I've created a javascript bookmarklet that will extract all endpoints (starting with /) from your current DOM and from all the all the external script sources embedded on the page. You can find it here, if you want to try it out: 0-a.nl/jsendpoints.txt #bugbountytips

تو mass دیگه باید تعداد میس دادن هارو کم کنیم این kxss یکم میس داره چون به بعضی از url ها نمیتونه درخواست بزنه تولز های شبیه اینو پیدا کن به نظرم بهتره github.com/xhzeem/reflxss
🚨 2FA Bugs by @h0tak88r 🚨 🧾 Other Resources - securitycipher.com/docs/security/… #bugbounty #bugbountytips #bugbountytip #hackerone #bugcrowd #infosec #cybersecurity #pentesting #redteam #informationsecurity #securitycipher #technology #coding #code #recon #ai #llm #owasp

كيف قدرت اكتشف ثغرة 🔴From JavaScript Analysis To UUID Pattern Exploration Revealed a Critical IDOR! مسائكم الله بالخير, عدنا بعد انقطاع لفترة طويلة بس مثل مايقولون من طول الغيبات جاب الغنايم اليوم عندنا بعض الطرق الممتعة الي استغليته مع بعض الى تحقيق ثغره ممتعة وخطيرة بس…


I've built a brand new version of my fuzzing tool Shazzer🚀 shazzer.co.uk - Easy fuzz browser behaviour - Find bugs - Share the results with the world
Right combination of web/internet archives result can give you a lot: gospider+crawley+cariddi+waymore+katana (bf/df/passive)+waybackurls+gau+gauplus+hakrawler = github.com/Dheerajmadhuka… Going to upgrade in a few hours , stay tuned ! #BugBounty #bugbountytips #DevOps #infosec
Found an IDOR with UUID but couldn't find the UUID leaked anywhere in the app? One of the alternatives is to use the Wayback machine using tools like waybackurls, but how do you search for the UUID with a huge list of URLs? 👇This tool will help you out! #BugBountyTools

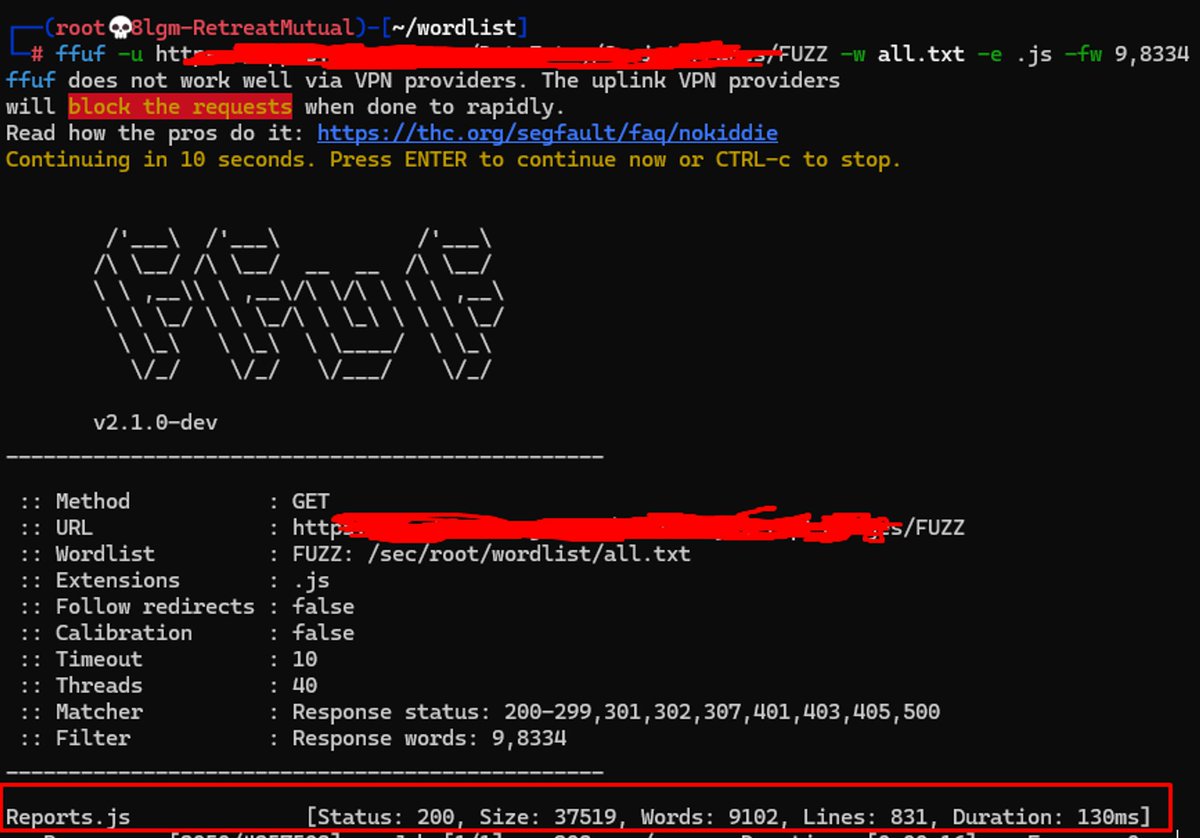
Extension is crawling in .js files and grep 1-Endpoints(with full url) just copy and open them in multipleurls ext 2-3rd urls 3-numbers 4-emails 5-JWT 6-secrets 7-indentities 8-static 9-incomplete paths


