Joy Savioli
@AzherothCyberwar - Countermeasures - Counter-intel from 1986
Similar User

@keld_norman

@NeURo_Olografix

@bigcountryo

@DocRoma78

@gedigi

@francescofaenzi

@p4s0

@MirchaEmanuel

@zen0
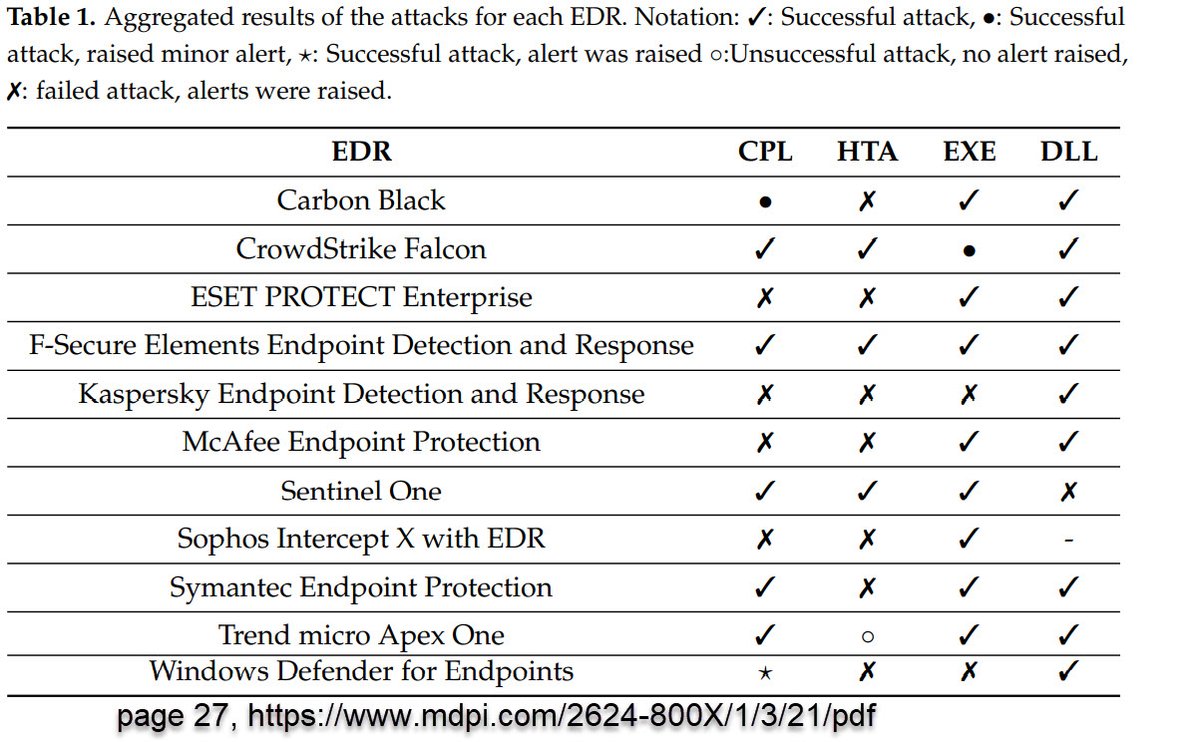
(1/2) TL;DR "DLL sideloading attack is the most successful attack as most EDRs fail to detect, let alone block, it." A scholarly and unbiased examination of how top EDR detects APT threats by @MDPIOpenAccess mdpi.com/2624-800X/1/3/…
Eisenhower: “Che si abbia il massimo della documentazione possibile, che siano registrazioni filmate, fotografie, testimonianze, perché arriverà un giorno in cui qualche idiota si alzerà e dirà che tutto questo non è mai successo”.



Windows Token Privilege to "nt authority\system" With Metasploit : meterpreter> getsystem Without Metasploit: Tokenvator.exe getsystem cmd.exe incognito.exe execute -c "NT AUTHORITY\SYSTEM" cmd.exe psexec.exe -s -i cmd.exe github.com/sailay1996/tok…
And so it begins... Intense scanning activity detected for BlueKeep RDP flaw buff.ly/2EA5YD1

Here is a shorter #BlueKeep Wireshark display filter: rdp.channelDef and rdp.name == "MS_T120"

New Repo Discovered! Name: CVE-2019-0708-PoC-Hitting-Path - Owner: digital-missiles - github.com/digital-missil…
Scranos #malware gains persistence on infected Pcs by installing a digitally-signed #rootkit driver. Researchers believe attackers obtained valid certificate fraudulently, which was issued to Yun Yu Health Management Consulting (Shanghai) Co., Ltd. and has not yet been revoked.

Besides stealing passwords and browser data, some SCRANOS payloads also interact with websites on behalf of victims — like clicking Ads, subscribing attacker-defined #YouTube channels and sending #Facebook friend requests & messages containing links to #Android malware APKs.

Can't lose the 2020 election if there is no 2020.

I am running as VP of the IEEE Computer Society to build a new open access strategy. If you care about the topic, vote/RT :-)
SMBloris; SMS Phishing; Car Hacking #podcast #security #daily i5c.us/2vk1RYK
How exposed is your IP address? Check it out using this binaryedge.io/ratemyip.html #vulnerability #scanning
What is the difference between an MSSP SOC Analyst and a True Threat Hunter? Find out in this latest article at bit.ly/2uTBDeL

Windows SMB Zero Day to Be Disclosed During DEF CON twib.in/l/bdM6Kyb48bEb via @InfoSecHotSpot

Attacking an air-gapped SCADA network via a connected coffee machine, yes a fucking #IoT coffee maker 👌💯🔥
a nice bedtime tale of a coffee machine TAKING DOWN A CHEMICAL FACTORY'S NETWORK 🤔 reddit.com/r/talesfromtec…

United States Trends
- 1. Dalton Knecht 51,5 B posts
- 2. #wednesdayfeelings 1.139 posts
- 3. Lakers 66,5 B posts
- 4. Hump Day 8.247 posts
- 5. Jaguar 137 B posts
- 6. $QUANT 16,6 B posts
- 7. Hampton Inn 2.168 posts
- 8. Jay Leno 4.851 posts
- 9. #LakeShow 6.102 posts
- 10. Linda McMahon 47,5 B posts
- 11. Dorit 5.919 posts
- 12. Spurs 17,7 B posts
- 13. #RHOBH 11,7 B posts
- 14. Carmel 3.536 posts
- 15. #WWENXT 31,1 B posts
- 16. Chase U 6.302 posts
- 17. Astrid 29,8 B posts
- 18. #chillguy 18,8 B posts
- 19. Lichtman 11,4 B posts
- 20. Honduras 49,8 B posts
Something went wrong.
Something went wrong.













































































![echo '16i[q]sa[ln0=aln100%Pln100/snlbx]sbA0D4D465452snlbxq'|dc](https://pbs.twimg.com/profile_images/1497098649561710615/QOgSFH2j.jpg)