montgomery 4.120 posts
- 8. Jose Siri 2.875 posts
- 9. $MCADE 1.356 posts
- 10. Dr. Phil 8.564 posts
- 11. Linda McMahon 3.452 posts
- 12. Monty 11,4 B posts
- 13. Dr. Mehmet Oz 7.905 posts
- 14. Stephen Vogt N/A
- 15. #LightningStrikes N/A
- 16. Bader 4.303 posts
- 17. Cenk 14,8 B posts
- 18. Lichtman 1.268 posts
- 19. Joe Douglas 12,5 B posts
- 20. $GARY 1.920 posts
Who to follow
-
 Arkbird
Arkbird
@Arkbird_SOLG -
 Shadow Chaser Group
Shadow Chaser Group
@ShadowChasing1 -
 Jazi
Jazi
@h2jazi -
 ᴘᴀʀᴛʜɪ
ᴘᴀʀᴛʜɪ
@cyber__sloth -
 Kse Proso
Kse Proso
@KseProso -
 Dee
Dee
@ViriBack -
 reecDeep
reecDeep
@reecdeep -
 avallach (@[email protected])
avallach (@[email protected])
@xorhex -
 Frost
Frost
@fr0s7_ -
 CyberWar - 싸워
CyberWar - 싸워
@cyberwar_15 -
 Timele12138
Timele12138
@Timele9527 -
 neonprimetime
neonprimetime
@neonprimetime -
 Denis Kuvshinov
Denis Kuvshinov
@WaChinYu1 -
 souiten_4t_FuYingL4b
souiten_4t_FuYingL4b
@souiten -
 Artilllerie ☣
Artilllerie ☣
@Artilllerie
Something went wrong.
Something went wrong.