⚙️powerful tool that recursively processes JavaScript files to extract URLs and secrets using both the JSluice command-line utility and Nuclei ! 🔥 github.com/nullenc0de/gof… #bugbounty #bugbountytip #bugbountytips #ethicalhacking #hacking #infosec #pentesting #penetrationtesting…
BruteX - Automatically brute force all services running on a target. » github.com/1N3/BruteX #cybersecurity #bugbountytips #pethuraj #infosec #bugbounty
🟢Asset inventory of over 800 public bug bounty programs. Monitor over 800 companies for new assets Credit: @trick3st github.com/trickest/inven…
I happen to find an SQL vulnerability on a website today🤍. There was not a proper sanitization or escape of input data; allowing for arbitrary commands to be injected. Is high time some developers became serious🌚. Come and give me my bounty quick😂😂😂. So an attacker can…

Thank you @_Wakhoo_
Bug Bounty Methodology. 1. Subdomain Enumeration -->Assetfinder <target[.]com> -subs-only | tee -a <file.txt> -->findomain -t <target[.]com> -o -->subfinder -d <target[.]com> -->github-subdomains -d target[.]com 2. Check for live subdomains --> Use HTTPROBE/HTTPX to find alive…
🔍 Bug Bounty Tips: Crawling parameters with Katana for quick XSS/SQLI wins! 🚀 When it comes to efficient bug hunting, active crawling can be a game-changer. One of the tools I rely on is Katana, which helps retrieve URLs and parameters for thorough testing against XSS, SQLI,…

Quick update: Just updated the old template. Filter reflected values on the path as well, in the most advanced way. Template folder github.com/karkis3c/cves/… Tip: cat nuclei_output.txt | grep -v '\:plaintext' Post x.com/kaks3c/status/… #bugbountytips #bugbounty
Stop using one-liner cmd to filter reflected parameters in get req. Use this advanced nuclei-template: raw.githubusercontent.com/karkis3c/cves/… cat endpoints.txt | nuclei -duc -t reflected-value-query.yaml -fuzz This is recommended. #xss #bugbountytips #bugbounty #pentest
United States Trends
- 1. Mike 1,79 Mn posts
- 2. Serrano 236 B posts
- 3. #NetflixFight 70,2 B posts
- 4. Canelo 15,9 B posts
- 5. #netflixcrash 15,3 B posts
- 6. Father Time 10,7 B posts
- 7. Logan 76,7 B posts
- 8. Rosie Perez 14,6 B posts
- 9. He's 58 23,5 B posts
- 10. Boxing 289 B posts
- 11. Shaq 15,7 B posts
- 12. #buffering 10,7 B posts
- 13. ROBBED 101 B posts
- 14. My Netflix 81,9 B posts
- 15. Roy Jones 7.066 posts
- 16. Ramos 70,1 B posts
- 17. Tori Kelly 5.077 posts
- 18. Cedric 21,5 B posts
- 19. Gronk 6.541 posts
- 20. Christmas Day 15,5 B posts
Something went wrong.
Something went wrong.